- Disable network sharing(hotspot, bluetooth and USB tethering)on devices to prevent unauthorized access.
- Set up Wi-Fi configurations for batch devices from a single dashboard.
- Configure the use of VPN according to the needs of the company.
- Remote access devices to diagnose and resolve network issues.
Comparing MDM and MAM in Cybersecurity [2024]
Mobile application management (MAM) solutions are limited to protecting apps when it comes to cybersecurity. With an MAM solution, businesses can prevent the installation of dangerous apps, remove apps on-demand, and wipe out any data from a device's apps.
However, an MDM is a more robust cybersecurity solution. Businesses can enforce security compliance around the entire device, network security for its operating environment, and take more actions for lost or stolen devices.
1 MAM vs. MDM in Cybersecurity
1.1 Security Compliance
MAM in security compliance
With a MAM, security compliance is limited to apps.
IT professionals may prevent the installation of apps that pose a security risk, such as vaporware.
They may also remove apps that are later found to be dangerous, such as legitimate apps that are revealed to have serious vulnerabilities.
Between the two extremes of prevention and removal, IT teams can also control how much employees can use a particular app, such as by implementing a threshold.
Security compliance with an MDM
An MDM can perform all the app-based security compliance that an MAM can and more. These requirements are governed by an overarching policy that defines compliant behaviors.
For example, enterprises can require employees to set a passcode for a screen lock. The device's apps will be blocked if the employee does not follow within a certain period.
These restrictions are fully customizable and encompass all device functions. Enterprises can not only require a password but also determine the exact parameters for length, complexity, limits to repeated characters, and validity.
Enterprises can set even more advanced requirements in security compliance with an MDM. They can prohibit the use of USBs to mitigate the threat of data loss through unauthorized file transfer.
They can block the use of the camera in general or only for the lock screen to keep employees focused on work activities.
They can prevent users from initiating a factory reset of the device.
1.2 Network Security
MAM in network security
An MAM does not directly enhance network security. These solutions only indirectly aid network security through its app-related features.
By enabling businesses to control the installation, use, and removal of apps, they help prevent malware, viruses, and other threats that can compromise the device and, in turn, network security.
An MAM has, at best, a tangential effect on network security.
Network security with an MDM
In contrast to an MAM cybersecurity, an MDM contributes directly to network security. The company can create a dedicated operating environment for devices to operate on.
For example, an IT professional can specify what WiFi networks a device can use so that they can only be limited to those belonging to the company headquarters or any of its satellite offices.
To secure corporate data, the business can customize the dedicated operating environment by specifying the access point name, time zone, language, or VPN. This dedicated operating environment can be suited for different use cases.
A company can require that app updates be done over WiFi to ensure these are done on a stable connection.
1.3 For Lost or Stolen Devices
When devices are lost or stolen, companies that rely on an MAM are limited in their responses. In contrast, companies that depend on an MDM have a much broader suite of options.
'MAM cybersecurity' for lost or stolen devices
If a device is lost or stolen, the business can remotely wipe all the data from the device's applications. This action will prevent third parties from accessing company emails, communications, deliverables, and other sensitive information.
The problem is that most users store data outside of applications, including photos, videos, contacts, documents, systems settings, and more.
There could be equally valuable information here. For example, an employee may store company credentials in a plain text document or maintain a list of external stakeholders in their contacts, a network that is also leveraged in some attacks, such as ransomware.
The MDM playbook for lost or stolen devices
Businesses have a much more comprehensive range of options for lost or stolen devices. First, they do not have to rely on employees to self-report a missing device.
The enterprise can instead set up a geo-fence around a general location, such as the city boundaries in which the organization conducts business. If a device leaves this geo-fence, the IT team will get a notification indicating a potential lost or stolen device.
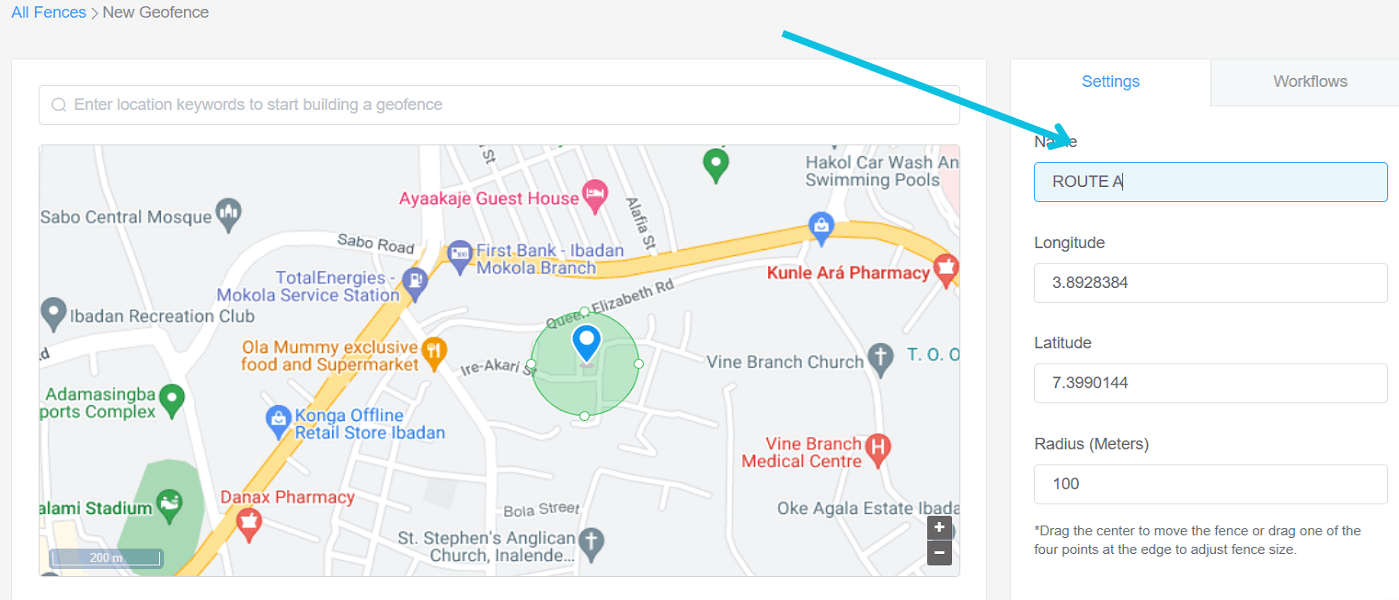
Upon receiving this notification, the IT team can further track the device to determine whether it is stolen. If the device is stationary at a remote work location, such as a client's office, the employee may have misplaced it. If the device is on the move in unfamiliar territory, a thief may have indeed stolen the device.
In the case of theft, the IT team can use the phone's camera to take remote photos of the person with the device and his surroundings. This information may be used to help locate the device's exact whereabouts as well as to preserve evidence against the perpetrator.
If there is little hope of recovery, the IT team can trigger Device Lock, Remote Factory Reset or enable Lost Mode. Unlike a remote wipe with a MAM cybersecurity, it will cover not only applications but also the entirety of the device - it will be restored to its original factory settings, exactly like it was when first taken out of the box. This complete erasure protects the organization.
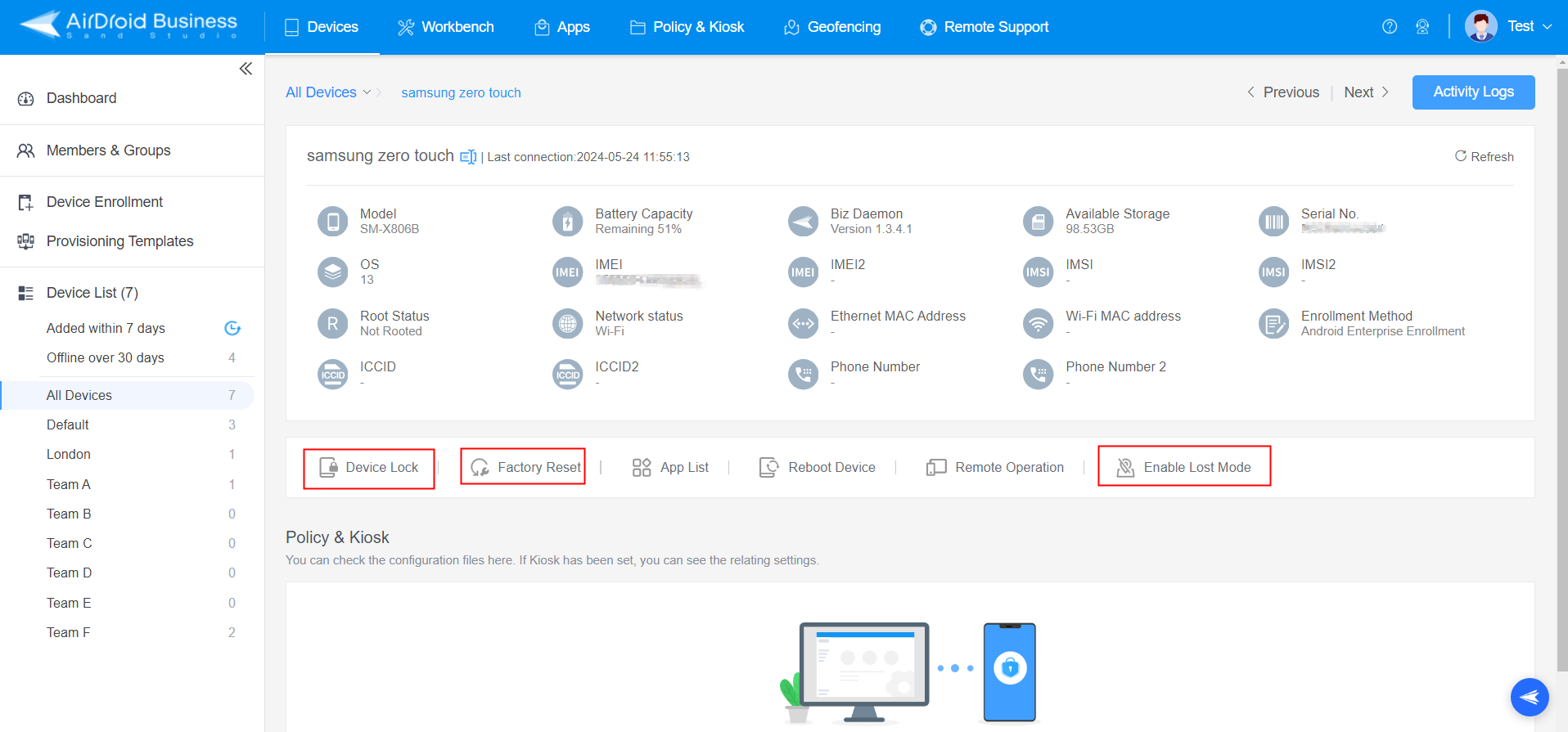
2 MDM Solutions Offer Greater Security
A famous saying is attributed to Henry Ford: "If you asked people what they wanted, they would have said faster horses." This thinking also accounts for why most businesses choose an MAM for cybersecurity.
Because most of work life is built around applications - employees email from Gmail, communicate on Slack, and meet over Zoom - IT professionals will naturally look for a solution that focuses on securing them. They fail to realize that devices have far more vulnerabilities than just the applications themselves.
- While working on the go, an employee may connect to the public WiFi of a cafe or coffee shop. These connections are insecure. The employee may expose their device to various possible attacks, such as a man-in-the-middle or evil twin attack. These security breaches may compromise their device and other networks within the company.
- Employees may get reckless by not setting a passcode to screen lock their phone. Because this employee is from human resources, a colleague may snoop through the device when it is unattended at the office. The snooping colleague may learn that layoffs are being considered and encourage their peers to resign.
- Employees in the field need to remember their devices at a restaurant. The person who finds the phone realizes it belongs to a famous tech company employee. Realizing this, he goes onto the dark web and sells the phone's data to a cybercrime syndicate before the employee can even report the loss to the IT department.
These are just a handful of scenarios that a MAM would not be able to protect organizations from due to their exclusive focus on applications. The much more secure choice would have been a mobile device management (MDM) solution.
An MDM is a much more secure strategy than an MAM. It encompasses the scope of a MAM by also being able to deploy, manage, and remove applications, but it extends much further toward all the other areas necessary to protect.
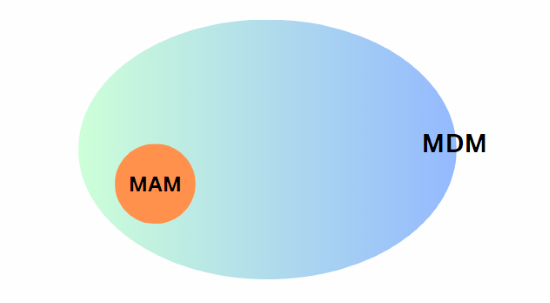
An MDM has a provision for network security so businesses can control the environments to which workers can connect. An MDM can also enforce compliance with security policies, such as requiring a passcode for a screen look. Finally, an MDM also has more options in the event of a lost or stolen phone, including restoring the device to its factory settings to protect company data.
3 Why MDM Bests MAM in Cybersecurity
Knowledge workers spend a significant amount of time on their phones in apps. Because of this orientation, IT teams automatically default to choosing a MAM for their organization's cybersecurity.
Unfortunately, this choice is short-sighted: A phone's apps are just one small part of everything that needs to be protected.
For this reason, an MDM like AirDroid Business is the superior choice for cybersecurity. Businesses can enforce much broader and more granular security controls at the employee level with an MDM.
IT teams can do everything from specifying the complexity of a passcode to blocking the use of USBs for file transfer.
IT teams can also control the operating environment, providing greater network security. A business can limit the use of devices to only specific operating environments, such as the WiFi of pre-determined offices, coworking spaces, or home sites.
These limitations prevent employees from using public access points that may expose the company and its devices to malware.
Finally, an MDM gives businesses more options in case of a lost or stolen device. A MAM can only wipe out data contained in apps. An MDM, in contrast, can remotely wipe the entire phone and take a series of escalating steps before then, such as tracking the phone via GPS and taking photos of the surroundings.
An MDM is a more intelligent choice for businesses concerned with cybersecurity. They can extend their impact beyond just apps and implement total device security. This shift in scope will keep the organization, its employees, and their devices safe from harm's way.






Leave a Reply.