Operating System Vulnerabilities: Types, Examples, & Tools
Operating System (OS) vulnerabilities are one of the common loopholes used by attackers to target the operating system of digital devices, including Windows, Android, Mac, and iOS devices. Remember, the OS is the heart of digital devices meaning that its vulnerabilities can cause serious consequences, such as denial of service, data breaches, data theft, ransom, sensitive data reveal, authentication bypass, and sometimes full system compromise.
A good example is the famous 2017 WannaCry ransomware attack that targeted computers running on Windows operating systems. This particular attack encrypted and demanded ransomware in Bitcoin currency from more than 200,000 computers in over 150 different countries!
This is just the tip of the iceberg! Here is everything you should know about operating system vulnerabilities and effective solutions to help you avert risks associated with operating system vulnerabilities.

1Types and Examples of Android OS Vulnerabilities
Android OS is one of the leading yet most vulnerable operating systems running many devices across the globe. Just like other operating system vulnerabilities, Android OS vulnerabilities come from different sources and work differently to achieve their objective.
They could be facilitated by programming errors, outdated codes, and third-party interactions among others.
Android OS vulnerabilities are classified into various types based on how they attack your device’s operating system. Some of the common vulnerabilities of Android operating systems include:
1 Memory Management Vulnerabilities
These vulnerabilities involve improper handling of system memory and critical resources, which may lead to out-of-bounds access or reuse of freed memory.
Examples: CWE-125 (Out-of-bounds Read) allows attackers to read data beyond the allocated memory range, while CWE-416 (Use After Free) may cause attackers to reuse the memory area after it is released and execute malicious code.
2Injection Vulnerabilities
The primary aim of this OS vulnerability is to insert payloads into executable apps on your Android device through unvalidated user input. Often, developers fail to check the integrity of installed apps and attackers can use this loophole to inject a malicious code that replaces the original legitimate code.
Examples: The most common type of OS injection vulnerabilities includes SQL injection which uses SQL commands to modify, add, or delete records or entire databases. Others include remote code injection (CWE-94), JASON, and NoSQL.
3Privilege Escalation
This type of vulnerability targets access to higher privileges than intended by the access control and sandboxing security model in the Android OS. This flaw allows a locally authenticated attacker to have elevated privileges that could potentially cause unauthorized access and modification of certain system files.
Examples: CVE-2024-43093 allows attackers to access Android data, OBB, and sandbox directories and subdirectories.
4Unpatched Software Vulnerabilities
These are vulnerabilities that happen either because the apps running on your Android operating system are outdated or simply because they lack updated security patches to deal with the evolving cyber security threats. Attackers can compromise your Android device without your interaction.
Examples: Four vulnerabilities namely CVE-2023-24033, CVE-2023-26496, CVE-2023-26497, and CVE-2023-26498, allow attackers to compromise your Android phone remotely at the baseband level. This means the attackers can remotely and silently compromise your device.
5Zero-day Exploit Vulnerabilities
This type of vulnerability is closely related to unpatched software vulnerabilities. Often, the software vendor discovers a system vulnerability and finds a fix that will be released as security patches. However, during that period before the discovery of the vulnerability and the release of the right security patch, attackers can take advantage of the system vulnerability and attack it before the fix is rolled out. This is what is referred to as zero-day exploit vulnerability.
2How to Prevent Vulnerabilities on My Android Device?
Vulnerabilities on Android devices exist but it is worth noting that there is a lot that you can do to significantly mitigate these vulnerabilities. While there is no one-for-all fix to vulnerabilities on your Android device, here are some of the best ways to prevent Android OS vulnerabilities.
Keep Your Device Updated:
Android vendors and app developers pack back-end security fixes to new patches to make them more immune to new security threats. Therefore, updating your device and respective applications to the newest versions can massively reduce system vulnerabilities caused by patches. Check out for regular updates and download them as soon as possible to avoid zero-day exploit vulnerabilities.
Only Download Apps from Trusted Sources:
Google Play offers an array of apps and it is the official app-download platform for Android. However, certain apps might not be available and you can fetch them from third-party download sites. Unlike Google Play or trusted sources, most third-party stores don’t have rigorous app-scanning capabilities. Therefore, you could easily fetch a malware into your Android device. To avoid this, only download from trusted sources.
Be Wary of Unknown Links and Attachments:
Unknown links and attachments can be infected with malware that can cause harm to your device and data. Attackers can hide malicious files in these attachments, emails and links that redirect you to unknown websites. Avoid clicking suspicious links and attachments even if they come from someone you know.
Protect your Android Device:
One of the best ways to prevent the vulnerability of your Android device is to protect it with suitable antimalware tools. This security software helps you scan your Android device for various security threats. This saves you the time and energy of manually finding and solving potential threats to your Android device.
Pay Attention to Permissions:
When installing applications, pay attention to the permissions requested. Sometimes, because you are in a hurry, you might accept certain permission requests thus allowing apps to access some private/sensitive data in your Android.
3How to Know If There are Vulnerabilities on My Device?
Preventive measures can help you reduce risks associated with operating system vulnerabilities. However, this alone is not enough. Knowing how to detect these vulnerabilities can heavily boost your goal of addressing these vulnerabilities. Some of the practical ways to detect possible vulnerabilities on our devices include:
1. Check for security updates
The latest security updates come with the latest patches capable of fixing new security flaws on your system. You can check for new updates under the system settings section on your Android. If updates are available, consider installing the updates because your device is currently vulnerable.
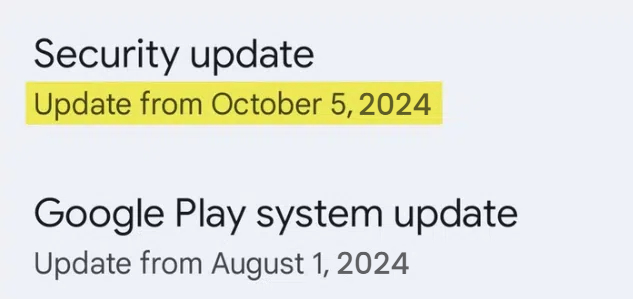
2. Check the security patch level
The security patch level represents the version of the security update your Android device has received. The security patch level number comes in a date format followed by a number. To find the security path number, simply navigate to the security update section in the settings app.
3. Detect Root Status and Developer Mode
Rooting your device and putting it in developer mode exposes your device to more Android vulnerabilities. To check whether your device has undergone rooting/jailbreaking, consider using specialized developer mode/rooting detection software.
4. Using security scanning tools
Several dedicated security scanning tools can automatically detect vulnerabilities in your device. While different security scanning tools don’t have exactly the same features, it is important to choose the one that meets your needs.
4Best Tools for Checking OS Vulnerabilities
As aforementioned, certain dedicated tools can help you automatically scan and detect potential OS vulnerabilities on your Android device. Some of the best tools include:
1 AVG Mobile Security
AVG Mobile Security is a comprehensive OS vulnerability checker for Android. This tool protects your Android device from harmful viruses and malware with the help of app lock, photo vault, Wi-Fi security scan, hack alerts, and malware security.
Furthermore, it provides you with an app permission advisor to help you manage app permissions, especially during installations. While it offers broad Android device protection, its subscriptions are pricey and you have to make it your default browser.
2Avast Security & Privacy
Avast is a popular OS vulnerability detection tool that combines the functionalities of antivirus and VPN. It gives you advanced antivirus and VPN services to ensure that your network is secure, private, and free from viruses and malware. It can scan all kinds of viruses and malware including spyware and Trojans across the web, apps, and files. However, this tool lacks spy camera options and protections against phishing and ransomware.
3ESET Mobile Security
ESET Mobile Security is another wonderful Android operating system vulnerability scanner. This tool can detect viruses, ransomware, and various other types of malware on your Android device. Additionally, you can evade phishing scams, secure your online shopping, generate security reports, and scan USB with ease. ESET Mobile Security offers a premium version with a 30-day free service and a free limited version. Although it has a clean intuitive interface it lacks URL protection and is pricey.
5Secure Android Devices with an MDM Solution
MDM solution provides the best way to manage a fleet of Android devices for an enterprise. With powerful MDM solutions like AirDroid Business, you can set up security policies and deploy them to your multiple remote devices from a single console. Additionally, you can remote control these multiple devices in an array of ways.
For instance, you can wipe data remotely, set auto factory reset, lock the phone remotely, restrict user downloads from unknown sources, set website, and apps blocklist, limit in-app browsers, and execute password management without breaking the bank. The list is long and you can selectively apply policies to different devices and edit them whenever you want to.
6Summary
In a nutshell, understanding the core of operating system vulnerabilities will always put you a step ahead in mitigating and managing them. The beauty is that there are tools that help you stay on top of your OS security. For example, you can use an MDM solution like AirDroid Business if you’re managing a fleet of mobile devices. It will give you the flexibility, convenience, and relevant features to handle your Android OS security.







Leave a Reply.