What is Device Binding? Everything You Need to Know
Have you ever tried to log in to your account, say a financial account, only to realize that you can’t access it because someone has stolen your details and maybe used them to steal your money? Well, attackers use various hacks to steal user account details even without touching the user's device. The consequences of theft of personal details can be far-reaching especially if the compromised details belong to a business or organization.
Therefore, it is important to link your device to your personal account so that in the event your account details are stolen, the attacker cannot access your account using a different device. This is exactly what device binding does. Well, this article takes you through everything you need to know about device binding including how it can help you protect your account and sensitive details on your device.
Part 1: What is Device Binding & How It Works?
Suppose you have a special book and you don’t want anyone else apart from you to access it. You will probably lock it on your shelf and have a special key that opens it.
Perhaps people might know there is a book inside but they cannot access it because you are the only one with that special key. In this scenario the key is your device binding!
Now, device binding as the name suggests binds your device to your account and authentication process so that if someone steals your account details, they cannot access it with a different device other than your device.
It simply creates a unique association/link between an application and a specific mobile device. This means the app can only be accessed and used by that specific registered device.
Simply put, it attaches your device to the account authentication process hence preventing cases where attackers steal your account information and access your account using other devices.
How does binding device work?
When you sign in to the app for the first time, this app creates two keys namely public and private keys.
The app keeps the private key and sends the public key to the backend server. The next time your device sends a REST request (to retrieve or modify resources), it signs the payload using the private key. Upon receiving the message, the backend server validates the payload using the public key.
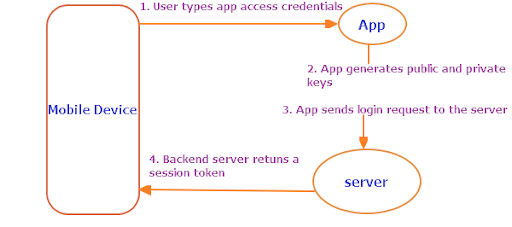
The server will then encrypt the files using the public key then send them to the app. Now, the app will store the files and use the private key to decrypt them. Since the private key is not extractable, attackers stealing the session token cannot be able to decrypt the files because they don’t have the associated private key.
Part 2: Practical Use Cases for Device Binding
Device binding is a useful app access security feature and finds extensive applications across many fields. While it is difficult to discuss all possible fields, here are some of the areas that heavily benefit from device binding.
1Financial Services Apps
Financial service apps require enhanced security because a leak in your account credentials can put you in financial losses. This can be worse especially if the financial app is used to manage the company’s finances. However, with device binding, you tie accounts with specific devices, making it extremely hard for unauthorized users to access your account using other devices. Device binding also reduces fraud because it limits access to registered devices. Additionally, it helps your company become regulatory compliant and win the trust and confidence of customers.
2Secure Communications in company-owned app
Several companies have company-owned communication apps for internal communications. These communications are often private to the company and such information should not be accessed by unauthorized users such as competitors. This can include emails, meeting sessions, and calls among others.
By leveraging device binding, companies can restrict and limit the number of devices that can access these communications. This ensures that only company-verified devices can access this information hence preventing costly data leaks.
3Healthcare
Healthcare is a sensitive field and access to healthcare apps by unauthorized users can prove costly. There are many healthcare apps available and others are developed for specific healthcare facilities. These apps could be used to enroll patients, access patient details, make appointments and follow-ups, procure drugs, and manage payments.
Device binding ties access to the hospital accounts to certain devices, operated by healthcare employees. This way, it becomes difficult for attackers to get into the hospital accounts and cause modifications even if they have the login credentials.
4Enterprise Device Management
Enterprise devices perform an array of tasks that are critical in the running of the enterprise. However, enterprise devices are often handled by different users with unique behaviors. This makes them vulnerable to attacks including account detail theft.
However, device binding can help prevent account access and theft of sensitive information within the respective app accounts. It simply ensures that specific apps can be accessed from a registered device thus preventing unauthorized access and data breaches that can have far-reaching consequences on the enterprise.
Part 3: Device Binding and MDM Solutions
Device binding and MDM can be seamlessly integrated to help IT admins conveniently control and manage the security of a fleet of devices, data, and apps from a central computer. The Android or iOS device is first registered with the MDM solution then device binding is activated within the platform.
Depending on the MDM you are using, you can add additional security policies and deploy across multiple devices at once. With the respective devices now bound, the admin or IT teams can monitor them in real time from a single console.
With a good MDM solution like Android Business, you can add more policies and restrictions to your bound devices to further improve their security. For example, you can manage OS updates, restrict app downloads only from known sources, manage access permissions, remotely lock and unlock devices, and manage app updates among others. The good thing with AirDroid MDM is that you can set policies on specific devices and apps based on your enterprise needs.
Summary
Device binding is becoming a powerful solution to unauthorized account access. It has made it more challenging for attackers to access private information or important data even if they manage to steal login credentials. If you are running an enterprise, device binding should be top of your priorities. You can also make it easy to manage and control your bound devices by simply integrating device binding with solutions like a good MDM tool.





Leave a Reply.