Android Device Restrictions: IT Admins‘ Complete Guide
Devices are vital for employees of most businesses, yet without restrictions, they may be used for personal reasons or to breach corporate guidelines. You maintain control and compliance by setting restrictions on your organization’s Android devices.
1What Are Android Device Restrictions and Why Are They Crucial?
Android device restrictions are policies and controls that IT administrators apply to corporate-owned devices using a Mobile Device Management (MDM) solution. Their purpose is to enhance data security, ensure regulatory compliance, manage device usage, and improve employee productivity by controlling access to apps, settings, and features.
The benefits
- Device Management: Every device on the network can be monitored and controlled via a central platform.
- Data security: Device restrictions increase security and assist in protecting sensitive information.
- Compliance: Many businesses have strict compliance rules that can be breached if devices are correctly managed.
- Work Efficiency: Restricting corporate Android device users to using business-related apps only encourages more work focus.
2A Comprehensive List of Android Device Restrictions
General Device Restrictions
Four basic restrictions that most organizations need to apply are:
● Battery Restrictions: To conserve battery life, limit the number of background activities that can be running at one time.
● Restrict Calls: Prevent users from making or receiving calls, either in full or from a select list only.
● Restrict Numbers: Block outgoing/incoming calls or messages from specific numbers or locations.
● Configure Contacts: Alerts will let IT know what contacts have been added by the user to the list.
App Restrictions
App restrictions ensure that only company-approved apps are used and that only certain information is released to the app provider.
● Organization App Library: An MDM can create its own app store for users to access. This ensures that only approved and business-related apps are available for the device user to download. IT teams add apps via the upload APK function.
● Managed Google Play Store: Similar to creating its own app store, an organization’s IT team can create a managed Google Play Store. Apps are added directly from the Google Play Store, which means that only the apps that have been added can be accessed. This process only supports devices that have been enrolled through the Android Enterprise or Zero Touch method.
● Manage App Permissions: Businesses want to limit the data they provide to app developers. By managing app permissions, IT staff can decide what functions are allowed by default. That way, users can choose whether to provide access to the camera, photo albums, locations, or Google Drive.
● Install/Uninstall Apps: IT teams can set up controls to allow or disallow users from uninstalling apps or apps from unknown sources on their Android devices.
Limit Data Usage
Data usage is a concern for many business owners as it uses bandwidth and data limits.
● Overall Data Restrictions: With an MDM, IT teams receive an alert when any device exceeds a specified threshold.
● Limit App Data Usage: Set data usage limits so that IT is alerted when an app's data usage surpasses that level.
Date and Time
Using the MDM’s timezone settings, IT teams can set a device timezone or add an NTP server to ensure that all devices have the same time—this helps reduce issues caused by time differences. The team can also allow or disallow users from modifying the time and date.
Screen Capture and Display Restrictions
● Screenshot/Screen Record Restrictions: MDMs can restrict screen captures for security reasons, which blocks users from taking screenshots or recording screens.
● Screen Timeout: Timeouts might be acceptable on Android phones, but for Android kiosks that need to be functional for a set time, use the set screen feature to keep the screen awake for that period of time.
● Screen Brightness: This is also a preferred setting for Android kiosks, which sets a fixed brightness that’s best for everyone and then blocks users from adjusting it.
Connectivity Restrictions
Restrictions must be set for employees’ Android devices' connectivity options.
● USB Tethering Restrictions: Don’t let end users tether their devices by USD as this enables data sharing, which may cause overuse of their limit.
● Bluetooth Tethering: Hackers easily access an Android device via Bluetooth. By disabling Bluetooth tethering, you can prevent unauthorized connections.
● Wi-Fi Network Restrictions: Unsecure Wi-Fi networks are another way hackers can access and control which Wi-Fi network devices can connect to.
Camera
MDMs can control access to the device camera. If the organization feels that taking pictures doesn’t meet business needs for any reason, IT staff can block access to the camera, even from the lock screen.
Developer Mode Restrictions
Developer Mode on an Android device allows access to debugging options and advanced settings that could potentially destabilize the device or expose sensitive data. IT staff can disable this option via an MDM to prevent unauthorized changes. Only permitted staff can access this area.
Kiosk Mode Restrictions
Kiosks often perform one function and don’t need to run or even have multiple apps installed. Kiosk mode locks the device to a single application or a select group of approved apps, preventing access to all other applications and system settings.
An extra step can be to create a kiosk browser that blocks specific website addresses while restricting the use of the home screen and notification bar, ensuring users remain focused on the intended tasks without distractions.
3How to Choose the Best MDM for Android Restrictions
While there are many MDM (Mobile Device Management) software options available, they offer different features and functions, so selecting the one that best meets your enterprise's specific needs is crucial. Here are some important considerations:
1. Matching Needs
Every business is different, and only a few MDMs have one platform for all business needs. Ensure the software aligns with your enterprise's unique requirements, such as device types, operating systems, reporting functions, management features, and security protocols.
2. User Friendliness
Some MDMs have complicated setups, and even the user dashboard is difficult to use. Others have been designed with the end-user in mind; implementation is straightforward to allow for a swift takeup of the software. After that, it’s easy for all users to operate and get the most out of it.
3. Flexibility and Scalability
Some MDM platforms are sold “as is,” with every possible bell and whistle included. This makes it difficult for IT teams to implement as they need to turn off many features. The ideal MDM software begins with core features and has others that can be added on as the organization’s needs grow.
4. Technical Support and Service
Purchasing software shouldn’t end at the sale. Customer support is essential and needs to be provided with the following concerns in mind:
● Easily contacted
● Be friendly and approachable
● Swift and speedy response times
5. Cost-Effectiveness
MDMs range in price from low to extraordinarily high. The ideal one charges only for the number of devices and features being used, with the option to add more endpoints and functions as required. Buying a complete system with a high one-off cost may not be the most cost-effective option. Further, are there ongoing licenses, membership, updates, or support fees? These need to be factored in before a decision is made.
4How to Implement Android Restrictions with an MDM (Step-by-Step)
AirDroid Business is an MDM platform that allows IT teams to monitor every Android device in the network from one central location. They can quickly troubleshoot, update, receive alerts, and put restrictions on Android phones.
Steps to Implement Restrictions
Step 1. Log in to AirDroid Business
Step 2. Add and register devices.
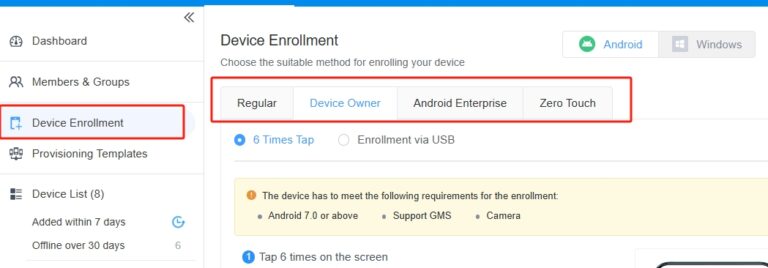
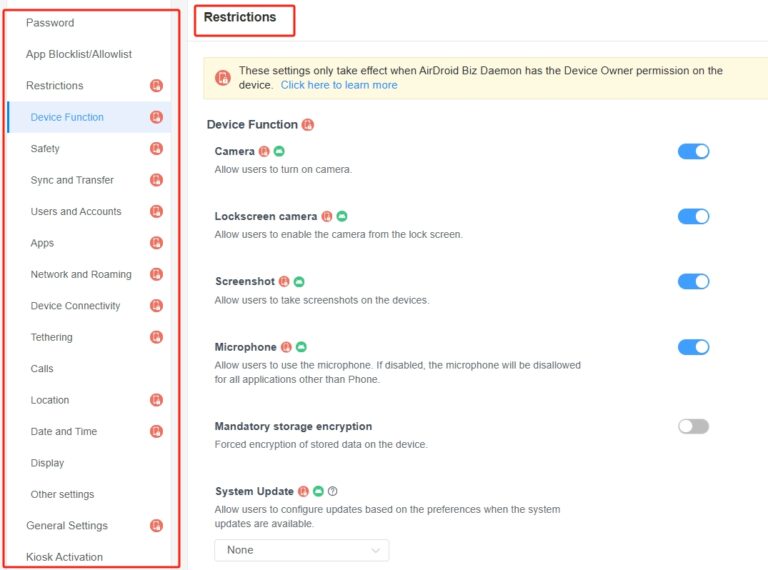
Step 3. Configure device policies and restriction settings.
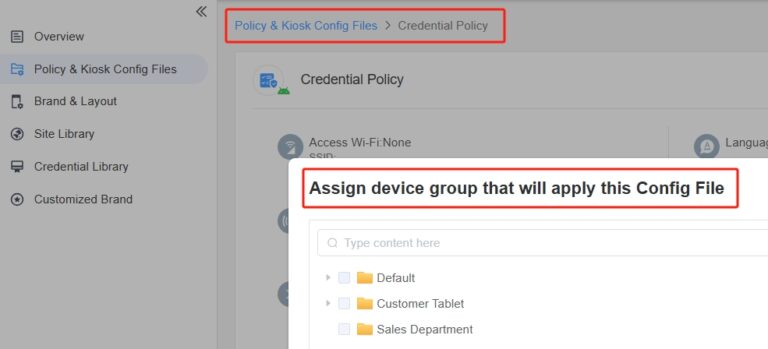
Step 4. Apply policies and monitor device status.
How to Remove or Disable Restrictions
It’s essential to understand that only IT staff can remove restrictions on Android devices with AirDroid Business; device users cannot do this themselves.
- Log in to the MDM console.
- Select the device to modify.
- Cancel or adjust restriction policies.
- Confirm changes and save.







Leave a Reply.