The 5 types of risk assessment include:
- Quantitative Risk Assessment
- Qualitative Risk Assessment
- Generic Risk Assessment
- Site-Specific Risk Assessment
- Dynamic Risk Assessment
Without robust safeguards, vulnerabilities in your systems could jeopardize sensitive company data, customer information, and even your reputation. 61% of organizations reported a third-party data breach or incident in the last year.
That's where IT risk assessment comes in. By identifying potential threats and vulnerabilities, businesses can take proactive measures (instead of reactive) to protect their assets and ensure smooth operations.
However, for startups and newly formed businesses, IT risk assessment may seem like an overwhelming or unfamiliar concept. It's not just about compliance; it's a vital tool for safeguarding your operations in an increasingly digital world.
In essence, IT Risk Assessment is a critical component of IT Risk Management, involving the identification, evaluation, and mitigation of risks that could potentially impact a business's information technology systems.
IT Risk Assessment is the first step of IT Risk Management, and by analyzing these risks during the 'assessment' stage, organizations can identify controls that can reduce and mitigate these risks altogether.
Implementing these strategies also helps mitigate vulnerabilities, protect valuable assets, and ensure business continuity in the event of a system failure or a targeted cyber attack.
IT risk assessment involves a series of concepts, including what risk management is, what IT risk includes, and the common IT Risk Management Framework.
Risk Management is the process of identifying, assessing, and controlling threats to an organization's capital and earnings. Risk management in IT is a component of risk management specifically focused on risks related to information technology.
Common IT risks include:
To help streamline the IT risk assessment procedure, there are multiple IT Risk Management Frameworks organizations can refer to and utilize to standardize their strategy, such as NIST Risk Management Framework (RMF), ISO 27001, and COBIT. These frameworks provide structured steps for assessing and managing IT risks.
Before conducting an IT risk assessment, you may want to learn about the IT risk assessment methodologies. There are two main IT Risk Assessment methodologies organizations typically rely on: Quantitative IT Risk Assessment and Qualitative Risk Assessment.
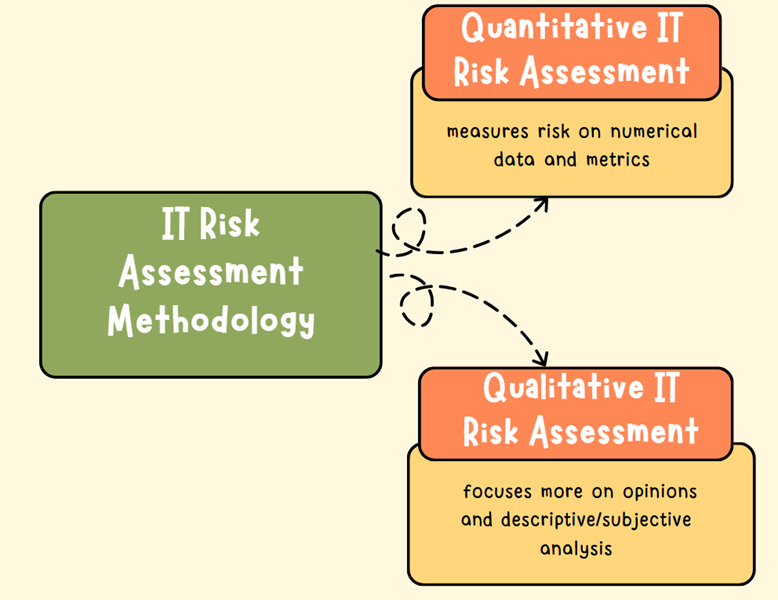
Quantitative IT Risk Assessment primarily measures risk on numerical data and metrics.
In particular, the methodology takes into account monetary values to potential losses, giving you a clear indication of expected losses associated with specified risks and can be useful for cost-benefit analyses.
These are some of the key determiners and aspects of a Quantitative Risk Assessment:
1. Risk Measured in Financial Terms: Helps estimate the potential financial impact of identified risks. For example, financial loss from a ransomware attack, factoring costs from downtime, data recovery, and brand reputation damage.
2. Probability Estimation: Utilizes statistical data and historical information to calculate the likelihood of risks occurring. However, only effective if there is 'good' data and history to refer to.
3. Decision-Making Based on ROI: Helps determine the cost-effectiveness of implementing specific controls based on the risk level. High likelihood of occurring + high cost = high risk vs. low likelihood of occurring + low cost = low risk.
In contrast, a Qualitative Risk Assessment focuses more on 'opinions' and descriptive or subjective analysis. This relies on your organization's perceptiveness and judgment to categorize risks based on likelihood and potential impact, often using risk matrices or heat maps.
These are some of the key determiners and aspects of a Qualitative Risk Assessment:
1. Focus on Expertise: Qualitative assessments rely on expert judgment, interviews, and discussion to identify potential risks instead of hard metrics.
2. Simplified Categorization: Oftimes classifies risks as low, medium, or high based on the severity and probability of specific risks.
3. Flexible & Timely: More 'flexible' and can be used even when precise data is unavailable or if you need to identify potential risks quickly.
While you could technically rely on just one or the other methodology, the best course of action is to regularly utilize both to identify all possible threats.
This part shares the guide to conduct an IT risk assessment. There are eight steps for IT risk management process in total:
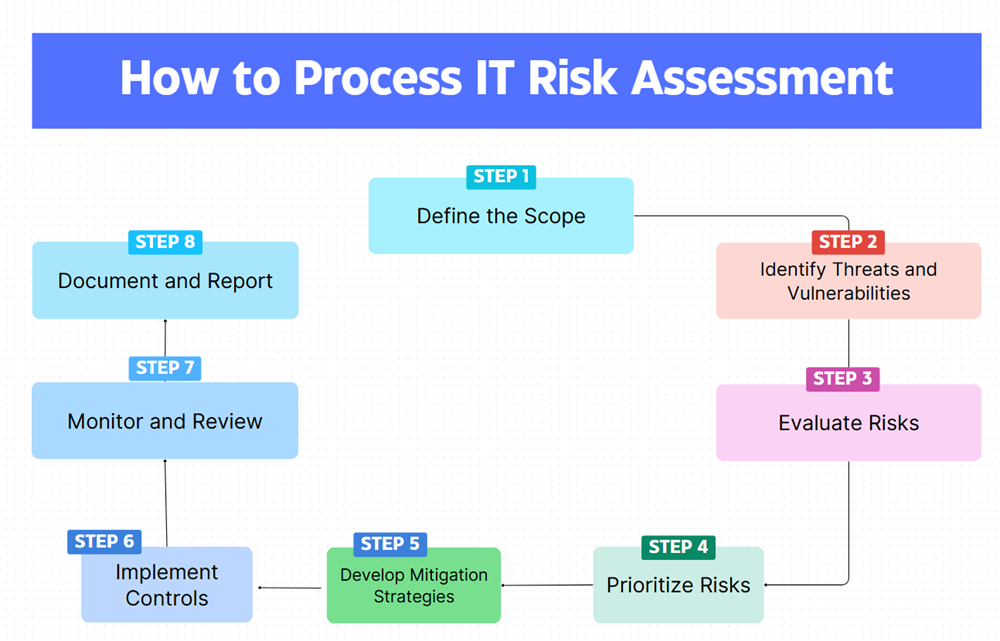
The first step in an IT risk assessment is to 'define the scope'. Organizations should identify the assets that need to be assessed and determine the boundaries of the assessment.
Your 'assets' in this case could include:
Then, identify the 'boundaries' of what is included and excluded for the assessment, such as which systems are included for the assessment, the time frame, or specific workflows/business processes.
Doing this step helps to ensure the assessment is focused on critical areas of the organization's goals while saving time and resources from 'assessing' unnecessary areas of your IT infrastructure.
Once you've outlined which assets to include in the assessments, identify potential threats and vulnerabilities that could impact them within the defined scope.
Threats could include both external and internal risks such as:
Alternatively, you also need to consider the potential vulnerabilities in the existing IT infrastructure:
By identifying and understanding potential threats and vulnerabilities, organizations can map out potential risk scenarios and rank priority areas that require immediate attention.
Once you've identified potential threats and vulnerabilities, you need to evaluate the risks. Here are some key components to consider:
1. Threat: The nature and characteristics of the risk source. This could be a specific type of cyberattack or situation like insider leaks.
2. Vulnerability: How 'vulnerable' or susceptible the asset is to the identified threat.
3. Impact: Evaluate the potential damage and disruption should the risk occur. This could include financial loss, damage to brand reputation, and possibly legal penalties.
4. Probability: Lastly, evaluate the likelihood of the threat occurring. You can base this on industry trends and standards, historical data, and expert judgment.
In this case, the usual step is to utilize either the qualitative/quantitative methodology to assess risk levels to categorize low, medium, and high-priority risks.
The next step is to prioritize the identified threats by the severity of their impact and the likelihood of it happening to allocate resources more effectively.
High-priority risks are critical risks to your IT infrastructure that also have a high likelihood of occurrence. These should be your top priority that needs to be addressed.
Low-priority risks have either a low probability, a minor impact, or can be solved relatively easily. These can be monitored and addressed as the issue pops up.
Utilize risk matrices and heat maps to visualize your risk priorities. The matrix allows the mapping of likelihood and severity to then determine what the overall rating of the specific hazard is. While there is no set format for how this matrix can look, the general form is something like this, with likelihood on one axis and severity on the other.
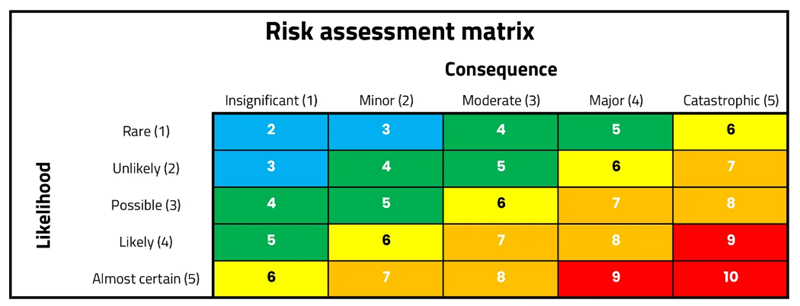
Image from Height Safety Engineers
Each step on each axis can be given a numerical value which, when added together, can be used to place the hazard within a particular response band.
With your list of prioritized risks, you'll need to develop mitigation strategies to either accept, transfer, mitigate, or avoid the threat entirely.
Choosing to 'accept' the risk typically means you've evaluated that the impact of the risk is minimal and the organization is willing to 'accept' any losses.
Transferring the 'risk' typically involves using insurance or 'transferring' the responsibility to a third party to cover any potential financial losses or reduce the impact of the threat on your organization.
Mitigation typically includes reinforcing safeguards against the risk with stronger access controls, for example, to limit unauthorized access.
Your last option is to practice 'avoidance' which simply discontinues any activity or system that puts your IT infrastructure at high risk.
When you've figured out your mitigation strategies, you'll need to put your strategy into action by implementing the necessary controls and safeguards.
This could take the form of installing additional firewalls and anti-virus software, conducting regular security training with employees, mandating stricter access management policies, and storing backups of your data or data recovery plans.
Effectively implementing your 'controls' reduces the organization's exposure to threats and strengthens the overall security of the IT infrastructure.
Once you've deployed your mitigation strategies and controls, you'll need to monitor and review them regularly.
With the nature of IT risks evolving with newer technologies, emerging threats, or changes to business operations, organizations need to monitor existing systems and conduct regular reviews to ensure the controls in place are still effective.
This helps detect new threats and vulnerabilities and allows the organization to update strategies that reflect current risk levels.
This could take the form of automated monitoring tools, periodic internal audits, and stakeholder feedback to ensure the assessment is relevant and actionable.
The last step is to document and report the entire risk assessment process to generate comprehensive reports for stakeholders and future reference.
This should include the identified risks and evaluation, the ideated mitigation strategies and implemented controls, and the results of the post-implementation monitoring and review.
These reports are incredibly valuable references for compliance audits, any future risk assessments and management, and the decision-making processes at the time.
A common framework provides a standardized approach to identifying, assessing, and managing risks, ensuring consistency across different departments or projects. This part introduces some common risk management frameworks for you to choose:
Widely used in the U.S. for compliance with federal regulations.
NIST RM is widely adopted by U.S. federal agencies and provides a standardized approach to managing risks while ensuring compliance with federal regulations. It follows a 7-step process to prepare, categorize, select, implement, assess, and authorize. It focuses mainly on security controls, risk assessments, and continuous monitoring to align with federal cybersecurity requirements.
A globally recognized standard for information security management.
ISO 27001 is an international and globally recognized standard to manage information security. It provides clear guidelines for establishing, implementing, maintaining, and continually improving an organization's information security management system (ISMS) to help protect sensitive data and ensure business continuity.
Focuses on aligning IT processes with business goals.
COBIT stands for 'Control Objectives for Information and Related Technologies' and prioritizes IT processes' alignment with business objectives. By managing risks and optimizing IT resources, the COBIT framework emphasizes creating value and ensuring that IT contributes to achieving business goals to balance risk management with value creation.
Empowers organizations to perform internal risk assessments.
OCTAVE stands for “Operationally Critical Threat, Asset, and Vulnerability Evaluation” and is a 'self-directed' framework that allows organizations to assess their risks, identify critical assets, and evaluate vulnerabilities internally. This allows it to be flexible and customizable to allow companies of various sizes to create tailored security strategies.
Performing regular IT risk assessments help businesses in many aspects, such as:
35% of organizations state security issues prevent them from faster cloud adoption. But after an IT risk assessment and management, organizations can improve security by identifying and mitigating risk rather than simply 'reacting' to a threat as it happens, so as to improve the security of your sensitive data and can proactively counter any unforeseen events.
An IT risk assessment also allows you to make informed decisions on your strategies. Identifying which risks need to be addressed while finding simpler, cost-effective solutions to 'low-risk' threats can be integral to maintaining a positive cost-benefit ratio.
54% of companies have a difficult time meeting regulatory standards in hybrid and multi-cloud environments, but IT risk assessments help organizations meet legal and industry requirements. Companies can avoid issues of non-compliance that typically lead to costly penalties, ensure alignment with best practices, and help build trust with both regulators and customers.
In the unfortunate event that you do encounter a 'threat', with a risk assessment that identifies and outlines the problem and has a strategy to solve it, you can continue with your daily operations without completely halting your organization's workflow and minimizing downtime.
The 5 types of risk assessment include:

Leave a Reply.