Access Points Explained: The Importance for Your Business Connectivity
In today's fast-paced digital world, understanding the basic components of a network is essential for businesses looking to optimize their connectivity and security. A key element of this infrastructure is the access point (AP). But what is access point mean? And why is it so important to business? Let’s dive in!
Part 1: What is Access Point Mean?
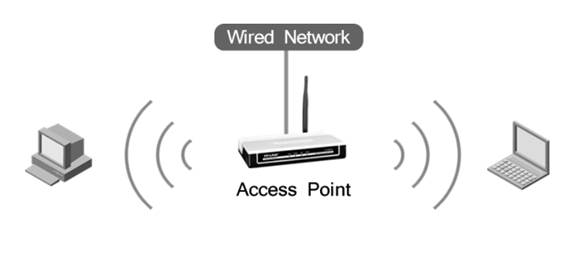
An access point is a hardware device that allows wireless devices to connect to a wired network using Wi-Fi or other standards. Essentially, it acts as a bridge between the wired network and wireless clients, enabling devices such as laptops, smartphones, and tablets to access the internet and network resources without needing physical connections.

Features of Access Point
Once you have understood what is the meaning of access point, we can move on to its features. Access points offer multiple features that significantly improve wireless connectivity and network management. Here are the 3 main features of access points.
1Provide wireless signals
The main purpose of an access point is to provide wireless signals. It plays the role of a transmitter and converts the network signals to wireless signals. This allows wireless devices like phones, laptops, etc., to connect to a network on the go.
2Connection bridge
The access point acts like a connection bridge between a wired and wireless network. This facilitates a seamless connection between wireless devices. They allow the user to expand a network’s reach without forgoing its performance.
3Network management
Access points make network management easy by allowing users to control, monitor, and optimize the performance of a wireless network. Users can easily manage multiple access points from a single location.
Part 2: How Does Access Point Work?
An access point works by integrating with the existing infrastructure of a wired network. It does this by establishing a connection to a router or wired switch with the help of an ethernet cable.
The access point then broadcasts the wireless signal which allows the devices nearby, with Wifi enabled, to connect to the wireless network.
One or multiple SSIDs are broadcasted by an access point. Every wireless network will have a unique identifier that is known as SSID. A user can select the SSID he wants to connect to a specific wireless network.
Generally, multiple access points can be seen in large corporate networks. In such a network, the APs allow seamless switches from one connection to another as they can move physically in the coverage area without ever losing the connectivity.
The encryption protocols supported by APs are WPA3 or WPA2. When you opt for advanced APs, some security features of authentication using RADIUS will also be included.
Part 3: Applications of Access Point
Access points find their use in homes, offices, as well as public spaces.
1Enterprise Environment
Having a stable internet connection in enterprises and offices is very crucial so that all the employees can have access to fast and stable internet connection wirelessly. With hybrid working in demand, access points have become very essential for collaborative workspaces.
2Home Network
If you wish to expand the wireless connectivity in your home, access points can prove to be useful. By using APs, you can ensure a strong and stable connection in every room of your home. This way, every family member of yours can connect seamlessly to the Wifi from any part of your home.
3Public Spaces
Public areas like restaurants can make use of APs to expand their wireless connectivity to more visitors. Even the public venues like shopping centers can add access points to attract remote workers to work there while also get attracted to buy something in the stores.

Part 4: Common Access Point Configurations
Huge inroads have been made to make sure that AP configuration becomes as easy as possible. A few common configurations that need to be set on APs include the following.
Security Protocol
The security protocol set, should meet all the requirements given out by the cybersecurity team of an organization for the remote home offices and facility networks. The common standard used for home and corporate APs is WPA2.
Legacy Device Support
When required, the IT professionals need to be equipped to set up their APs so that they can support legacy devices. One such scenario is when an enterprise supports BYOD but a portion of the workforce working in hybrid style may not be using the latest wireless devices.
SSID Support
To save airtime utilization, the SSID support needs to be limited to no more than 5 wireless networks while configuring remote home office and corporate office APs. This holds true for remote professionals who need an AP to work from home.
When there are many SSIDs, more airtime is consumed which in turn limits the amount of data that gets transmitted over the wireless network supported by the APs. This can affect the scalability and capacity whenever the hybrid workers meet at the office.
Part 5: Limitation of Access Point
Just like any other technology, the wireless APs have a few limitations that are mentioned below.
1Limited Coverage
AP’s coverage is actually very limited and finite. It also gets affected by physical constraints like walls or other devices connected to the same wireless network.
This would imply that strategic placement of AP is crucial, otherwise it may result in weaker signals and areas with no network coverage, especially in larger spaces. As a result, additional APs would be required for a full network coverage.
2Limited Connected Devices
Every AP can only take on a certain number of device connections. When there are too many connected devices, it can significantly overload the APs. This results in performance degradation for other users connected to the same wireless network.
When this happens in an organizational setup, slow internet connection speeds can cause delay in other work as well.
3Security Risks
In comparison to wired networks, the wireless network connections are less secure. Also, when the APs are not configured properly, security vulnerabilities increase to a great level, leading to unauthorized access which can pose a security risk to the wireless network and its data. This means that stronger AP security measures may need to be implemented.

Part 6: Best Practice to Avoid AP Security Risk - MDM
As seen from the above section, there can be a few security risks associated with APs. If you want to avoid this, the best way would be to take the assistance of mobile device management. It is a tool that several businesses use to control, monitor, and secure the wireless devices owned by the business.
MDMs work by securing the data of the company while ensuring that the wireless devices are secured and managed in the most secure way which also complies with the cyber security strategy of the company.
How Does MDM Can Help Secure Access Point
1. Password Management
Strong password policies can be set up for ensuring only the authorized users can gain access to the devices owned by the business. The password policies set up can contain input limits on password tries and the option of screen lock passwords.
2. App Blocklist
This feature lets you block certain applications from getting installed or even being used on any of the Android devices owned by the business. This keeps the device built for the purpose and also safe from malicious apps that can pose security risks.
3. Device Restrictions
Versatile limitations can be imposed on the usage of devices by the enterprise employees. You can even set a limit for functions like video and sound recording, screen capture, etc.
You can also set safety limitations on the corporate devices including safe mode, factory reset, developer mode, and USB connection. Even tethering restrictions and app limitations can be imposed like app uninstallation, permission settings, hotspot, disable bluetooth, USB and other similar connectivity features.
In Summary
In this post, we explain everything about ccess point. When it comes to modern networks in the business, access points have a crucial role to play. With their help, the connectivity of devices, mobility, and seamless network access can be greatly improved. However, to make the most of the access points, they need to be deployed and managed properly.






Leave a Reply.