How to Encrypt Mobile Devices with MDM
Part 1 : How to Force Encrypt Android Device with MDM (Step-By-Step)
MDM can help with data encryption among mobile device. Usually, it uses Policy to enforce the encryption.
The feature ‘Mandatory Storage Encryption’ is a very important safety feature to keep corporate data secure.
There are also requirements to use the ‘Mandatory Storage Encryption’ features. You must have the following requirements to force encrypt Android devices with an MDM:
- An MDM admin account
- An Android device that runs version 6.0 and up.
- A controlled end app installed on the Android device
Once you have these set up, you can move forward with encrypting the Android device.
- Step One:Enroll the device in an MDM
- The device needs to be enrolled in an MDM in order to be controlled.
- The specific steps are as follows: Admin console > Devices > Device Enrollment > Device Owner (recommended) > 6 times Tap.

- Step Two:Create Policy Config Files
- Creating the Policy Config files establishes the parameters of control over the device. The file can be used to enable and disable certain settings on the device.
- And the feature ‘Mandatory Storage Encryption’ for mobile data encryption is placed in: Policy & Kiosk Config Files > + Create Config File > Policy > Restrictions > Device Function > Mandatory storage encryption.
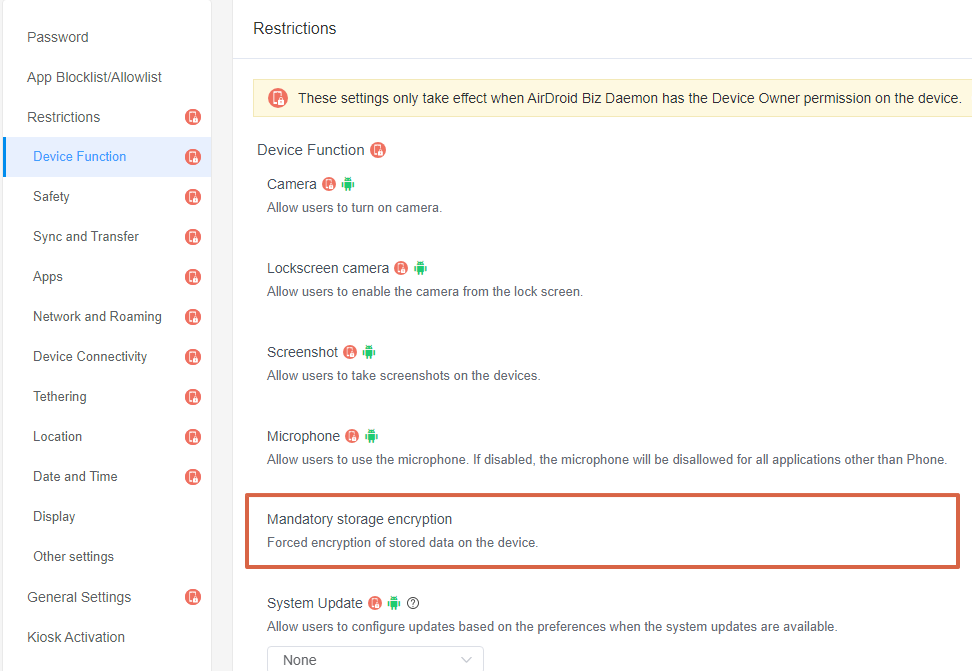
- Step Three:Apply the Policy Config File to the Device or Device Group
- As the policy of MDM encryption activate, you will see no document (all device info is invisible ) when you connect the device with PC. And of course, you cannot export any data.
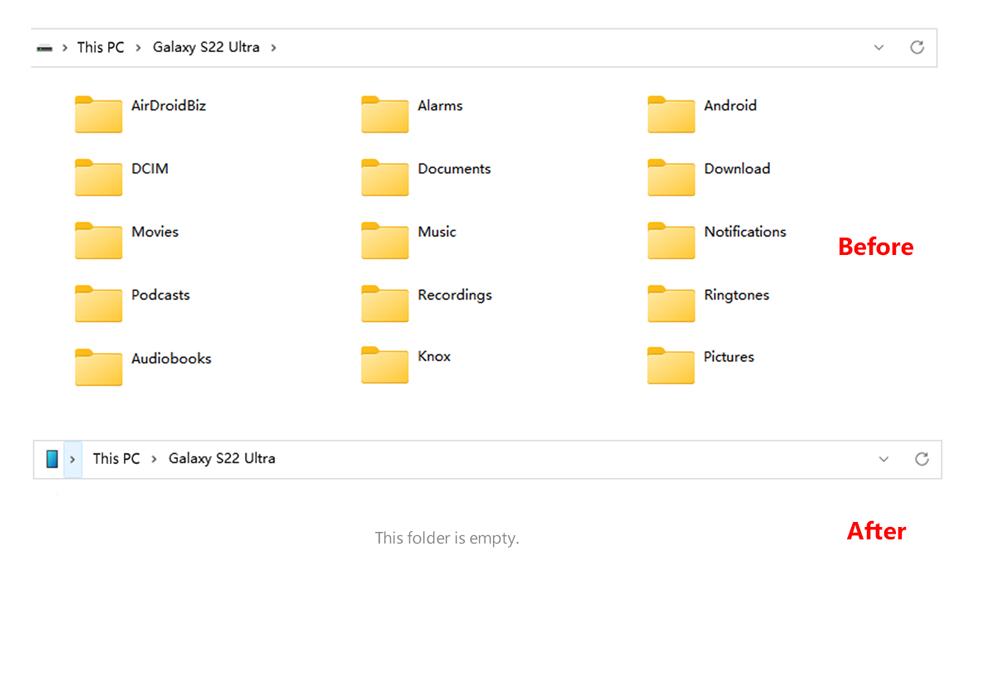
- Learn MoreWhat if someone force cracking the device and exporting data?
- Data in files will show as disorderly code and unreadable.
Other MDM Features to Secure Mobile Device Data
- 1) Password Policy
- 2) Auto Screen Lock or Device Factory Reset
- 3) Clear App Data and Cache
- 4) File Transfer with TLS Encryption
Enforcing password complexity rules helps to keep mobile devices more secure and less likely to be used by bad actors.
You can use Auto Screen Lock or Device Factory Reset to secure devices that may have fallen into the wrong hands.
You can also clear application data and the cache to destroy data on a device. This can be done remotely through the mobile app management feature.
Finally, you can also complete file transfers with TLS encryption through an MDM solution to ensure data is safe and secure while being moved from one device to another.
Part 2 : How Does MDM Encryption Work?
Let’s explore the different ways that MDM can help you encrypt device data. Take AirDroid Business as an example.
1) Data Center
AirDroid Business uses Amazon Web Services (AWS) as its cloud infrastructure host, which keeps customer data completely secure. AWS has top-of-the-line protection and security measures, such as firewalls, data encryption, DDoS mitigation, and securely located servers. By using AWS, AirDroid Business ensures that customer data is encrypted.
2) Server Session Encryption
Usually, those MDM solutions use secure connection types to connect users to the servers. Most of the connections connect through TLS, while the others connect via TCP or UDP.
AES (256-bit) session encryption is also used for connections, as well as RSA public/private keys, which are closely related to https/SSL security standards.
For each server session, AirDroid Business uses the most secure security standards with its routing and encryption.
3) Password-based Encryption
Additionally, password-based encryption is used by MDM to maintain secure connections with one-way hashing. AirDroid has an airtight password policy, with recommendations for password security thresholds and custom password rules.
4) Backups
Additionally, all of data backups are encrypted and stored separately to preserve them and keep the data safe. Servers and storage centers are extremely secure and contain cameras to ensure customer data security.
These backups are also regularly deleted from time to time to manage the lifecycle of data and not keep unneeded data.
5) Payment
No payment information is stored on servers. Instead, most MDM solutions use Payment Card Industry Data Security Standard (PCI) compliant third-party companies.
Part 3 : What is the Default Encryption on Android?
Android data encryption has two different default encryption methods depending on the device. These methods are known as full-disk encryption and file-based encryption. Full-disk encryption has been replaced by the newer file-based encryption on new updates and devices.
1 Full-Disk Encryption
This method of encryption comes as default on Android devices that are running Android 5.0 up to Android 9.0. It uses an encryption key to encrypt data that is created on the device. This encryption key is able to be found only after entering the device password. Full-disk encryption uses a 128-bit master key based on the PIN, password, or pattern of the device.
2File-Based Encryption
On Android devices running Android 7.0 and above, these devices use the default method of file-base encryption, also known as FBE. Rather than encrypting all content on the device through one key, file-based encryption encrypts different files with different keys. This method of encryption is more secure, which is why Android switched to it for its newer devices.





Leave a Reply.