Top Blocklist Manager for Corporate Devices in 2024
Blocklisting is a preventive measure by cyber-security that allows individuals and corporations to block suspicious, harmful, or malicious activities. It filters out harmful or unnecessary applications, websites, calls, and emails and blocks them to keep the working environment secure.
Blocklist manager helps enterprises restrict known vulnerabilities and other non-work-related content like social media to improve employees' work efficiency and device security.
1 Top Blocklist Manager for Corporate Device
A proficient blocklist manager should have essential blocking features and the capability to disable or customize device functions.
App Blocklisting
The app blocklist feature helps enterprises to block known malicious apps. After identifying commonly used non-work-related apps, admins can add and save them in the blocklist tab provided by AirDroid Business to ensure employees cannot access those apps on official devices.
- Create an App Blocklist to specify which apps can not be used on the managed devices.
- Customize the App permissions rule according to your needs, turn off certain permissions to ensure security.
- Restrict devices to a specific set of worked app and prohibit access to all others.
Steps to Configure App Blocklisting
- Log in to the admin console using your AirDroid Business account and select the ‘Policy and Kiosk’ option.
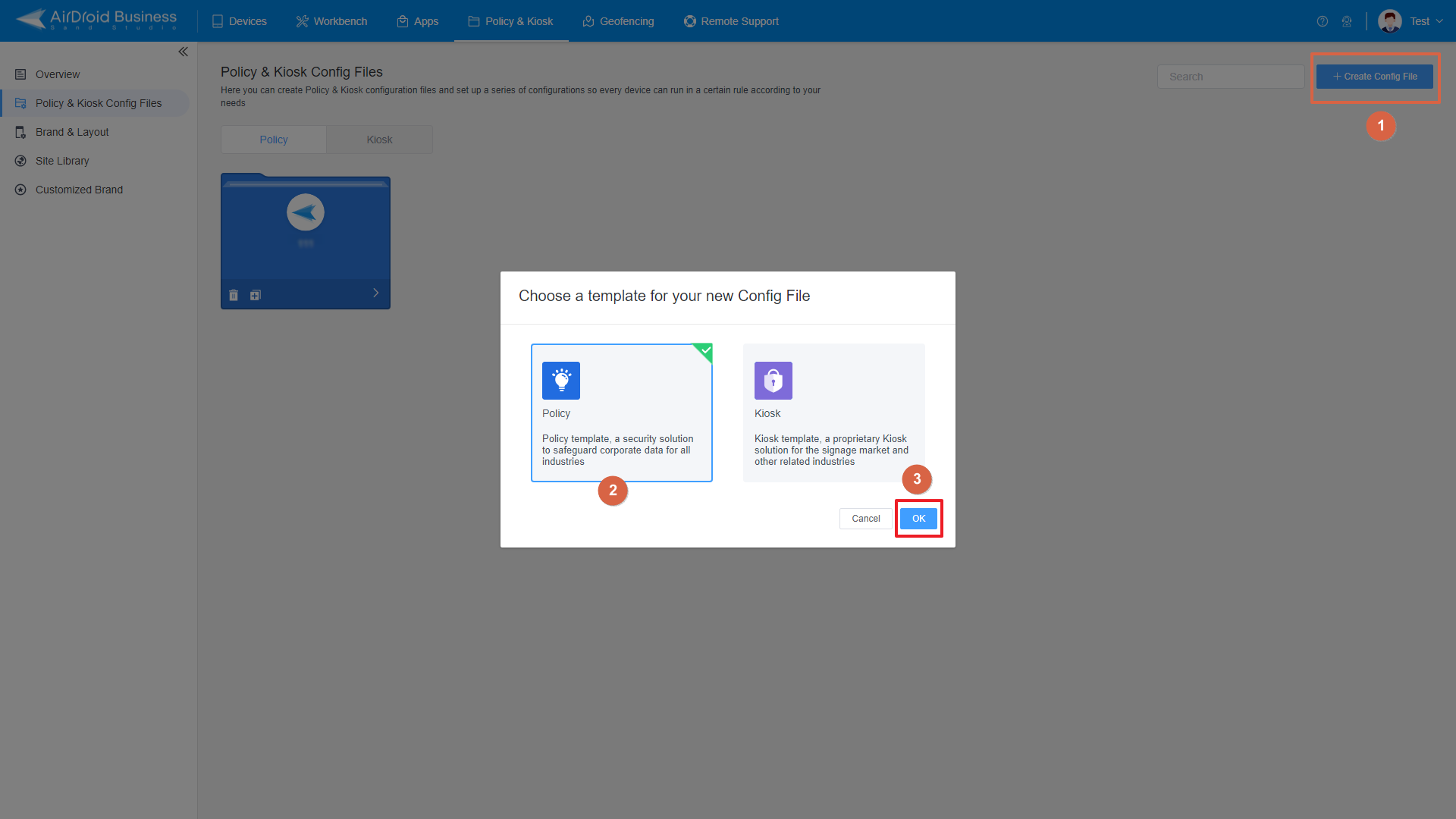
- 2. Then choose ‘Policy and Kiosk config files’ to create a new config file. Select ‘Create Config file’.
- 3. Select the 'App Blocklist' option from the left menu and add one or more apps you want to block. (You can add it by simply selecting the ‘Add app’ option).
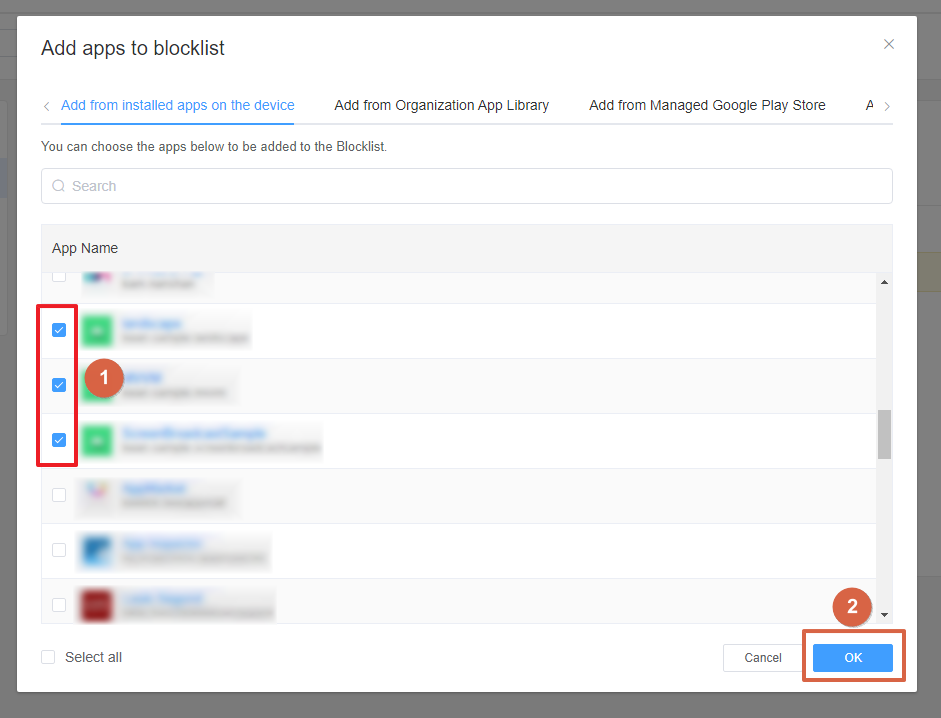
- 4. Give a name to the Config Profile and select the devices or groups you want to configure this App blocklist and save it. Now the blocked apps can't be accessed on the devices where you are applying.
Website Blocklisting
A list of websites created by business administrators to restrict harmful and redundant websites on official devices. The rate of unnecessary device usage is very high in the corporate sector. So, blocklisting is an effective way to reduce it and enhance employee productivity.
- Select a reliable browser (like Chrome, Edge, or Firefox) as the default browser on your managed devices.
- Customize the list of URLs to block access.
- Complete the 'Configuration' option to improve the browsing experience.
Steps to Configure Website Blocklisting
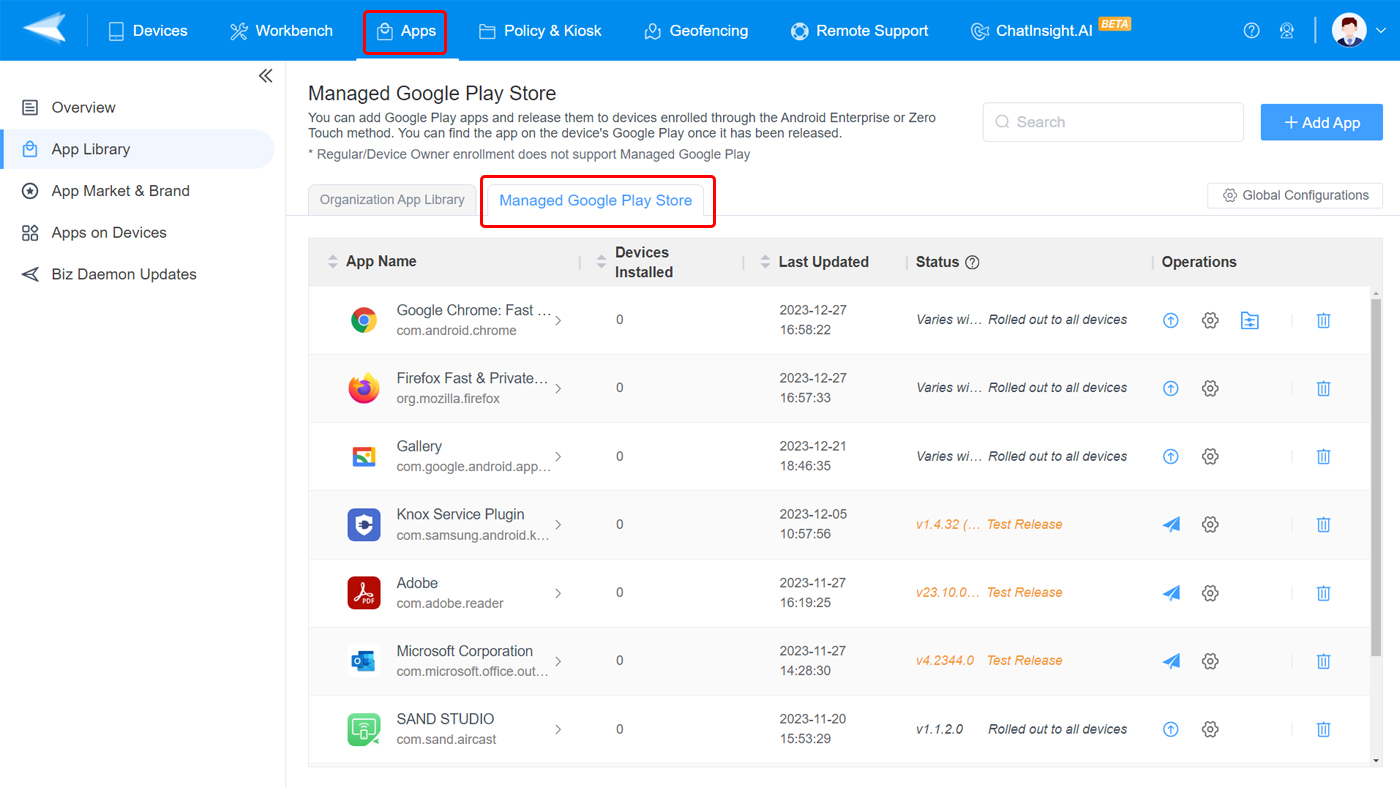
- 1. Open the AirDroid Business admin console and navigate to the 'Apps library' from the 'Apps' tab.
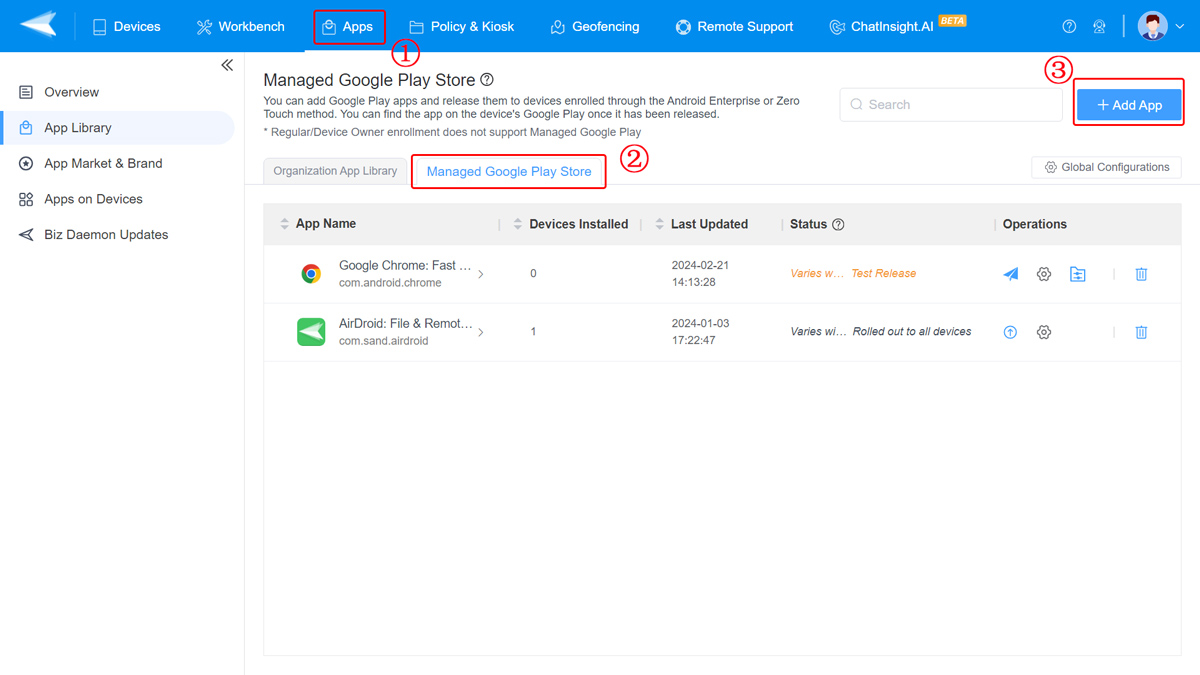
- 2. Select ‘Managed Google Play Store’ and add Google Chrome or any other browser to the list. Then, choose the configurations icon after the internet browsing app available in the list to make changes.
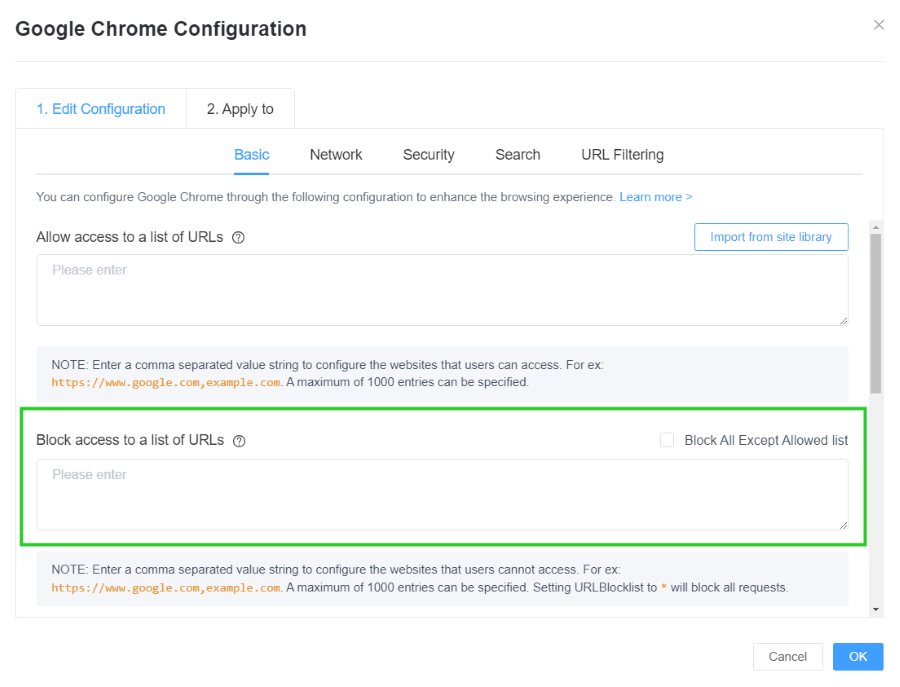
- 3. In the ‘Edit Configuration’ tab, select ‘Basic’ and scroll down to find ‘Block access to a list of URLs.’ Here, you can add all the URLs to block and then press ‘OK.’ Save the settings to apply them to all managed devices.
Calls Blocklisting
Call blocklisting helps to keep them safe from malicious calls. Similarly, call blocklisting helps enterprises keep employees focused on work during work hours by blocking unnecessary calls on their devices.
Specifically, in the transport industry, call blocklisting plays an integral role in avoiding distractions when drivers are on the road. Government organizations and security agencies always prioritize the security of designated authorities.
- It enables users to prevent telemarketing, robocalls, and other unwanted call that can waste time and distract them during work.
- Call blocklisting also allows users to automatically block calls from unknown numbers during working hours to enhance productivity.
- Blocklisting managers provide additional features like caller ID and call recording to enhance security.
Steps to Configure Calls Blocklisting
- 1. Open Airdroid’s admin console and select the ‘Policy and Kiosk’ tab from the main menu.
- 2. Select ‘Policy and Kiosk Config Files’ and then choose the ‘Create Config File’ option. Select ‘Policy’ tab and press ‘OK.’

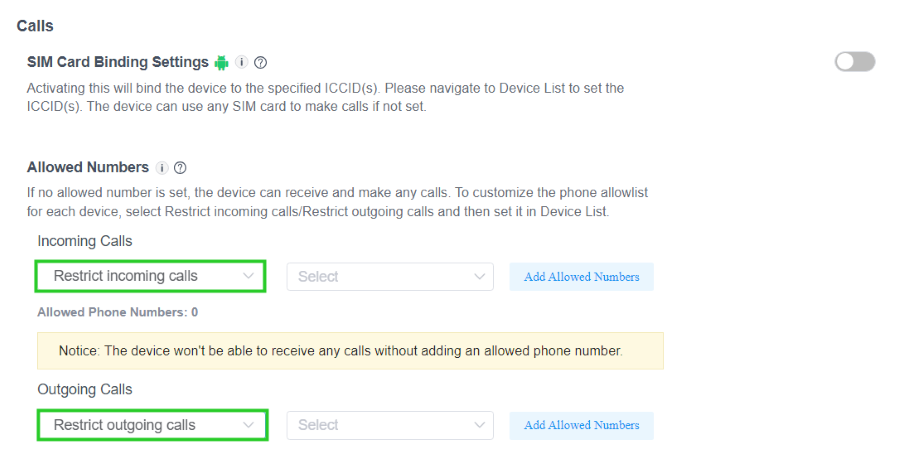
- 3. Find the 'Calls' option in the configuration options on the screen. Customize settings to block incoming & outgoing calls. Select the devices to configure these call-blocking settings and click 'Add' to apply them.
| Blocklist Settings | Usage | Scenarios | Advantages |
|---|---|---|---|
| App blocklisting | Prevents access to unnecessary applications on corporate devices | ·To create interactive kiosks with limited app access. ·In offices to avoid malicious apps that can cause data breaches. | ·Focused work. ·Prevent known threats by directly blocking them. |
| Website blocklisting | Restricts access to specific websites and categories, which can cause distractions | In offices to prevent Facebook and other social media web pages to avoid distractions. | ·Improved security. ·Blocking malicious and non-work related websites ensures productive work. |
| Calls blocklisting | Block unwanted calls like scam calls or telemarketing or the calls from unknown numbers. | ·Block spam or telemarketing calls during official hours. Offices where cell phones are only allowed to make or receive official calls. ·Preventing personal calls like family friends during work. | ·Efficient contact management. ·Simplest way to keep personal life separate from working hours. |
2 Why Choose MDM for Blocklisting?
Choosing MDM for blocklisting brings several benefits to enterprises, including optimizing business processes and improving productivity.
Customizable blocklists
MDM solutions provide highly flexible, customizable options for blocklisting, which helps manage device usage to the maximum extent. It provides options to select what needs to be blocked. Admins can select multiple websites, applications, or call logs to block. MDM provides device customization to apply blocklisting. Admins can smoothly apply blocklisting on specific devices, groups, or all managed devices remotely.
Real-time monitoring and updates
Real-time monitoring enables business administrators to remotely monitor device activities. It provides detailed insights into device usage, such as application usage, installed apps, and data consumption by top applications.
Real-time monitoring helps verify that blocklist URLs or applications are not running on the managed devices. Device and app updates are a prime factor in ensuring security by accessing the latest features updated by the developers. MDM allows scheduled updates so admins can update devices after working works.
Integrate with Security Policies
MDM solutions enable corporate agencies to ensure equal app distribution and configuration settings. Security policies are remotely applied and enforced on all devices to ensure compliance with regulations.
In addition to blocklisting, MDM enables organizations to establish password policies and customize device functionality. This helps to keep data confidential and prevent data breaches with reduced efforts, ensuring permanent growth of business infrastructure and revenue.
3 Enhance Security & Productivity with Blocklist Management
Blocklist manager is a tool that allows optimization of device functions with businesses. These tools offer comprehensive features and customization options to configure settings with enterprise needs.
App blocklisting helps mitigate security risks by preventing or blocking access to non-approved apps, which are more likely developed by cybercriminals to enter into the system and breach privacy.
Similarly, website blocklisting by management tools enhances the security to a greater level by restricting the internet browsing experience for employees.
Some tools also provide remote monitoring and control features to continuously track device usage and ensure employees are actively engaged in work activities. Moreover, additional restrictions like network, services, and calls help to ensure compliance.
4 Blacklist vs. Blocklist vs. Denylist
All these three terms serve a common purpose, i.e., security and limitations on device usage. However, if studied deeply, each can be used in different scenarios to safeguard enterprise networks differently.
A blacklist feature is used to identify undesirable or malicious entities like IP addresses and users to prevent access to known vulnerabilities. It also helps to secure the communication.
Blocklist has, contrarily, a broader concept and usage. It allows listing various applications, websites, content types, and call logs to block access. It is primarily used at home for parental controls and in offices to ensure productivity for work by limiting the employee’s access to non-work-related activities.
Denylist is a list of entities not allowed to operate in a system. Unlike the above terms, it is a more descriptive and latest cyber security addition.
5 Conclusion
Blocklist manager is a valuable tool for enterprises because it enables users to prevent access to various applications, websites, and calling on devices. Enterprises use a blocklisting feature to block non-work-related activities for employees, which helps improve the productivity and security of corporate devices.
It is hard to manage large-scale enterprise devices manually to ensure productive implementation and continuity of blocklisting. So, enterprises need an MDM solution that helps them enroll bulk devices quickly and apply blocklists from a central location. MDM also facilitates implementation on specific devices or groups and real-time monitoring to monitor activities effectively.






Leave a Reply.