- All-in-one Android MDM Solution
- Remotely Access and Control Android Devices
- Kiosk Mode for Dynamic Business Needs
- Monitoring, Alerts, and Automated Workflows
- Device Location Tracking & Geofence Alerts
Best Practices to Ensure the Security of IoT Devices
What are IoT & IoT Security?
The term Internet of Things (IoT) refers to the interconnected network of devices, appliances, and other things outfitted with electronics such as sensors, processors, wireless network modules, and other similar components.
IoT security refers to the measures used to prevent unauthorized access to, or manipulation of, connected IoT devices in the physical world. IoT security aims to ensure IoT applications' availability to authorized people continuously. It also provides a check on the confidential data not being breached by anyone and provides consistency and accuracy of data. Let's discuss IoT security best practices in this article.
- 1 : Why IoT Security is Important?
- 2 : IoT Use Cases in Different Industries
- 3 : Potential Threats of IoT Security
- 4 : Best Practices for Reduce the Risk of IoT Security

- 5 : Cases of IoT Security Vulnerabilities
- 6 : IoT Security vs. Traditional IT Security
- 7 : Recap - Security Tips for IoT
- 8 : Related Questions of IoT Security
1 Why is IoT Security Important?
The use of IoT devices has increased so much that we will find them in every industry, from domestic to commercial sectors. Almost all businesses rely on IoT devices; even people's lives are somehow connected to some IoT applications.
For example, IoT devices installed in smart cars to provide driverless service must be 100% secure. Any cyber-attack can disturb its functions and hence cause an accident. Similarly, large enterprises that use IoT devices have confidential business information. If a cyber-criminal attacks an IoT device with no security measures, it can breach the information and cause a great financial loss.
2 IoT Use Cases in Different Industries
IoT applications are used in various industries to ease man's work. IoT devices are helping industries by providing predictive maintenance, smart metering services, remote monitoring and controlling and energy optimization.
Retail
The applications of IoT are increasing day by day in the retail industry. Location tracking for delivery operations is one the best and most effective ways to manage the deliveries and provide appropriate feedback for the delivery status including time.
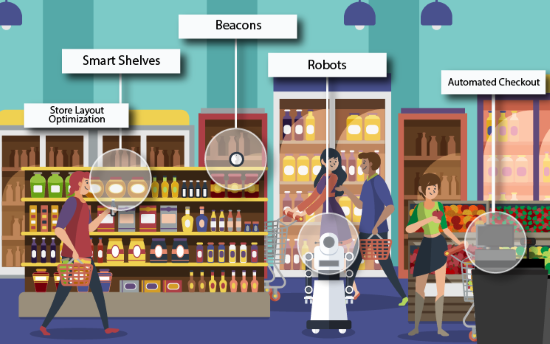
Another application of the IoT in retail the inventory management. Things are arranged in a more sophisticated way so that they are easy to find. With the help of sensors, it is easy for managers to find the products that generate more revenue and user-activity heat maps help manage the space efficiently.
Healthcare
Healthcare IoT devices are the most trending technology used worldwide to examine health-related factors, and their use is predicted to increase more in the next few hours. From the growing trend, it is predicted that in 2026 the value of these products is to reach $176 billion.
Various healthcare operations are performed using IoT services; from which the most crucial and common one is the patient's remote monitoring. The IoT device measures various healthcare factors like temperature, heartbeat rate, and blood pressure, and the data is shared with a software application from which experts can fetch the data and prescribe the patients accordingly.

It eliminates the need for travelling to doctors every week. IoT devices help patients monitor their glucose level continuously, while normal tests only tell the glucose level at the time of the test. Mood-aware IoT devices help doctors to understand the depression level of patients more accurately.
Transportation & Logistic
Transportation and logistics are highly asset-intensive industries like manufacturing. So, to secure the assets, a connected network is used to manage the whole system minimizing the risks of loss as trucks and vessels are the moveable assets of these industries and the most crucial ones.
Hence it is necessary to provide a complete network to track the assets from all endpoints. Experts have described four pillars of the logistics industry, i.e. communication system, vehicle tracking, supply chain management and IT security. The interesting thing is that IoT devices have controlled all these four pillars in their hands.
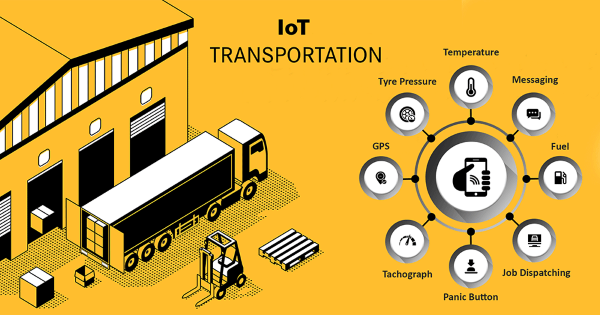
Trucks are the lifeline of the logistics industry. With the help of the location and route management system of IoT, the logistics industry has come into safe hands. Managers can easily track the location of trucks. With the help of IoT predictive maintenance, the logistics and transportation industry can identify defects before time.
Government
The use of IoT devices in the government sector gives the government more potential to control the whole country. With the help of IoT, data collection in any sector is transformed with modern techniques.
An increase in IoT deployment increases the opportunities for jobs in the IT industry and other industries like manufacturing and production. IoT sensors can help the government in various surveys in less time.

City management and planning can be perfectly done by installing IoT sensors all over the city. Issues like waste management, population rate, water and food supply system, transportation and public property can be handled smoothly using IoT sensors.
Warehousing
Management must adopt the latest technologies to establish a successful business. For that purpose, ignoring the IoT advancement in the warehousing industry would be inappropriate. IoT helps collect various measures and data about the warehouse with sensors and robots.
IoT warehouse management solutions provide the best mechanism for asset tracking and management. Data analytics by IoT management solutions provides a clear image of future business plans.

3 Potential Threats of IoT Security
Although IoT devices have supported almost all businesses, there are potential risks to using IoT devices. The first thing is to know what risks businesses face while using IoT devices, and then we will move towards a secure IoT network that could overcome these threats.
Here is a list of potential threats with IoT devices:
1. Lack of Supervision and Management
Lack of supervision and management can lead to IoT failure. If IoT devices are not managed properly, they can stop processing, and a minor fault in the device can lead to processing failure.
As time passes, new vulnerabilities are discovered. A software update is a necessary element to overcome these threats. Secure devices can become unsecure if not updated with the latest software version.
2. Weak Passcodes
IoT devices come with default passcodes. Mostly IoT managers ignore the threat of passcode and keep them the same. Hackers are smart enough to find such codes as they are experts in this work.
It is very important to set strong passcodes that are impossible to guess. There should be a proper set-up for the expiration of passcodes; otherwise, it can lead to a great loss depending on the IoT device's purpose.
3. Insecure Data Storage & Transfer
Lack of data encryption seriously threatens the confidential data in IoT devices. It can cause a great loss of the privacy of the business. If the data is not encrypted, hackers can access the network and breach all the personal data stored and shared from IoT devices.
4. Inadequate Privacy Protection
Users only use the services if they are ensured that the system is secure. Businesses know the system is at great risk without adequate privacy protection. If IoT devices are left with inadequate privacy protection systems, users will never prefer such IoT devices as they can cause loss to them.
5. Untrusted Deployment Locations
The location of deployment of IoT devices is a key factor for their security. Hackers get the I.P address of IoT devices deployed in public places enabling the hackers to bypass the security system of IoT devices easily. Sometimes, IoT devices are located in insecure places, creating a space for hackers to attack them easily and misuse them.
4 Best Practices to Reduce the Risk of IoT Security
To reduce the risk of IoT security, IoT best practices are necessary to implement and monitor. These practices involve manufacturing, development, deployment and monitoring processes.
1. IoT Hardware Manufacturer
IoT hardware manufacturers are the people associated with manufacturing the hardware of IoT devices. IoT hardware is a structure that involves an electronic device to connect and share things on the internet.
For best hardware manufacturing, always keep following points in considerations:
Design of hardware must include minimum features to operate it. Installation of keyboard keys, USB ports, and mouse should be installed only if required as they may increase the risk of cyber-attack.
If devices are built with cryptographic assurance of firmware versions and encrypted upgrade pathways, they may remain safe. Make sure the hardware components installed in the IoT device are physically secure by using alerts.
When someone tries to remove it, operators may get alerts about it. Construct Trusted Platform Module-based security features like encrypted storage and booting. These additions strengthen the security of devices and contribute to the safety of the Internet of Things as a whole.
2. IoT device Solution Developer
Methodology for Software Development
Developing safe software demands considering security from the roots, from the beginning of a project through its development, testing, and eventual release. This approach affects the selection of platforms, languages, tools and various software solutions.
Developing safe software is scaled into manageable steps utilizing Microsoft's Security Development Lifecycle.
Selection of Open-Source Software
With open-source software, it's possible to create new tools very rapidly. The amount of community involvement in each open-source module should be taken into account when making a decision on which open-source software to use.
An active community helps in updating the latest issues and bugs to keep them resolved otherwise if an open source with an inactive community is used, issues will remain unclear and hidden.
Integration
Take caution while integrating libraries and APIs, since this is a common entry point for software vulnerabilities. The API layer may provide access to features that aren't strictly necessary for the present deployment.
If you want to ensure everything stays safe, you need to ensure the integrated components don't have any security issues in their interfaces.
3. IoT Solution Deployer
IoT solution deployers have a key role in securing IoT devices. Two things that you must consider while deploying IoT solutions are:
Secure Hardware Deployment
IoT devices are mostly used in places and are open to use by anyone for a specific purpose. The only solution is to ensure that the hardware of the IoT device is tamper-proof as much as you can so that no one can take out any of its parts. Also, ensure secure additional features like USB ports must be secure from any external attachment.
Authentication keys
Keep the authentications and IDs private and make sure no one can access them. Otherwise, there is a definite risk of a breach of privacy and a great loss. They are also of great importance even after the deployment, so never leak them.
4. IoT Solution Operator
The security factor is a key factor that remains active even after deployment. It can even not be neglected after the device is permanently stopped. Most important is to manage the security after deployment when the device is in use.
Choose the best IoT solution operator for IoT device monitoring and security. AirDroid Business is the best solution operator that is used for Android devices. For other devices, you may use AWS and Azure solution that provides secure IoT management and security features.
AWS IoT is perfect for all large and small IoT applications due to its comprehensive features. Azure IoT has enhanced categories that support various IoT operations, including deploying IoT devices. An ideal IoT solution operator must have the following properties:
Real-time Monitoring & Set Alerts: Choose an IoT operating software that perfectly monitors all the security factors of your IoT devices. You can easily manage the real-time monitoring with IoT software. Users can also set alerts for various security conditions to get notifications for immediate actions.
Using Encryption Protocol and Secure Passcodes: The software solution must support the encryption protocols and provides secure passcodes that are unable to break.
Keeping IoT Software Up-to-date: Unlike mobile devices, software auto update feature is hard to manage in IoT devices. With IoT software, managers can automatically update the IoT devices.
Protect Both Data in Transit and Data At Rest: Manager needs to choose a platforms to provide data encryption to protect the security of the data during file sharing. For Android devices file sharing, we recommend AirDroid Business, which uses TLS encryption protocol to protect the connection to ensure data security.
5 Cases of IoT Security Vulnerabilities
It is obvious that managing the security of IoT devices costs a huge amount; even after that, there have been several cases where big-budget security devices were hacked in the past.
In the past few years, we have found some instances that are clear examples to justify IoT security vulnerabilities. Mirai Botnet attack in 2016 clearly shows the threats of cyber-attacks on IoT devices.
All major services were temporarily blocked due to the Mirai attack. The Mirai ransomware briefly disabled multiple high-profile services. The approximate number of affected devices is 60,000. Similarly VPNFilter malware attack in 2018 effect around a half million routers.
The malware was shared with the other devices connected to the router, and information like passwords was breached. It enabled the hackers to steal some sort of data and makes the devices unusable.
One of the instances happened in 2020 when a cyber-security expert hacked Tesla Model X in just 90 seconds. A lot of Tesla cars were automatically controlled and stolen. In 2021, Swiss hackers hacked around 150,000 live cameras of a camera firm named Verkada, which were installed in public sectors.
6 IoT Security vs Traditional IT Security
IoT security must be stronger than traditional IT security as IoT devices have to deal with the physical world. IoT security is a fusion of cyber-security with various disciplines, while traditional IT security is cyber-security. Traditional IT security systems have failed in providing security to IoT devices. Hence, separate security measures are introduced for IoT security.
How do Hackers Enter Networks?
There are various ways by which hackers can enter the network:
Lack of Multifactor authentication (MFA), enable hackers to attack easily when they have a good technical command of various hacking techniques like phishing and trusted relationships.
Outdated software can be a reason to enter a network via exploits. Hackers that such software gets access to the networks. Vulnerabilities scans are there to help find unsupported software.
Default passwords and user names are easily available around the internet. So, if a strong password is not set up, there is more chance for hackers to enter the network.
VPN is the easiest way hackers use to access any network as they are poorly designed and can be easily used to access networks. Unprotected cloud services are also a major source for hackers to attack any network.
7 Recap - Security Tips for IoT
We can see the use of IoT devices in every industry, including healthcare, transportation and manufacturing. Their security has always been a serious concern for all businesses equally. To keep the IoT devices secure, you must keep the software of IoT devices updated with the latest Version; otherwise, hackers will easily attack your IoT device.
While purchasing a new IoT device, keep yourself aware of its security features. Always deactivate the unused features of IoT devices as they create a space for hackers to attack. Abrogate the third-party access when it is of no use. These tips will help you in securing IoT devices.






Leave a Reply.