Unravel Incident Management Process & Best Practices
(INTRO)
Businesses are more reliant than ever on the performance of their IT infrastructures. Should a major incident undermine the operational capability of these technology systems, the implications could be dire – the ability to produce goods, deliver services to clients, or relate information to employees could be significantly impacted. Therefore, senior leadership teams must develop appropriate incident management policies and procedures which serve to mitigate against these risks. By doing this, businesses can suitably prepare themselves for events that cause significant disruption to productivity.
A fit-for-purpose incident management plan enables companies to swiftly identify the scale and nature of an issue, initiate a considered and proportionate response, and later re-calibrate their internal processes in order to reduce the likelihood of a repeat occurrence.
In the following sections, we examine the various aspects businesses must consider when constructing their respective IT incident management procedures, and, by analyzing the potential consequences of failing to placate a threat to business continuity, we shed light on the critical importance of responding effectively to major incidents.
- Part 1 : Explanations of Incident Management, the Process, and Worflow
- Part 2 : 8 Examples of Incident Management
- Part 3 : Incident Management Process: 8 Key Steps
- Part 4 : Best Practices to Create Incident Management Workflow
- Part 5 : 4 Incident Management Process Improvement Ideas
- Part 6 : Incident Response Plan Example: How to Use MDM Automated Workflow
- Part 7 : Why Do Businesses Need an Incident Management Process?
- Part 8 : FAQs
Part 1 : Explanations of Incident Management, the Process, and Worflow
What Is Incident Management, Incident Management Process, and Incident Management Worflow?
Incident Management | Incident Management Process | Incident Management Workflow |
|---|---|---|
| It is the approach of identifying and resolving issues that affect IT systems, services, or infrastructure. | It refers to the series of steps taken to deal with incidents, and is a part of IT Service Management framework. | It is an implementation of an incident management process that illustrates task procedures, and sometimes represents the functionality of a certain tool. |
The composition of an incident management plan is typically organized under three key focus areas: management (how a specific risk will be dealt with/contained), process (who is accountable for delivering the response) and workflow (what are the physical actions taken in order to tackle the problem). We review each element in closer detail below.
Incident Management is vital that IT teams agree to a general response strategy. This may be partially achieved through the establishment of SLA or ITIL. IT teams will also consider how their approach may alter when addressing potential threats to security; pressing issues may require proactive intervention, whilst a reactive stance may be most appropriate in other cases.

During the Incident Management Process, major incident response efforts usually involve and impact a sizeable number of individuals. Clearly, those who are chiefly accountable for detecting, diagnosing, and tackling systems issues will feature prominently in incident management policies, but other stakeholders must also be factored into planning discussions – employees, suppliers, and clients (and others) may also be impacted. Furthermore, a process for communicating effectively with senior leadership teams during periods of disruption should also be considered.
There must be an established methodology for dealing with each type of incident, supported by an agreed set of response workflow charts. All key personnel should be acutely aware of the specific actions they need to undertake when a particular event occurs – the nature of this activity will depend on whether the problem exists in-house or in a customer-facing environment.
Note
- SLA - Service Level Agreements, is a set of commitments which outlines what departmental teams will deliver in the event of a specific issue.
- ITIL - Information Technology Infrastructure Library, is a detailed bank of information about the internal IT infrastructure, which helps IT operatives to better understand how an incident may impair operational integrity/how to best fix the problem.
Part 2 : 8 Examples of Incident Management
We’ve listed a set of common incidents which could severely impact a business’ capacity to function.
| System Outages | Whether caused by a technical fault or power failure, system outages can immediately halt production/the provision of services. |
| Data Breaches | Incidents where an unauthorized actor(s) gains access to restricted data/information. |
| Device Failure | A device connected to the corporate network fails in some way, unable to fully perform as required. In this scenario, remote management device management tools can be utilized in order to resolve this issue (more on MDM to follow). |
| Hardware Failure | This type of issue specifically relates to the condition of the hardware or ‘shell’ of the device, as opposed to the functionality of the asset’s applications. |
| Software Bugs | A virus that attacks software within a device, therefore undermining the user’s ability to use corporate platforms/programs. |
| Help Desk Disruption | Accountable for dealing with customer issues and complaints, helpdesks are vital components of a business’ service proposition – therefore, if this department is struck down by a systems issue, the repercussions could be severe. |
| Network Connectivity | If employees cannot successfully connect to the corporate network, it’s unlikely they will be able to deliver all required tasks. |
| Employee Negligence | Should an employee fail to take the appropriate steps to protect a device, make a technical error, or blatantly disregard their duties, a critical risk to the operation could easily materialize. |

Part 3 : Incident Management Process: 8 Key Steps
In the previous section, we’ve discussed the three components which must be considered in the creation of an incident management plan – but how does a company harness various elements when attempting to formulate an effective response to a security threat?
We’ve provided a guide below to illustrate incident management process steps:
- Step 1.Incident Detection
- First and foremost, IT security analysts seek to understand the type of issue which has occurred.
- Step 2.Notification
- The internal alarm system is triggered, notifying relevant stakeholders of a major incident.
- Step 3.Categorization
- Once the problem has been diagnosed, IT teams can make an informed judgement on the extent of the risk – the incident’s ‘categorization’ determines what remedial action needs to take place.
- Step 4.Prioritization
- This process encourages IT teams to breakdown the issue into bitesize chunks, and address their most pressing concerns first. It may also result in other departmental areas of the business receiving less focus, as additional resource is mobilized to help quell the immediate threat.
- Step 5.Task Assignment
- Individuals responsible for delivering specific elements of the co-ordinated response approach are identified and briefed.
- Step 6.Response
- Agreed workflow actions are implemented.
- Step 7.Resolution and Closure
- The threat is nullified, and operational systems are once again performing at full capability. If an IT ticketing process is in place, any notes on the system are marked as resolved.
- Step 8.Analysis
- IT teams conduct a thorough probe into what caused the event, recording as much relevant data as possible. Any learnings taken from this analysis are used to help adjust/improve future response activity.
Part 4 : Best Practices to Create Incident Management Workflow
Composing a credible, relevant, and effective incident management plan is in no way an easy task. Indeed, given the inherent complexity of IT infrastructures, which facilitate intensely inter-connected systems and support a wide variety of technological equipment, business continuity experts must ensure responses are robust, adaptable, and suitably detailed.

When pulling together a set of incident report policies, businesses would do well to consider the following tips and best practices we’ve provided below:
1Define clear roles and responsibilities for Incident Manager and response teams.
This may seem an obvious thing to consider, but in a highly-charged environment, individuals can often falter under pressure when unclear about their own role in the resolution process.
In order to ensure maximum accountability and transparency of duties, the responsibilities of each response team member (including the Incident Manager) should be publicized. This also helps individuals understand which colleague to report to/communicate with when specific situations arise.
2Establish a standardized incident classification system.
As alluded to earlier, in order to calibrate the correct level of response, threats must be filtered through an appropriate classification system. A set of pre-determined indicators should be used to help accurately categorize each risk, which compel IT teams to consider stakeholder impact, operational functionality, and brand integrity.
3Develop a comprehensive incident response framework.
In order to optimize the quality and efficiency of their response to cybersecurity attacks, it’s highly recommended that businesses deploy a remote mobile defense management system. These sophisticated platforms empower companies to protect networked devices without having to undertake any type of manual intervention.
Indeed, remote MDM’s can independently detect, diagnose, and address risks to security, providing relevant updates to IT teams along the way. Furthermore, they can ‘push’ tailor-made security profiles and policies onto specific or groups of devices, ensuring company assets are primed to handle common environmental threats, and end-user access to confidential corporate data is controlled.
Below, we’ve highlighted several of the defense mechanisms integrated into remote mobile device management systems – each of these are specifically focused on protecting company assets:
Main MDM Features for Incident Management
- Remote device lock/wipe
In instances where unsavoury actors have infiltrated a device, actioning a remote lock ensures no applications, software, or operating system settings can be accessed. Similarly, when a remote wipe is performed, all stored data is instantly removed from the device, preventing the user from exploiting or sharing sensitive corporate information. - Alerts & Workflows
Pre-established security profiles, customized by internal IT teams in order to best handle prevailing threats to company networks, determine how a remote MDM system responds to suspicious device activity.
Notifications (or ‘alerts’) inform relevant stakeholders that an incident has occurred, and confirm what action has been taken, if any, to address the issue. The nature of this action (or inaction) is dependent on the workflow response setting (i.e., how IT teams have set-up the system to react to specific incidents). - Geofencing
This feature enable IT teams to construct virtual boundaries in geographical locations, which help to identify when a corporate device has become lost or stolen. The relevant stakeholder is notified as soon as a device strays outside the pre-determined ‘safe zone’ pre-empting a swift investigation and (hopefully) positive resolution.
4Establish escalation procedure and ensure smooth communication channels.
As well as being provisioned to directly tackle threats that materialize within corporate networks, pre-installed security profiles also instruct remote MDM systems to escalate specific risks when unable to deliver a solution, or when activity requires some form of human intervention.
Businesses should ensure they have a clear internal escalation process, with relevant stakeholders notified dependent on severity level. An agreed method for communicating issues should also be in place, which sets out how to connect with the right people at the right time.
img-review and improve
5Reviewing performance, and subsequently creating a plan for improvement.
Whenever a major incident occurs, it’s vital that businesses reflect on the quality of their response, investigating the impact any preventative measures had on external parties (i.e., clients, suppliers, vendors), internal employees, and of course, the general operation. When this piece of work is completed, a suitable incident management process improvement plan can be created, detailing areas of the incident management process that require further attention, and any important learnings from the event.
6Regular training.
Establishing a comprehensive internal training programme ensures employees keep relevant knowledge up to date, and acquire new skills and expertise. As a result, IT operatives are better equipped to deliver their role, and are well-positioned to protect the business from current security threats.

Part 5 : 5 Incident Management Process Improvement Ideas
1) Streamline Incident Reporting Process
Simplify the steps involved in incident reporting. And, to establish a quick-and-easy mechanism entry, such as a self-service portal or mobile app.
2) Automate Classification and Ranking
Utilizing AI learning algorithms and cloud computing are effective ways to reduce time, and, further, to figure out solutions faster.
3) Use Point-to-point Incident Management Software
Since unexpected issues are different and happen across various carriers. Use oriented tools can better solve problems.
For instance, AIOps platforms for cause analysis and monitoring; on-call scheduling tools for alert routing and communication; mobile device management solutions for COBO/BYOD devices issues; remote device management solutions for commercial equipment malfunction; etc.
4) Develop a Knowledge Base
Build up a knowledge repository to save occurred incidents, solutions, and best practices. This helps identify similar incidents and make a faster problem-solving plan.
Some MDM solutions are available to create one which applies Chat AI.

Part 6 : Incident Response Plan Example: How to Use MDM Automated Workflow
Incident management includes fields from hardware to software. Devices, as one of the management objects, also require an incident management strategy. To impletement the incident management process, device management solution might be the best tool to help.
A mobile device management solution is able to set up automate workflow and take actions. Here are some examples of using incident response workflow.
Before starting, you need to have a AirDroid Business account and enroll device to the organization. Learn MDM enrollment.
How to set up MDM automated workflow for security incident?
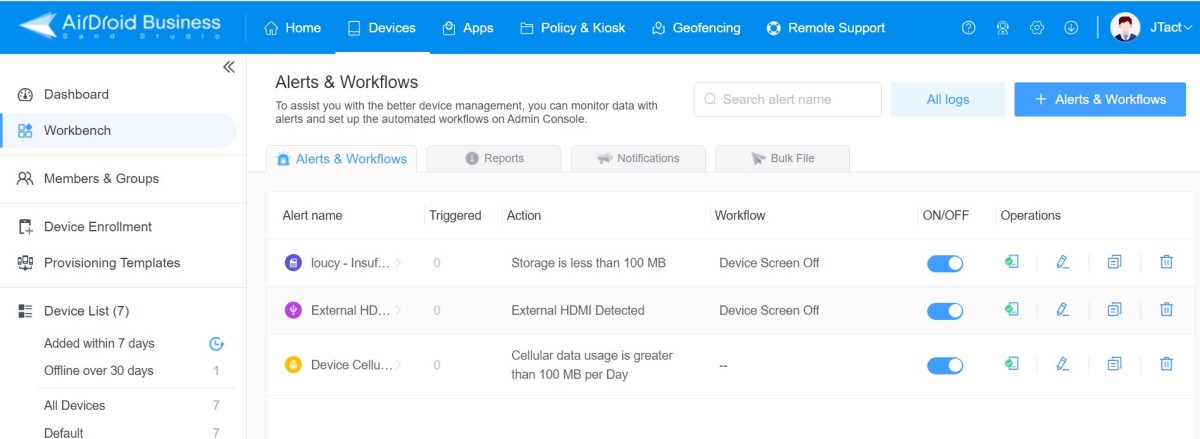
- Step 1.Create alerts to receive notifications.
- Find the menu in the admin console: Device > Workbench > Alerts & Workflows > + Alerts & Workflows.
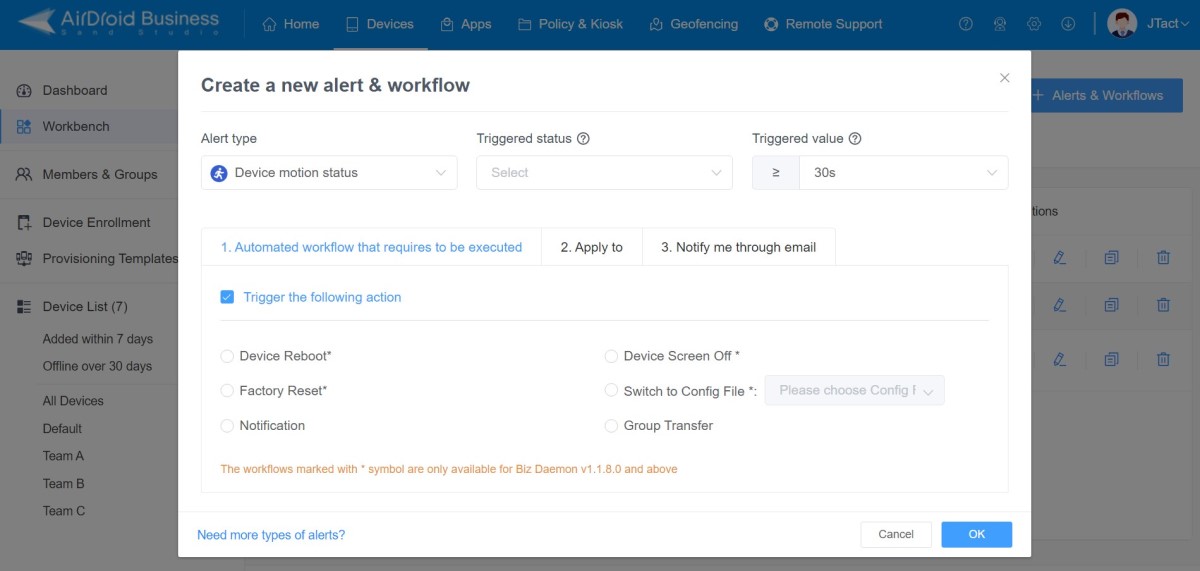
- Step 2.Choose alert types and set up trigger conditions.
- There are more than 15 types to choose from. For example, you can choose 'Device motion status' and set up moving as the triggered status.
- Step 3.Configure automated workflow.
- Workflow actions contain factory reset, screen off, reboot, and others. You can also use Policy file as the automated workflow.
- Step 4.Apply preset the alert and workflow to devices.
- Click 'Apply to' and choose device groups.
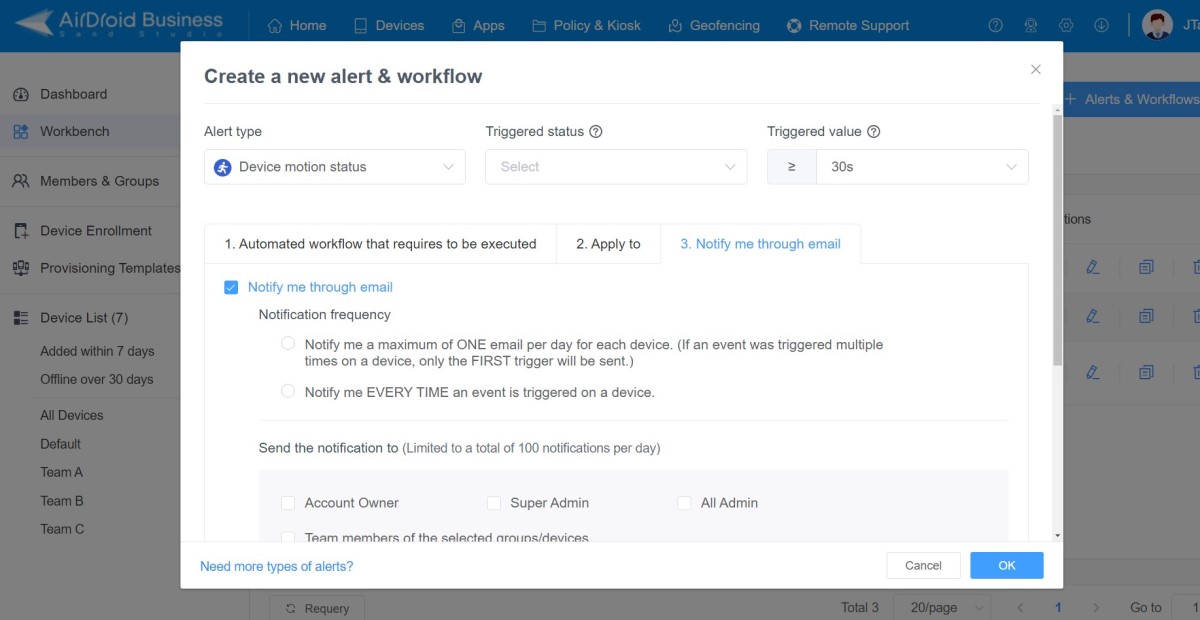
- Step 5.Receive notifications via email.
- Click 'Notify me through email' to set up notification settings. This way, you will get noticed once the alert is triggered.
Part 7 : Why Do Businesses Need an Incident Management Process?
So, why is it so important for businesses to install an effective incident management process? What are the potential repercussions of not being able to reduce the risks associated with the outbreak of a major incident?
In the points below, we provide an answer to these pressing questions, and in doing so illustrate just how vital a clear, efficient, and fit for purpose incident management plan can be.
- The average cost burden of succumbing to a data breach was $4.24m in 2021, a substantial increase on the previous year.
- It’s understood that approximately three-quarters of organizations have an incident response plan in place, but only 54% have assessed its durability in the past twelve months – businesses must regularly strength-test their incident management process and make necessary adjustments in order to maintain its relevance.
- In 2020, a colossal 64% of corporate entities experienced an event which required them to initiate their respective incident management response procedure.
- According to IBM, it typically takes businesses 277 days to identify and contain a data breach – possessing an appropriate incident management plan can reduce this timeframe significantly.
FAQs
IM (Incident Management) – The process used by businesses when attempting to resolve issues causing operational disruption.
ITSM (IT service management) – The process used by businesses to identify, organize, and deliver customer support solutions.
ITAM (IT asset management) – The process used by businesses to provision, maintain, and update company assets, whether that work is performed in relation to devices, networks, or other IT-related properties.
ITIL (Information Technology Infrastructure Library) – A comprehensive guide to a business’ IT infrastructure, which is used to help swiftly identify, diagnose, and resolve issues which emerge on corporate networks.






Leave a Reply.