Mobile Device Inventory Management: What is it & How to
What is mobile device inventory management?
Mobile device inventory management is a process that businesses use to organize, provision, secure, and track devices which are tethered to a corporate network.
Although smartphones are usually the most commonly-used devices on these networks, the monitoring of tablets, laptops, and desktop computers must also be considered.
In order to establish an effective device inventory management process, corporate entities must ensure they have a suitable mobile device management (MDM) system in place. An internal MDM platform supports IT teams to efficiently manage a corporate network, by enabling them to gain complete visibility of individual and group device performance and activity, addressing security threats and providing notification of action taken (or escalating risks to senior IT leaders when human intervention is required), and facilitating authentication controls when end-users attempt to access sensitive and confidential data.
What tools are used during the process of device inventory management?
There are various types of devices used in workplaces, offices, and dedicated business purposes. The following solutions are able to handle mobile asset management.
MDM (Mobile Device Management)
- Best for smartphones, tablets, rugged handhelds, and custom mobile devices.
- Compatible with Android and iOS.
- Available to configure and manage device system settings, apps, files, etc.
EMM (Enterprise Mobility Management)
- Best for smartphones, tablets, and laptops.
- Compatible with Android, iOS, MacOS, Chrome OS, and Windows.
- With more capabilities about app management and access management.
UEM (Unified Endpoint Management)
- Best for desktops, smartphones, and any other IoT devices.
- Compatible with Windows, MacOS, ChromeOS, Linux, Android, and iOS.
5 main mechanisms working on device inventory management system
In conjunction with their local mobile device management system, IT teams utilise a range of tools in the delivery of device inventory management. Whatever the tool is, all are for centralized set-up and monitoring.
In this section, we highlight several of these key mechanisms, and discuss their respective functions:
1 Device deployment and configuration
Before an asset is introduced into a corporate network, it must be suitably provisioned. This process enables the device to be receptive to the controls and features of the local mobile device management platform.
Pre-existing security profiles, which are tailored to the needs and requirements of the company they seek to protect, are pushed onto new devices prior to deployment. This ensures the device is equipped to handle the conditions of its operational environment, enabling it to perform its required tasks without succumbing to cyberthreats. Should there be a desire to alter settings at any stage, the MDM system can re-configure devices remotely, without requiring assistance from the end-user.
2 Security and access control
Given the increasing sophistication of cyberattacks, and the reliance modern day businesses have on the performance of their networked assets, it's essential that IT teams are in a position to protect devices against prevailing security threats.
Mobile device management features, such as policy, remote data wipes, kiosk modes, and the aforementioned allocation of bespoke security profiles, are key to realising this objective.

3 Group devices
Companies may opt to categorize devices based on the authority level of the end-user, or the department in which they work. This enables IT teams to ensure specific devices can be mobilised to serve a particular purpose, and prevents employees without the relevant permissions from accessing confidential corporate data.
Once these groups have been created, devices can then be allocated dependent on the role and seniority of their intended end-user.
4 Track devices
In order to understand how assets are performing on the corporate network, and to mitigate against the threat of sensitive company information falling into the hands of illicit actors, IT teams must have the capability to consistently monitor the entirety of their device estate. This is achieved through accessing regular reports on the condition and functionality of single or groups of devices, and the use of geofencing technology, which alerts IT teams when an asset has strayed outside a pre-determined virtual boundary.
5 Maintain devices
MDM systems intervene to deliver remote remedial repairs to devices as soon as issues arise, enabling end-users to continually access all software without significant disturbance, and therefore supporting them to consistently execute their required tasks.
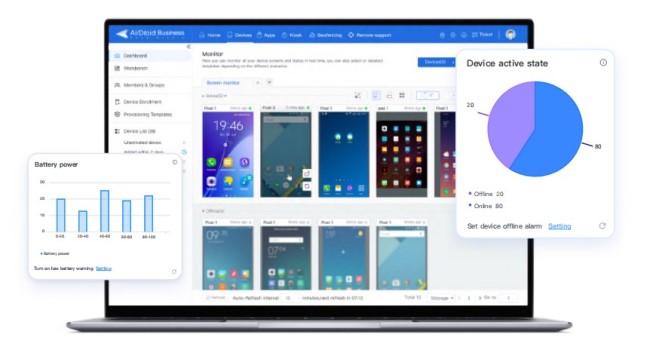
How-to: delivering device inventory management with MDM solution
The process for initiating device inventory management tools is dependent on the MDM solution being used. We’ve provided a step-by-step guide on how to deliver this whilst exploiting AirDroid Business, one of the marketplace’s most comprehensive mobile device management platforms.
1. Enroll device to the MDM console.
The MDM console is the central dashboard IT teams use to manage, monitor, and regulate the corporate device estate. Therefore, each new device must be enrolled onto this system.
There are several ways to enroll a device into the AirDroid console, including:
- Six-tap function
- Fully-integrated USB enrollment
- Android Enterprise enrollment
- Regular enrollment
However, please note that the first two options enable IT admins to automatically acquire the device owner’s permission for set-up (which in turn provides seamless access to configuration and kiosk settings), whilst using Android Enterprise requires the authorisation process to be conducted via Google Play. Therefore, six-tap or USB enrollment is recommended in this instance.
2. Preset device configuration with Provisioning Templates.
This action refers back to the provisioning phase discussed earlier, whereby devices need to be appropriately set-up before becoming active on the corporate network.
It should be noted that users are able to adjust pre-existing provisioning templates – enabling them to edit wi-fi settings and layer on any pre-configured applications – before downloading them onto the device.
To pre-set device configuration with provisioning templates:
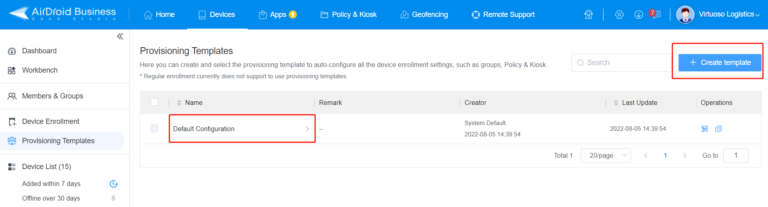
- a. Go to Admin Console > Devices > Provisioning Templates
- b. To edit a default provisioning template, click ‘Default Configuration’ Alternatively, to set-up a completely new template, click ‘+ Create Template’
- c. On the ‘Pre-install apps’ tab, users can select the applications they wish to automatically install onto the device.
- d. In ‘Other settings’ users are able to select several preferences for device use, including language, time zone, and wireless network mode.
After each of these relevant stages has been actioned, the user can then administer the provisioning template(s) to the device group or configuration file to which it applies.
By selecting device group, the device will be allocated to a pre-selected device group, which the user has earmarked – via the use of a QR code – for that specific provisioning template.
By selecting configuration template, the device will automatically be assigned to the ‘Default Group’ and be issued the pre-selected policy the user has earmarked – via the use of a QR code – for that specific provisioning template. However, if the user wishes to move the device to a different group, they can do so by dragging the device from the ‘Default Group’ tab, and placing it under the tab aligned to the desired group.
3. Track device status via Device Inventory report.
AirDroid Business’ comprehensive suite of reports allows IT teams to conveniently monitor the status and performance of all networked devices.
To specifically access the Device Inventory report:
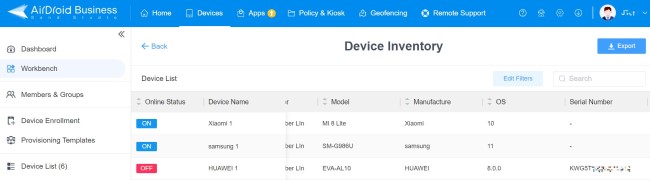
- a. Click Devices > Workbench > Reports > Device Inventory Report.
- b. Users can toggle the filter to hone in on specific elements. Report can be exported to a document, and therefore saved for administration/tracking purposes.
4. Update device list.
This function enables IT teams to ensure the profiles and permission settings of devices within a device group are appropriate for their intended end-user population.
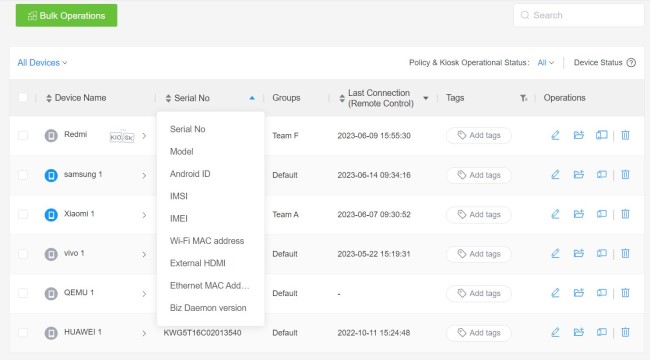
All enrolled devices and groups can be seen in 'Devices' of the console, including their details like Device Name, Serial No, Last Remote Control Time, etc.
Here you can take the following operations:
- Edit device profile and remark
- Move to a certain group
- Remote access and control
- Unenroll device
- Bulk operation
The role, function, and importance of Enterprise Mobility Management
In the previous sections, we’ve touched on the tools and features which are used by mobile device management solutions, and how these are harnessed in the delivery of inventory management procedures. However, these systems are only effective providing a capable, well-drilled, and highly-trained team are overseeing their use.
Enterprise Mobility Management (EMM) relates to the implementation of mobile device management platforms (and therefore by extension the integration of inventory management processes), and how IT administrators, specialists and senior business leaders ensure their methods for facilitating, monitoring, and utilising these systems are fit for purpose, and best support the demands of their clients, suppliers, employees, and any other relevant stakeholders.
A business’ EMM strategy should be underpinned by an agreed set of policies, which detail how the mobile device management system will be leveraged to serve the requirements of the organization, and the role each individual plays in achieving this end.
Why is device inventory management important?
There are multiple reasons why it is critical for modern-day businesses to implement an effective device inventory management process. It enables IT teams to:
- - Provision devices prior to them being released into the corporate network. This ensures that devices inhibit the necessary settings and applications in order to perform as their end-user requires.
- - Conveniently assign policies and profiles to specific device groups, and re-allocate devices within these groups at any given time.
- - Easily monitor device location, performance, and functionality within a corporate network, and alerts them (through geofencing technology) when assets are physically moved outside a virtually-constructed set of geographical parameters.
- - Understand the nature of current security threats, and therefore supports them to mitigate against the risk of falling victim to a cyberattack. In this way, it helps businesses keep sensitive data secure, and reduces the likelihood of operational disruption.
Frequently Asked Questions
In relation to the above, consider purchasing AirDroid Business – a mobile device management solution which is equipped with each of the aforementioned tools (and a lot more!)






Leave a Reply.