How to Craft a CYOD Policy? (Key Steps Included)

The modern workplace is a far cry from employees carrying out their work, at the office, completely beholden to a desktop PC. Mobility is the name of the game, with demands by employees to carry out work-related tasks from their smart devices, but how do organisations safeguard themselves in this instance?
Fortunately, there are several strategies out there, each offering different benefits depending on the organisation’s unique circumstances. Choose Your Own Device (CYOD) policies are one such strategy allowing organisations to strike a balance between flexibility and security.
- 1 : Understanding CYOD in Practice
- 2 : Building Blocks of a CYOD Policy
- 3 : CYOD Policy Challenges
- 4 : Key Steps in CYOD Policy

- 5 : Conclusion
Part 1. Understanding CYOD in Practice
So, what exactly is a CYOD policy and how does it fit into the device management landscape?
With a CYOD policy, employees are given the choice to select a device from a pre-approved list, which are usually owned by the organisation. This is sometimes a device that is for both personal and professional use.
You might’ve heard of something similar – a ‘Bring Your Own Device’ policy – which differs in that the employee uses their pre-existing personal device, owned by them, to carry out work-related tasks as well.
Both offer substantial benefits and drawbacks, with BYOD tending to come with reduced hardware costs but increased security risk, while CYOD offers the reverse.
Part 2. Building Blocks of a CYOD Policy
Once organisations determine that a CYOD policy is a more suitable solution to them, they’ll then want to think about just exactly what makes a CYOD policy effective.
There are some critical components to think about:
📌Criteria for device selection
• Compatibility with existing software, applications, and network infrastructure.
• Budgets that consider not just upfront investment but overall cost of ownership - think maintenance, and potential repair expenses.
• Scalability of devices to accommodate potential future growth.
📌Security standards
• Devices with robust security features, such as biometric authentication and encryption capabilities.
• Password requirements that follows best practice with mandated use of complex passwords and regular changes.
• Malware protection for detecting and mitigating the impact of malicious software.
📌Acceptable use guidelines
• Clearly outline expectations regarding the protection of sensitive and confidential data.
• Guidance for acceptable balance between personal and professional use of CYOD devices, including use of personal applications and social media.
• Clear guidance on which activities that are strictly prohibited, such as unauthorised access to networks or the installation of unauthorised software.
📌Adherence to compliance requirements
• Identifying industry-specific regulations and compliance standards governing the handling and protection of sensitive information. For example, healthcare organizations must comply with the Health Insurance Portability and Accountability Act (HIPAA) to safeguard patient information, maintain privacy, and avoid legal repercussions.
• Alignment with third-party vendors or partners to ensure these parties are compliant with the relevant regulations, as well as establishing data transfer agreements so it is processed compliantly.
• General Data Protection Regulations (GDPR) so that CYOD policies align with the principles and requirements when handling personal data for both customers and employees.
There is plenty more to consider, but these building blocks are the foundation for any good CYOD policy.
Part 3. CYOD Policy Challenges
Of course, any new policy won’t come without its challenges. There are several key considerations when it comes to implementing CYOD policies for organisations to consider.
🔰 Employee resistance
Unlike BYOD, there isn’t carte blanche for which devices employees can use with CYOD.
While the policy does provide a semblance of choice, organisations may still face employee resistance, predicated on a perceived loss of control over their device choices, when it comes to implementation.
🔰 Device compatibility and integration
IT teams need a meticulously planned approach to address the compatibility issues brought about by the diversity of devices within the ecosystem.
There may be more uniformity than BYOD, but it doesn’t mean it isn’t without its challenges. The initial procurement phase needs to factor this in.
🔰 Evolving security landscape
Despite being a more secure alternative to BYOD policies, CYOD implementation still requires industry-leading security measures and policies that meet tackle those challenges head on.
Security threats evolve all the time, and technology along with it, so organisations need to keep their finger on the pulse.
🔰 Budget constraints
A CYOD policy costs more than BYOD because of the upfront costs of the devices. That upfront investment might be too much for organisations (particularly smaller ones) to bear.
After initial procurement costs, lifecycle management needs to be considered, as repairs, provisioning, maintenance, and device retirement all require additional spend, time and resources.
Part 4. Key Steps in CYOD Policy
It’s not enough to implement a CYOD policy in the hopes that it will be adopted en masse, without any issues.
When you consider that, in 2022, the average cost of a data breach worldwide is around $4.35 million, it’s easy to see why a CYOD requires constant nurturing and attention, from device setup, security protocols, and reporting procedures.
A. Welcoming and Equipping Employees
If organisations want to ensure that employees are appropriately educated and trained, some things to consider are:
- Onboarding workshops can help employees familiarise with the operating system and device to mitigate any potential issues stemming from the acceptable usage of the policy.
- Regular mandated security training that covers topics such as password management, phishing or other cybercrime threats, will ensure employees continuously adopt best practice.
- Establishing a dedicated reporting portal that contains clear escalation pathways, so employees need to quickly and easily log issues with IT.
These are just some of the ways organisations can implement a CYOD policy, regardless of the size of the organisation, in a successful way.
B. Managing Devices Across Their Lifespan
As we’ve mentioned, there is more to a CYOD than just equipping your employees with their devices. The lifecycle of CYOD begins with procurement, to provisioning and maintenance, then ends with the retiring of the devices.
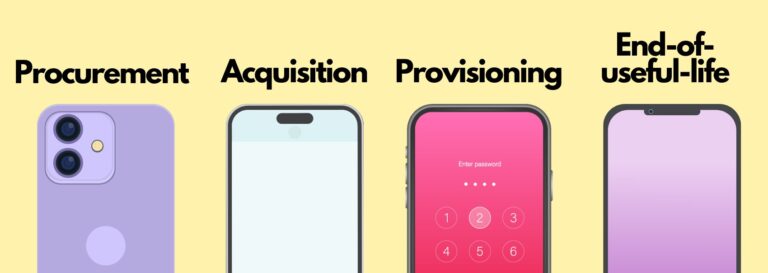
Procurement is where much of the research and analysis is required. First, an audit of the current device inventory should be carried out, followed by establishing clear objectives and requirements for the new policy, such as the desire operating system.
Then, the acquisition of the devices themselves, which involves evaluating and selecting a preferred vendor, then negotiating a contract and payment terms.
The provisioning phase simply refers to setting up – or enrolling – the devices to work in alignment to the CYOD policy. This phase is dependent on the organisation but consists of the configuration and customisation of the devices within the IT network, considering things like network settings, security policies, and also email configurations.
End-of-useful-life (EOL) refers to when devices reach a stage of obsolescence need to be retired from the fleet. This element is where devices will be decommissioned, so that the integrity of company data is retained. Securely wiping the devices is one of the steps in this process, which ensures all data is protected.
C. Security Measures and Controls via MDM
This should give you a solid understanding of just what makes an effective CYOD policy. In the provisioning phase, we mentioned the need for setting up the CYOD devices before deploying them to the organisation. That’s where Mobile Device Management (MDM) solutions play a pivotal role.
Put simply, MDM is a foundational tool for businesses that enables IT admins to centrally manage, deploy, and maintain all devices within the fleet, affording them granular control over all aspects of the devices to ensure security integrity is maintained.
One example is AirDroid Business MDM, which contains an array of tools that tools to bolster a great CYOD policy.
Some of those are:
- Device enrolment and provisioning: Easily enroll and provision company-owned devices in bulk with predefined template.
- Advanced encryption: Secure file transfer with multi-layered encryption using HTTPS and end-to-end encryption.
- Policy enforcement: Ensure that devices adhere to security policies, including security authentication requirements, device compliance, and data loss prevention measures.
- Kiosk Mode: Create a fully customised environment with restricted access to a specific app or group of apps, websites, and device functionalities.
- Application management: Configure, deploy and manage business apps over-the-air with rich rollout options – all from a single remote dashboard.
- Monitor and alerts: Remote monitor, receive alerts, and respond to abnormal events for endpoints (e.g. excessive data usage or network errors) in real time to protect data.
Datasheet for Mobile Device Management (MDM)
If you are looking for a better solution to secure CYOD devices, you’ll want to grab our Datasheet for MDM. It’s loaded with detailed information to help you make the best decision for your organization's needs.
D. Balancing Privacy and Security
Now, without employee buy-in, a CYOD policy is never going to achieve the intended objectives. A common grievance is that employees feel their privacy is compromised, with IT admins having such close control over their devices.
As a result, the policy requires a fine balancing act that ensures both – often opposing – forces are managed. While there are built-in tools that achieve this balance, it should be a fundamental priority of organisations to have a stress-tested communication policy in place.
Meanwhile regular training sessions and two-way communications channels will offer invaluable insights for IT admins and comms teams to work with and address concerns on an ongoing basis.
Part 5. Conclusion
While CYOD policies don’t make sense for all organisations, whichever ones do go with that option will need to consider everything involved before they jump straight to implementation.
There will always be challenges, from either from an operational point of view or an employee-facing one, but there are enough significant benefits to a well-conceived policy that makes them more than compelling.
One thing is certain: technological trends and best practices will continue to evolve, so CYOD might not make sense for organisations in the future, but for now they provide effective means to buttress operational security while assuring employee privacy and satisfaction, offering a balance that is higher in demand every day.






Leave a Reply.