10 Crucial Ways for Securing Remote Access: Safeguard Your Data
Remote work has become a trend in every business that is based on technology. When you have a sizeable remote workforce, you must pay immense attention to remote access security. There has been an exponential rise in remote access security breaches with the rise in remote workforces.
Remote access sessions have become an easy target of cybercriminals through which they get access to corporate networks and sensitive data.
Therefore, secure remote access is essential. Here we will discuss all the aspects of secure remote access and illustrate how to secure remote access in the best possible way.
Part 1. What is Remote Access Security?
Remote access is a connection between two devices located in different locations through the internet. Remote access security refers to the act of securing remote access sessions through different methods and measures.
Secure remote access involves proper authentication, strong encryption, and controlled access. You have to adopt the best security practices to ensure operational efficiency during remote access.
Through reliable remote access software, you can securely establish remote connections and eliminate unauthorized intrusions to digital assets. Along with advanced techniques, you must incorporate the latest technologies and enforce strong cybersecurity policies across the organization. That is why employee training programs are an essential part of remote access security.

Part 2. How to Secure Remote Access? - 10 Ways
We have already stated that you can achieve strong remote access security through multiple secure remote access solutions. Here are all the ways to secure remote access from all possible cyberattacks.
1Use of Strong Passwords & Two-Factor Authentication
Authentication of users is essential before establishing a remote connection. You must strengthen the authentication process so unauthorized users cannot intrude on remote sessions. That is why two-factor authentication is a must for securing remote access.
Along with password authentication, SMS or TOTP-based authentication can ensure that only authorized devices establish remote connections.
Besides, the passwords must be strong and complicated so that cybercriminals cannot guess them. You can use a password manager to get strong password suggestions and save your passwords safely.
2Implementation of Firewalls & Network Segmentation
A company needs to invest in establishing strong firewalls to prevent intruders from getting through during remote access sessions. For remote workers, cloud-based firewalls work the best. You can tweak the settings and strengthen the firewalls to scale up network security.
Along with firewalls, network segmentation is a necessity. It is a security technique through which you divide the network into sub-networks. The sub-networks can have different security settings and prevent a cyberattack on any sub-network from spreading across the network.
3Use Reliable Remote Access Software
Finding trustworthy secure remote access software is also a great way to ensure seamless and secure connections to various devices and networks. This allows for efficient collaboration and communication, while also safeguarding sensitive data.
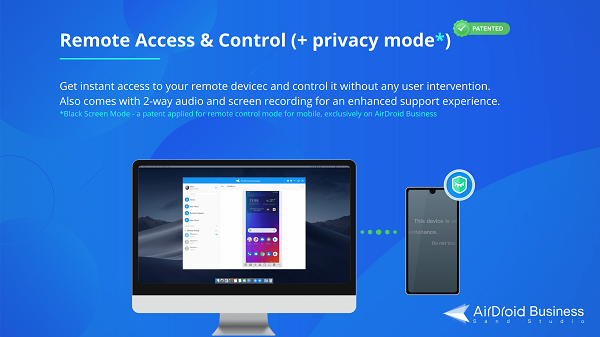
AirDroid Business is one of the most reliable Android-based device remote access software which uses TLS encryption to ensure the security of remote device connection and data transmission and protect the safe operation of the device.
Its black screen mode can protect organization data when remote accessing and controlling a device as the device screen will turn black and others are unable to see the screen content.
Moreover, you can enforce a security policy across all devices and set device usage restrictions for security reasons.
4Zero-Trust Access
Zero-trust access is a security solution that is based on the concept of never trusting users or devices without proper verification. Any request to establish a remote connection must be verified before approval to eliminate unauthorized remote access.
Only after proper authentication and verification remote access to devices and data is provided based on the security policy and access controls. Even when the network security is compromised, zero-trust access service ensures minimal damage.
5Intrusion Prevention & Detection
The priority should be intrusion prevention to mitigate the risk of cyberattacks. An intrusion prevention system(IPS) is responsible for securing the devices and applications in use along with the network. It should protect your network with the latest security technologies to block incoming attacks.
An intrusion detection system(IDS) should be placed to monitor the network activities. The system should detect abnormal behaviors and instantly block the compromised applications or devices. It should also alert the concerned team to promptly stop intrusion before further damage.
6Use of VPN & Encryption
A virtual public network(VPN) is software that encrypts data exchanged between the remote user and the company's internal network. It creates a private tunnel that cybercriminals cannot access even when they have breached the remote user's network. Therefore, remote users can safely access the company's server data, resources, and applications through the assigned VPN access.
Certain VPNs come with firewall settings for enhanced remote security. Apart from that, the files on the company's network must be encrypted so they cannot be decrypted easily, even when they land in the wrong hands. Therefore, your company's sensitive data will stay protected all the time.

7Develop a Cybersecurity Policy
Every organization needs a proper cybersecurity policy strictly followed by every remote employee. A cybersecurity policy contains the dos and don'ts that the employees need to follow on their work devices. The policy can blacklist applications and websites that employees should not access from their work devices for security reasons.
The policy should also specify the steps to follow during a security breach incident. Besides, there can be different policies for employee-owned devices and company-owned devices. Moreover, it should specify the security measures to follow while transferring files and backing up data.
8Employ the Principle of Least Privilege
If you limit the privileges and access permissions of the employees, you can mitigate security risks significantly. You can categorize users into different groups with different sets of privileges. You can assign your employees into different groups based on their positions and the privileges they need for regular operation.
For example, an admin team member will be a super user with all access permissions, while an employee will be a standard user with permission to access certain applications and resources. Besides, there can be a guest user with very limited privileges so that the system's security is not disrupted.
9Regular Software Updates & Patching
Every application used in remote access should be updated as and when the updates are available. The latest version covers up the security loopholes in the previous versions. Hence, you should update as soon as possible to prevent cybercriminals from breaching security through those loopholes.
Software companies also release patches from time to time. Patches are updates that fix the security vulnerabilities in the current version of the software. Not just software, you should update the operating systems and the devices as and when applicable for complete safety in remote access sessions.
10Employee Training & Awareness Programs
Last but most importantly, you should arrange training sessions to teach your employees about the latest remote access security practices and the company's cybersecurity policy. Cybercriminals target unaware employees to get access to the network through tricks and wicked methods. They should know about the actions they should not perform on their work devices.
When the employees are aware of the security threats and avoid certain steps through which cybercriminals trap remote users, the risk of security breaches can be mitigated to a greater extent. Therefore, arrange awareness programs and ensure that all remote employees strictly follow the security steps as per your company's policy.

Part 3. What Technologies are Employed for Secure Remote Access? How Does It Work?
We have discussed the steps for secure remote access, but remote access security is a combination of steps and technologies. Secure remote access combines multiple security technologies, and we will explain them for your understanding.
● Endpoint Security:
Endpoint refers to the end-user devices that remote workers use. Endpoint security refers to the firewall or antivirus installed on endpoint devices to prevent cyberattacks, detect intrusions, and block the attempt.
It is also responsible for implementing the company's cybersecurity policies by preventing access to certain blacklisted apps and websites and restricting setting changes.
● VPN:
A virtual private network is essential for securing remote access sessions. It provides a private tunnel for the endpoint devices to connect to the company's servers. The tunnel is encrypted so that there can be a secure transfer of data without any intrusion.
Even when the endpoint has an insecure network, VPN ensures that a cyberattack on the endpoint network does not affect the remote interaction from a security standpoint.
● Zero-Trust Network Access:
This security solution ensures that no remote connection can get through without proper authentication. Even when the device has connected previously, a re-authentication is necessary instead of trusting the network automatically. This adds an additional layer of security over the existing measures.
● Network Access Control:
It combines reliable remote access software, different security tools, and security policy enforcement. Besides, restricting privileges and permissions for different users is part of proper network access control.
● Single Sign-On:
While multi-factor authentication is essential, a single sign-on option allows users remote access through strong credentials. This is suitable for remotely accessing unattended devices instantly.
Part 4. Why is Secure Remote Access Important?
Remote access sessions are vulnerable to cyberattacks. Insecure remote access sessions are easy targets of cybercriminals as they can intrude on them without much resistance. We will discuss the risks of remote access that can be avoided with proper security measures and the challenges of secure remote access.
1Common Risks of Remote Access
Here are the common risks associated with remote access, which point out the importance of securing remote access.
Weak or stolen credentials
An insecure remote access connection needs only predefined credentials to establish the connection. If these credentials are not strong, cybercriminals can guess and crack them to get remote access to the company's server. On the contrary, two-factor authentication can prevent such unauthorized attempts and secure remote access properly.
Unsecured network connections
Remote workers are likely to use public networks to connect to the company's servers. More often than not, public networks are not secured by modern technologies. Such unsecured networks are playgrounds for cybercriminals.
They can breach the network and get access to the connected devices. Therefore, remote access through unsecured network connections is absolutely risky.

Outdated software and firmware
If the remote device connecting to the company's server has outdated software and operating system, they are vulnerable to security attacks. This is because outdated versions have security vulnerabilities that cyberattackers can exploit easily to gain access to the remote connection sessions and cause havoc.
Lack of multi-factor authentication
A single authentication step is no more secure as no connection should be taken for granted. Remote access without multi-factor authentication is blindly trusting the connected devices and users. It is easy for cyber attackers to get through single-factor authentication by cracking credentials and identity theft.
2Challenges of Securing Remote Access
Every solution comes with certain challenges, and remote access security solution is no exception. You should be aware of certain challenges of secure remote access.
Lack of control over the remote device
Securing remote work devices is challenging because you cannot get full control over their operations. You can monitor them remotely, but ultimately, it is up to the employees how they handle their devices to implement security policies and stay away from cyberattacks.
Complexity of access management
A secure remote access solution needs a company to manage different groups of users with different permissions and privileges. User access management becomes complicated when the workforce is relatively large with different hierarchies.
The security team has to develop a clear access management plan to overcome the complexity without compromising security.
Difficulty in enforcing security policies
Security policies are difficult to implement in any organization with a sizeable remote workforce. This is because it is difficult to monitor remote work devices all the time.
Not all employees are sincere enough to stick to the security policies, and any misstep can lead to cyberattacks. Therefore, repeated training and awareness program, along with automated monitoring, is a necessity.

Increased attack surface
The remote workforce increases the attack surface for cybercriminals. The company's devices need to be connected to remote devices through the internet, which makes the connected devices vulnerable to cyberattacks.
With the expansion of attack surface, a company must invest more in security and risk management. The company needs to spend more on reliable remote access software and implement the latest security technologies and techniques.
Vulnerabilities in third-party software
Third-party applications providing security in remote access are a constant target of cybercriminals. They try to spot and get through the security loopholes in the targeted applications to get exposure to the users of the applications. Therefore, you need to choose a reliable remote access application like AirDroid Business to avoid the risk of software vulnerabilities.
User behavior
It is difficult to change user behavior though security measures demand them. Many employees do not take security policies seriously nor implement them sincerely.
They keep doing the activities they are habituated to, making their devices and connected networks vulnerable to cyberattacks. Changing user behavior involves training, monitoring, and assessing regularly.

Part 5. What are the Benefits of Adopting Secure Remote Access Practices?
Despite the challenges, the benefits of practices to secure remote access are paramount. That is why companies with remote workforces are adopting secure remote access practices. Here are the benefits of securing remote access.
1Enable access to devices in different location
Employees can access the company's devices and resources remotely from anywhere with a high level of security. Companies can assign specific access permissions to applications and data for employees as per their roles and responsibilities.
This allows companies the flexibility to allow employees to work from anywhere to have a better work and life balance. The security team also finds it easier to centrally manage all the connected resources and take immediate steps to mitigate security risks.
2Enhance productivity and simplifies administration processes
A remote secure access solution simplifies the administration processes by offering a centralized approach to managing distributed assets. You can assign roles, monitor devices, and provide support and maintenance service from a central dashboard.
With simplified administration, the productivity of the admin and security team enhances. Besides, implementing security policies helps avoid distracting activities on devices, increasing employee productivity.
3Strengthen the governance of access
The admin team can remotely access the remote work devices anytime and provide support and tweak settings and apps for security reasons. They can monitor different parameters of the remote work devices in real time and take prompt actions to mitigate any security risks. Remote access and control ensure better governance of the remote assets and implementation of the security policies.
Part 6. Final Words
When you have a sizeable remote workforce in your company, secure remote access to protect your company's resources is important. We have stated all the steps and technologies you must implement to secure remote access effectively. Take action now to protect your data.





Leave a Reply.