Best Practices for Password Policy in Mobile Device Management
Did you know that data breaches cost organizations, on average, around $4 million? The rising threat of cyberattacks is forcing businesses to take action. But where to start?
Passwords are the first line of defense for enterprise protection. From laptops to mobile devices, strong password policies help secure sensitive data from breaches.
We’re not just talking about alphanumeric characters. There are many parameters involved when establishing a strong password policy. Today, we’ll discuss the best practices for password policy, challenges and how to set it up.
1What Is a Password Policy?
A password policy is a set of rules enforced when creating passwords across your organization. It reduces the risk and threats of cyberattacks and data breaches. Most of the time, we only see password policies implemented when creating accounts.
However, since many companies now provide mobile devices to their employees, another entry point must be secured.
When discussing security on mobile platforms, there are many areas to consider. These areas include the security of the applications on the device itself.
Examples of these threats are:
- Downloading malicious code
- Stolen sensitive data
- Network penetration through mobile device gateway breaches
That's why password policy is important when it comes to mobile security. It can prevent threats like malicious mobile applications, data leakages, phishing scams, spyware, identity theft, and many others. A weak password can make or break your whole organization.
As an organization, you want to ensure employees are not using weak passwords because they undermine other security measures. You could have strong firewalls, powerful antivirus software, and hardened devices, but a weak password could allow an attacker access without much trouble at all.
2Password Policy Best Practices
As someone who is in charge of cybersecurity, a key weapon in your arsenal against bad passwords is policies that define what is acceptable. This password policy will set specific parameters that tell employees what makes a strong password.
If you just had a very quick policy saying, "Please set strong passwords," it could be interpreted in a few different ways. So, this policy should set some really clear parameters, which are details about what exactly you want people to do.
Here are several tips you can follow when setting up:
Password Length
Length is the first and one of the most important factors for creating a strong password.
Say, for example, you created a password by combining 12 unrelated English words (e.g., "backyard wagon hashtag Jimmy"). It creates an enormous number of possible combinations. It makes it nearly impossible to crack with current computing power.
However, it's important to note that requiring users to memorize excessively long passwords (like an 84-character password) is impractical.

Password Complexity
It’s much better to mix up your password with combinations of uppercase and lowercase letters, numbers, and symbols. The more jumbled it is, the harder it is to guess and also the harder it is to break with brute force.
A simple three-character password with only lowercase letters has 17,576 possible combinations. That’s not a lot. By adding upper case, numbers, and special characters, the number of combinations increases significantly, enhancing security.
Your organization should also prevent users from using common substitutions, such as "@" for "a" or "$" for "s." These substitutions are too predictable and should be eliminated to ensure passwords remain cryptic and secure.
Avoiding Common Associations
You should also avoid any form of association with known words, phrases, or easily guessable information ("first grandchild," "password"). Discourage users from using personal or common information that could be easily guessed by attackers.
Users tend to default to something comfortable, like their dog's name or simple sequences like "123456." Policies need to be in place to eliminate common passphrases like "password," "123456," and "qwerty."
Password Rotation
Regularly changing passwords is a practice that many forget to implement. While this may differ in frequency depending on the organization's policies, the principle remains the same. The more frequently passwords are changed, the less time an attacker has to exploit a compromised password.
Show Password Option
When users try to type in or paste a very complex password, they want to see if it’s correct. An option to make your password visible (instead of showing as asterisks) is useful for the end user.
Setting a Limit
Most of the time, by default, devices and applications put a limit on the total number of failed/incorrect attempts a user can make before it locks. You can even set up a threshold of failed attempts before the devices restart to their factory settings. This way, before a hacker can even penetrate the device, private data has been erased.
Password Reuse
One of the most dangerous things is reusing passwords between websites, applications, and devices. A breach in one area can lead to issues in another, quickly piling up.
Implement policies that prevent the reuse of old passwords, ensuring that previously compromised credentials aren’t mistakenly added.
3Common Password Policy Mistakes
Let’s briefly talk about a few potential issues with password policies. These are common mistakes that can backfire and increase the risk of a data breach:
- Excessive complexity: Overly complex passwords are difficult for employees to remember. The last thing you want is for them to write down all of their passwords or reuse them across multiple applications.
- Frequent changes: Change is good, but forcing employees to swap passwords too often leads to minor, predictable changes that are easily exploited. You’ll see changes like “password1234” turn to “password2345” instead of something unique.
- Lack of education: Make sure to educate your employees on why password policies are important and how they can best protect their credentials.
- Restrictive rules: Rules that disallow certain characters or enforce specific sequences can lead to weaker passwords simply due to user frustration.
Remember that your users are humans. Create effective, user-friendly policies that they can maintain without much headache.
4Tools To Look Out For
If your organization wants to enhance its device security, consider using an MDM solution to secure and manage these devices. This includes setup password policies and enforce data encryption. AirDroid Business does exactly that and more.
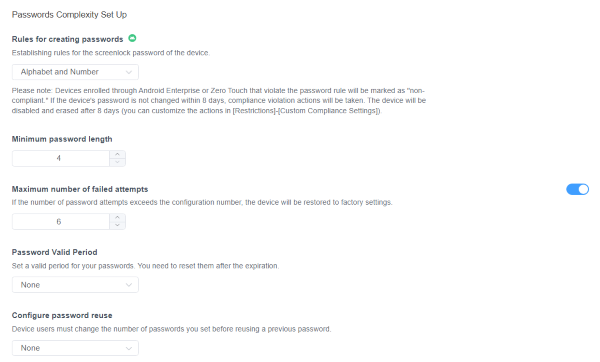
When setting up a strong Password Policy, you can:
The first option allows you to set up rules. You can choose the complexity (alphanumeric, lowercase, etc.) and the length (4-16 characters). Also, you can establish a maximum incorrect attempt before it goes to factory reset (in case of breaches).
The second option is adding a set password. This means that users can only unlock their devices using the password you configured.
Finally, the last option is password removal, the existing password will be removed remoely and users cannot set a new password.
5Conclusion
When it comes to safeguarding your data from theft or any form of cyberattack, your first shields are your passwords. Once they are compromised, it’s easier to penetrate everything.
So, it’s extremely important to set up password policies, not only on your desktop computers but also on your mobile devices. You can do that with the help of MDM tools such as AirDroid.
Consider following these tips we gave you today, but also don’t forget to strike a balance between security and practicality.






Leave a Reply.