Choosing Your Own Device: A Guide to CYOD Cyber Security
In today's fast-paced business world, the idea of Choose Your Own Device (CYOD) is a smart solution that fits well with what employees want. It boosts productivity and keeps employees happy because it lets them pick the devices they like from a list provided by the company.
According to a survey by Wipro, 71% of employees who get to choose their work devices are more productive, and 73% feel more loyal to their company.
But, having the freedom to choose your work device means you've got to be serious about keeping company data safe. That's where Mobile Device Management (MDM) comes in handy. It plays a crucial role in making sure CYOD is secure.
Before we dive into how MDM helps with CYOD security, let's go over what CYOD is, why it's good, how to set it up, and the challenges it can bring.
Part 1. CYOD Model Explained
The first basic knowledge you need to grasp about CYOD is the core point of this model. It will be helpful for you to distinguish CYOD from other models later.
The principle of CYOD model is about providing employees with a selection of pre-approved devices for work purposes. By offering a curated range of devices, enterprises can maintain greater control over the device structure and security while still providing more freedom and flexibility for employees.
Compared to other models of device management, such as BYOD (Bring Your Own Device), COPE (Corporate-Owned, Personally-Enabled), and COBO (Corporate-Owned, Business-Only), CYOD is a middle ground between BYOD and COBO. In the following table, you can differentiate between CYOD and other models based on several components that can define each model.
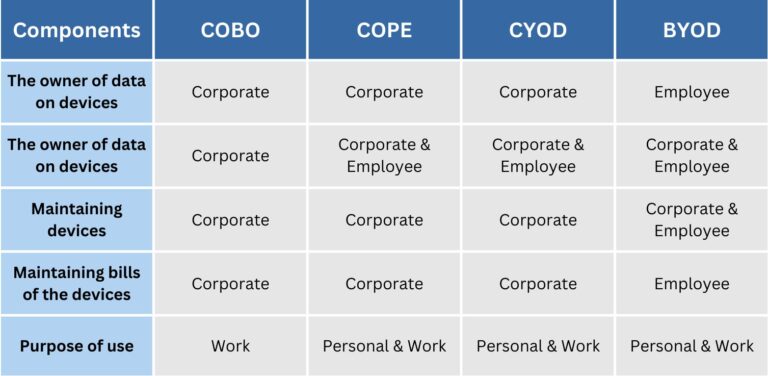
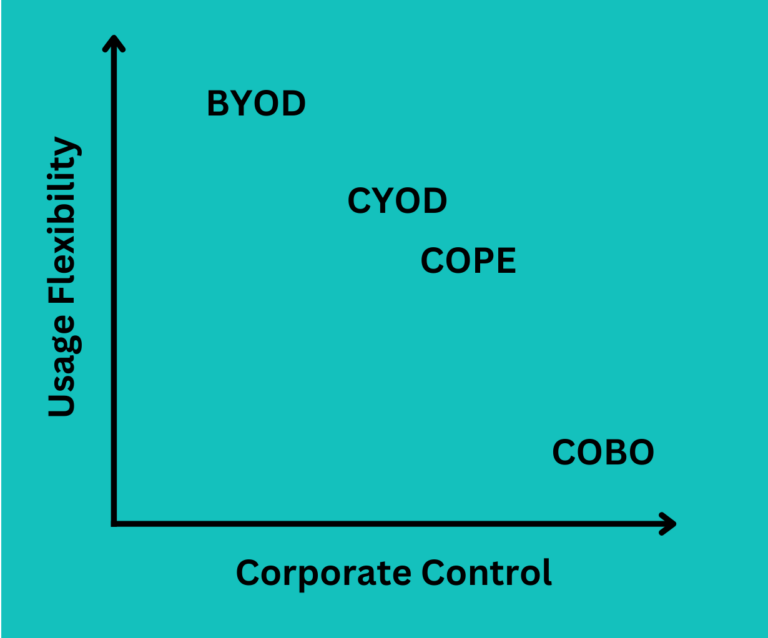
CYOD may look the same as COPE, but the key difference between the two models is the degree of freedom in selecting employees' devices.
In the COPE model, enterprises will not provide the option of pre-approved devices for employees to choose. Thus, as you may see in the below graphic, CYOD has more flexibility than COPE and COBO.
Part 2. Why Businesses Opt for CYOD?
Among the options of device management model, CYOD is the best fit for businesses which look for balance between security and flexibility. They choose CYOD because data security and regulatory compliance are critical concerns for the business, while they are still able to provide device options for the employees to increase their productivity.
When deciding to choose CYOD, it is also important to consider the benefits that come with this model. The first benefit is increasing productivity. As enterprise allows employees to choose the devices from the options you provide, they might choose the devices that they are most familiar with. It will make employees feel comfortable working and increasing their productivity.
The second benefit is enhancing device compatibility and security. Since the enterprise selects which types of devices will be used, IT can control device compatibility and install security features before employees start using them. That can ensure the devices and the data are securely protected.
Furthermore, CYOD can simplify device management as device options are limited in the beginning and IT knows exactly which devices are used across the enterprise.
Part 3. Key Steps to Craft a CYOD Plan
Examining the benefits can reinforce your decision to adopt CYOD as a business device management model. Meanwhile, crafting a successful CYOD plan requires a systematic approach that addresses the unique needs and challenges of an organization.
The following key steps serve as a foundation for establishing a robust CYOD strategy:
1. Assess your business' needs
Conducting a comprehensive assessment of your business technological requirements is crucial. This involves understanding the diverse roles within the company and identifying the specific devices and features that align with each role's responsibilities.
You can include representatives from I.T., legal team, human resources, security operations, and business management. All of these parties have a strong stake in the company’s productivity and security.
2. Specify approved device types
Once the enterprise's needs are identified, specify a range of approved device types that accommodate various work requirements while adhering to the organization's security and compatibility standards.
IT teams can either pre-select the list of devices for each department or open a catalog for employees to choose what they want, then IT will approve or deny at the end.
3. Address security concerns
Security considerations lie at the core of a successful CYOD plan. Enterprises must develop robust security protocols, including data encryption, secure authentication methods, and remote device management capabilities, to safeguard corporate information and mitigate potential cyber threats.
One way to amp up your security game is by using MDM. It's a solution that can give your security an extra boost.
4. Create a clear policy document
To keep things running smoothly and make sure everyone follows the same rules, it's important to create a clear policy document for using CYOD (Choose Your Own Device) at work.
This document needs to spell out the dos and don'ts for using devices, how to handle data, security steps, and what employees are responsible for.
5. Provide staff training
Making sure your team knows how to use the chosen devices is super important for a successful CYOD setup. Give them good training on the devices and what they can do. This helps keep the devices working well for a long time.
When your staff knows how to spot and deal with security risks, your company is better protected from cyber threats and data breaches. So, training them up is a solid move.
Part 4. Potential Hurdles in CYOD Adoption
Even though the CYOD model has a bunch of good things going for it and you've got a solid plan, don't forget about the challenges, especially when it comes to keeping things safe online.
Take a close look at these challenges so you can deal with them before they become big problems. This way, you're staying ahead of the game when it comes to using CYOD.
Some of the key challenges include:
• Data Loss or Leakage
If you don't set up strong security rules, your data might leak out in different situations. For example, if your employees download apps that aren't allowed or seem sketchy, it could create a way for hackers to get in, causing data leaks.
• Unauthorized Access
If a CYOD device is lost or stolen, and it doesn't have proper security measures like encryption, strong password, or remote wiping in place, unauthorized individuals could gain access to the data stored on the device.
• Malware and Virus Attacks
With around 300,000 new malware viruses popping up every day and 72% of businesses worldwide getting hit by ransomware attacks, it's clear that your devices are at risk.
Plus, different devices might not all get updated in the same way. Keeping all of them consistently updated with the latest security fixes is tough. When a device falls behind on updates, it becomes an easy target for malware and viruses.
To stay safe, businesses need to set up solid security measures. That means making sure all devices get regular software updates and have good malware protection. It's the key to protecting against cyber threats.
• Lack of Device Management Control
When you've got all kinds of different devices in the mix, keeping control can be tricky. Things like making sure devices work together, handling different security setups, and just keeping track of all the devices can be a real challenge. This lack of control can open the door to security issues.
That's why it's important to have strong Mobile Device Management (MDM) solutions in place to keep things in check.
Part 5. Secure CYOD with MDM Solutions
Overcoming the challenges we discussed requires a solid CYOD cybersecurity setup. That's where Mobile Device Management (MDM) solutions come in handy. AirDroid Business offers an array of MDM features, empowering you to bolster the security of your CYOD environments:
• Device Encryption
AirDroid Business keeps your company data safe using TLS encryption. This means even if someone gets their hands on the device, they can't get to your data. It's an extra layer of protection against unauthorized access.
• Geofencing and Location Tracking
If a device goes missing, you can leverage geofencing and location tracking to help IT find where the device is and put security measures in place.
You can even set up alerts for when the device goes outside a certain area. And there's a feature called Lost Mode in AirDroid Business that lets you automate locking the device when needed. Nice and simple.
• Remote Device Wipe
If a CYOD device unfortunately gets swiped, you can take action remotely. Pick the device from afar, wipe out the data, and uninstall any apps. Doing this makes sure that sensitive info stays safe, lowering the chance of data leaks and unauthorized access.
• Security Policies
AirDroid Business comes with security tools that help you control how your CYOD devices work.
For example, you can make a list of apps you don't want people to download, stop anyone from doing a factory reset (just in case someone on the inside tries something fishy), and set up passwords for the lock screen.
It's all about customizing things to keep your devices secure the way you want them.
• App Management
With AirDroid Business Application Management Service (AMS), you get a full package for handling apps. This covers safe app distribution on different devices, setting up apps just how you like them, and making updates a breeze.
Plus, the AMS comes with a Managed Google Play Store feature. This helps block weird app sources, making sure your work apps stay secure and lowering the chances of sneaky malware getting in.
Datasheet for Mobile Device Management (MDM)
If you are looking for a better solution to secure CYOD devices, you’ll want to grab our Datasheet for MDM. It’s loaded with detailed information to help you make the best decision for your organization's needs.
Part 6. Closing
CYOD is all about letting employees pick devices that are approved ahead of time while making sure everything stays safe and secure. It can boost productivity, make things more secure, and keep device management simple. But, of course, there's always the concern of cyber threats.
That's where MDM comes in as the all-in-one solution. With AirDroid Business MDM, you get features that handle cyber security challenges. There's device encryption to keep data away from the wrong eyes, custom access controls to stop data breaches and cyberattacks, blocking sketchy app sources to cut the risk of malware, and more.
Curious to know more about what AirDroid Business MDM can do? Click below!






Leave a Reply.