5 Best Examples of Mobile Device Policies
Mobile device policies refer to the instructions and rules created by each organization to manage and ensure compliance on all corporate devices.
These policies can apply to mobile devices, like smartphones, tablets and laptops, and are instrumental to a company’s security, data management, and continuous compliance with international and industry laws.
1What is Mobile Device Policy?
Mobile Device Policy is the term used for a company’s rules on managing mobile devices, including security policies and device function limitations:
Security Policy
Security policy pertains to the set of guidelines and rules that a company sets to instruct its staff members on how they should be handling their mobile devices during work hours and when it comes to using them for work.
Like password policies that affect how often passwords are changed, to policies about the type of data that can be shared and through what channels. And app allowlists which employed to limit the available apps installed on each mobile device.
Device Limitations
Device limitations unlike security policies are not instructional. Instead, they refer to a set of actions taken centrally by the company’s IT department to protect the company’s data.
Limiting the device functions on corporate devices, including the camera, microphone, and screenshot capabilities,etc. These restrictions prevent third-party unauthorized usage and data breaches to ensure compliance.

25 Best Examples of Mobile Device Policies
2.1Enforce Password Policy
For every company enforcing password policy can vary slightly, but more often than not it will include some configurations through the MDM software being used.
The options include:
- Use customized password: this allows you to establish rules for a device’s screen lock password and set complexity requirements for the type of password that can be used.
- Force password configuration: Blocks users from altering the configured password.
- Password removal: Removes the existing password and blocks users from setting up a new customized password.
Additionally, lock screen passwords can also be used to further enhance security. These measures are particularly important as they ensure that the devices and device data will not fall into the hands of people who are not authorized to access them. These additional protective layers can also come in handy in cases of theft or where someone is attempting to steal data from a device.
2.2App Allowlist
App Allowlist or Whitelist is used to limit the type of applications that their users can install and use on their devices.
These lists are essential as they ensure that data will not be shared through unauthorized or unsecured apps. It also helps protect devices from any apps that carry viruses and could end up harming the device in which they are installed.
Finally, they can also play an important role in ensuring that users will not be wasting their time on time-consuming apps that do not help them achieve their goals and company tasks.
2.3Restrict Network Sharing
While network sharing can have its benefits in allowing users to connect devices it also comes with many risks.
This is because any device that is connected to a network could gain access to company data that is stored on the device.
For that reason, MDM solutions, such as AirDroid Business allow companies to easily restrict network sharing through Hotspot and Bluetooth.
Restrict Network Sharing is especially important when trying to ensure that the company’s network remains secure and no unauthorized users will receive access to data they are not supposed to.
2.4Set Up Allowed Numbers
Configuring allowed numbers is split into configuring incoming and outgoing calls. This helps limit the possibility of any workers falling victim to scam callers, while also blocking them from receiving or having any calls with third parties that lack the proper authorization to receive data from the company.
Among these options, calls can only be configured to be allowed by users who are already on the user's contact list.
2.5VPN Configurations
VPN Configurations can be one of the most important security measures as they help ensure a user’s privacy when accessing the company network.
VPN configurations are necessary as they:
- Encrypts and protects data and information during the transmission process between devices in a corporate network. It further blocks unauthorized third parties from accessing it.
- Masks the IP address to encrypt the network connection, blocking third parties from tracking a user’s activity.
The mobile device policy includes VPN configurations, ensuring that company-owned devices connect to the Internet exclusively through the designated VPN. All Internet traffic is routed through a VPN, and the data is encrypted, which reduces the risk of being intercepted by malicious actors.
3How to Create MDM Policies?
Configuring MDM policies depends on a company’s requirements and compliance rules. To create mobile device management policies, you will need to:
- Step 1.Choose an MDM software
- Selecting the right MDM software for your business can be challenging due to the need to evaluate all available functionalities. AirDroid Business stands out as one of the most comprehensive MDM solutions, providing robust control and management features within a single dashboard. It provides you with complete policy settings.
- Step 2.Bind Your Mobile Devices into the MDM Dashboard
- Once you have signed up and logged into AirDroid Business, the next step is binding your mobile devices to the MDM Dashboard. Follow the enrollment guide to select the appropriate method for enrolling devices into the admin console for management.
- Step 3.Create Policy Config File
- After enrollment, click on Policy & Kiosk >> Policy & Kiosk Config Files >> Press +Create Config File button, this will allow you to view several options and start establishing policies for the managed devices.
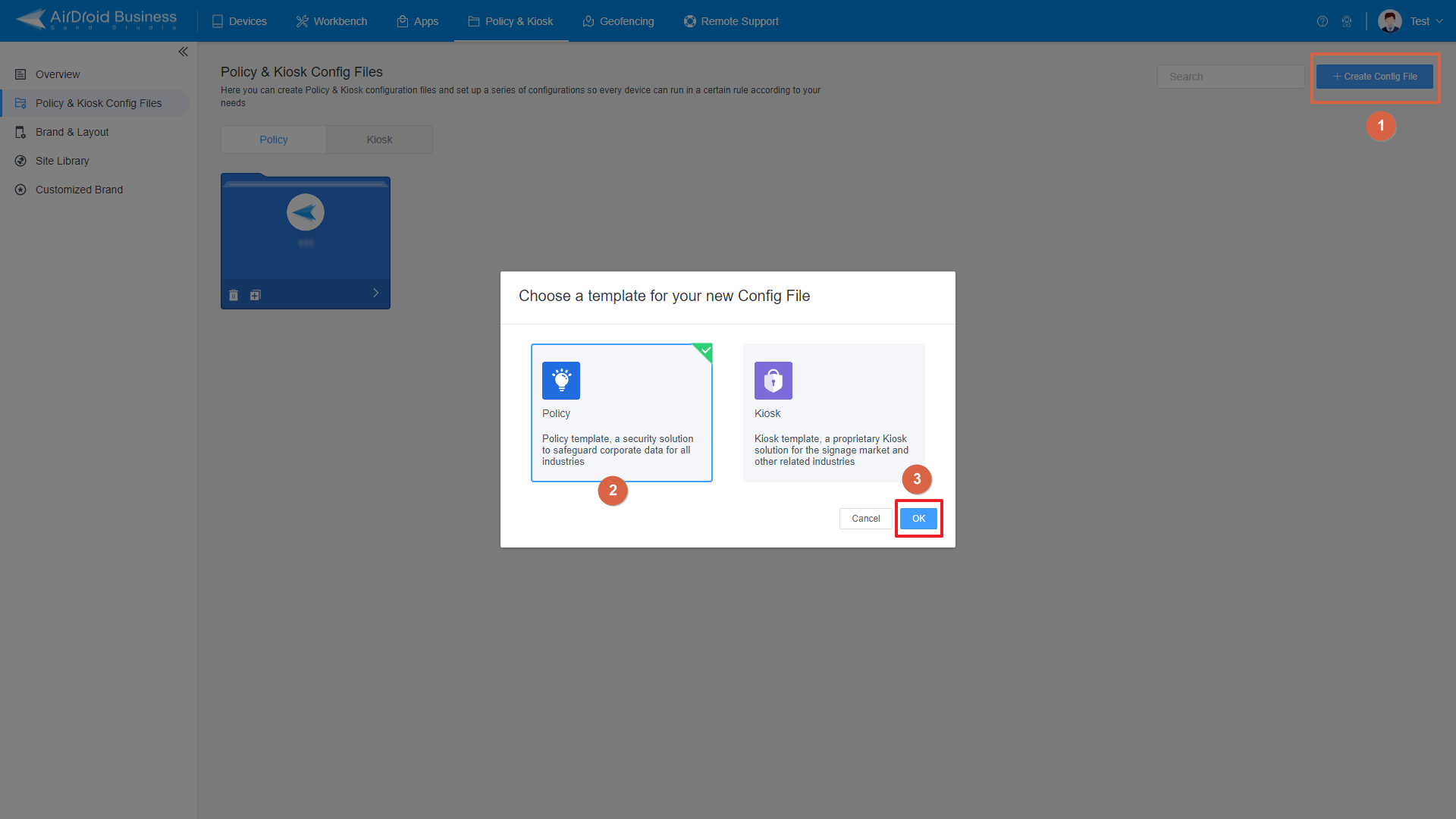
- Step 4.Apply Policy Profile to Corporate Devices
- Once you have determined what policy configurations the user needs to focus you can group the policy file and apply it to devices. These configurations can then be repeated on as many devices as you need.
4MDM Policy Checklist
| Risks | Description | Available Policies |
| Data loss | The result of devices falling into the hands of unauthorized third parties through theft or loss. It could also be the result of cyberattacks through the installation of malware that targets data access. | Remote Lock & Wipe Mandatory Storage Encryption Sync and Transfer App permission management |
| Unauthorized access | A third-party user without authorization has received access to sensitive company data. | Password Policy FRP protection Role-based access control |
| Malware | Threats include spyware, viruses, and malware applications that can be installed on mobile devices without the owner realizing it. | Application Allowlist/Blocklist Disable Allowing unknown sources |
| Security Vulnerability | Systems that are not up-to-date are missing the latest security patches to help mitigate the risks of cyber-attacks. | System Auto Update |
| Privacy leaks | Sensitive company data is either leaked by an unauthorized third party or an employee who has either accidentally or deliberately shared it with others. Data could have been stolen from a device if they had not been properly stored. | Disable device functions like camera, screenshot, microphone, etc. |
| Excess Data | Users are overusing the network for purposes unrelated to their work tasks, harming their productivity levels. | Network usage rules |
5Why Businesses Need An Mobile Device Policy
MDM policy for mobile devices can help with several security measures that a corporation will need to follow including:
Compliance & Standardize Device Configurations
A growing number of industries and countries have started implementing laws and string regulations regarding data protection. With MDM policies you can ensure adherence to these laws by restricting access to data, and keeping all apps on devices up to date to comply with regulations.
The central control of MDM policies allows organizations to group users based on their authorization access and standardize device configurations.
Cost Efficiency
Increased cost efficiency through monitoring and stopping the app and unneeded software usage, configuring bulk devices to use the office Wi-Fi, and creating unified device settings. This allows corporations to reduce IT burden and streamline the device configuration process.
Employee Productivity
MDM policies can heavily restrict what access employees have to apps that could function as distractions on their mobile devices. There is also the option of restricting the apps that employees have while monitoring how they spend their work hours. This sort of management can help limit the ability of users to procrastinate during work hours.
Security Enhancement
Configuring devices can block unauthorized third-party users from accessing corporate data and the company network. Users are restricted when transmitting data or installing different applications with application usage being monitored.






Leave a Reply.