GDPR and MDM: What Enterprises Should Know
MDM (Mobile Device Management) is a popular solution to help vendors manage and secure multiple devices working on different operating systems and in different locations. This blog explores the significance of GDPR compliance in MDM.
GDPR stands for General Data Protection Regulation and is a European regulation to protect the PII (Personally Identifiable Information) of an individual. GDPR is an essential element in enterprises because it ensures the safety of customers’ data. Also, the non-compliance with the GDPR standards in enterprises can result in penalties.
1 Overview of GDPR Compliance
This section covers the overview of GDPR compliance to help gain a better understanding of its elements.
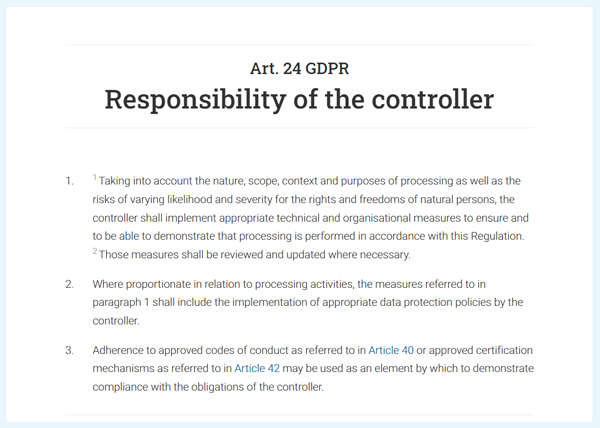
Understanding Data Controller and Processor
The data controller is the body that defines the purpose and the means of data collection and processing. On the other hand, a data processor is the body that processes the data of the business’s users on behalf of that business.
To understand this concept better, if a business uses MS Team for all of its internal communications, then the company is the data controller whereas Microsoft is the data processor.
- Controller
- Processor
Source: GDPR – Official Legal Text
Obligations of Data Controller
The data controller is responsible for allowing the data processor to collect and process its users’ data. Therefore, the data controller must abide by the following:
- 1) Ensure the collection of data is necessary and per the standards of GDPR.
- 2) Take into consideration all the potential risks that may occur in the processes of data collection and processing.
- 3) All the measures and processes must be reviewed at regular intervals to update them per requirements.
GDPR Compliance in Mobile Devices
Under GDPR compliance, all the devices that have access to users’ data in any way need to have standards for the protection of personal data. An employer must ensure that the company’s processes or workflows are not collecting or interfering with the user’s data. If any of the personal data is collected, it must be with the permission of the user and processed under legal standards.
2 How can Enterprises be Compliant with GDPR in Mobile Device Management?
MDM gives you a better hold of security practices by allowing you to control and manage the devices in a better way. It’s a must that enterprise mobility and GDPR go hand in hand to avoid any sort of security or user rights disputes.
One may argue that fines and penalties are not the worst to happen in case of not being able to comply with the GDPR standards, but in reality, it is. The fine is usually 4% of annual global revenue or the hefty amount of €20 million, whichever among them stands higher. Along with that, it costs the company in terms of its reputation and loss of future business growth.
Considering all this, the following are the five ways to comply with the GDPR in MDM:
1Data Protection Impact Assessment (DPIA)
To help set up a security and privacy policy that handles most of the potential risks concerning GDPR standards, assessments are a must. One of the significant assessments is DPIA.
If put simply, it’s a process designed to help you uncover the potential security concerns regarding the data processing in your system. It helps you identify the risks on the go and take the essential measures to reduce the occurrence of those risks in the future.
As soon as any of the risks are identified, the best practice is to set a policy that reduces its occurrence for users in the future. For example, during risk assessment, you may identify that the location tracking feature of your MDM is non-compliant with the GDPR standards as it is collecting user location data without prompting the user for his permission.
In such a case, you need to set up a security policy right away that enables the MDM to prompt the user for his permission whenever the location tracking feature is enabled.
2Policy for BYOD Devices
Many companies operate on the model of Bring Your Own Devices (BYOD) to save resources or for an ease of use. Although it seems like a feasible option in terms of finances, it can pose serious security concerns. Therefore, it’s important that Bring Your Own Device GDPR is in place.
To handle this problem, your MDM must have a system to keep the personal and professional data separate. It allows mobile devices to operate in two different modes: Personal and Work. That way, the employees can keep their personal data out of the legalities and the professional data under standard security measures.
But to have a proper GDPR in this model is important. Two main problems include ensuring the protection of user’s personal data from the policies and gaining the consent of the users to add two modes to their devices. However, both are important elements to ensure that the devices abide by GDPR standards and do not cause any potential risk to the company.

3Access the Data Protection Impact of Your MDM
It’s important that you keep on accessing and analyzing the data protection impact of your MDM solution. This helps you identify the loopholes and risks in your system, giving you the time and bandwidth to solve them before they turn into unsolvable issues.
It’s more of a continuous analysis of your MDM to help solve the issues even before they occur on the user’s end.
4Evaluate Coverage of MDM Solution
To gain a better understanding of how well your MDM is working, it's important to evaluate its coverage. By coverage, we mean the elements of your business and user data managed under the MDM. Two such examples include Device Inventory and Network Logs.
Device Inventory is a centralized dashboard for the administrator to access the list of all the registered devices along with their details. This makes it easier for you to access the data about any device. Network logs, on the other hand, are the record of all the transactions or events taking place on individual devices.
By having a better understanding of your MDM’s coverage, you can make smart GDPR mobile device management decisions.
5Apply MDM Solution to Secure Personal Data
Lastly, it’s necessary to make the most out of the MDM solution by applying the necessary security measures to protect the user’s personal data. This restricts the user's actions and auto-collection of impermissible data.
Some of the MDM solutions to comply with the GDPR for mobile apps are as follows:
- Enforce the user to set a PIN or password for the device. It reduces the misuse of devices on a generic level as the access of the device is dependent on the entry of the defined password.
- Have a configured remote access to the devices in a way that you can lock the device remotely and wipe the sensitive data in case of unforeseen situations.
- Set up network settings to reduce the connection to unprotected networks and ensuring logging of all events and transactions made over the server.
- You can force the devices to update the system to the latest versions to help ensure that they don’t miss out on any important security updates and that they stay on a consistent version.
- By restricting access and allowing the usage of certain apps, you can reduce the security risks by a great deal.
3 Other Methods to Protect Data in Mobile Devices
Although MDM is a great technique to protect data in mobile devices per GDPR standards, there are some additional methods to do the needful which include:
Sandboxing and Encryption Solutions
Sandboxing is a process of creating a mimic environment as that of the end-user operating system for code running and analysis. It keeps the detected code vulnerabilities separate instead of disrupting the whole end-user environment. Also, having encryption solutions in place can help the transfer, storage, and deployment of sensitive data in a safer way.
Training Plan
It's important to educate your employees on the significant role they play in ensuring the company’s security and data protection. To do so, set up extensive security training plans to keep them posted about the latest trends and cybersecurity practices.
Incident and Recovery Plan
Have a practical and effective incident and recovery plan in place to help deal with the security breaches. The incident plan lays out the practices to keep your data secure in case of a security breach. Whereas the recovery plan outlines the steps to continue the business processes after overcoming a disruption.
4 AirDroid Business Features
AirDroid Business provides you with MDM solutions that not only lower your operational costs but ensure the abidance of standard security practices. From setting up kiosk mode to policy creation, AirDroid Business gives you extensive control over your devices. With AirDroid, you can manage and control the devices per your company’s IT policies and international standards.
AirDroid Business - Mobile Device Management Solution
AirDroid Business helps to manage and control the Android mobile workforce. This enables real-time monitoring of Android devices by tracking locations, geofencing, data processing and analysis, intelligent alerts, and remote maintenance.
It also provides a secure and centralized platform to manage all devices. All these make it an excellent choice to help enhance device management and security in an organization.






Leave a Reply.