How Remote Browser Isolation Secures Browsing Activity
Opening a browser is a day-to-day behavior. People gain a vision of a broader world through it to satisfy one's curiosity. And at work, people use a browser to enable communication and connection breaking away from distance restrictions.
But, the alertness towards security can be decreased due to the routine. People sometimes don't realize that the browser, as an application with Internet-access power for 3W (World Wide Web), is an open door to cybercriminals.
According to the website security report by DWG, there is a website being attacked every 39 seconds. And it's possible to lead to identity theft for both personal and enterprise.
Remote browser isolation, also known as RBI, is introduced to help web security. Let's discuss the technology in this article!
- Part 1 : Remote Browser Isolation (RBI) Explained
- Part 2 : Key Cyber Threats that RBI Can Effectively Mitigate
- Part 3 : How Does Remote Browser Isolation Work in Browsing Security?
- Part 4 : Remote Browser Isolation Types and Examples
- Part 5 : Pros and Cons of Browser Isolation
- Part 6 : Other Approaches for Browser Security
Part 1 : Remote Browser Isolation (RBI) Explained
What is Remote Browser Isolation (RBI)?
Remote browser isolation is a solution to isolate the web request–response cycle and to keep browsing sessions in a cloud environment technically.
With it, endpoint users can use the browser as normal but will stay in read-only mode for the webpage content. The content is hosted on a remote server, not on the using device, which is the biggest difference from traditional browsers.
Let's take it a step further.
Technologies involved in browser isolation:
- To achieve Remote: Cloud computing; virtualization; load balancing; data compression; caching and others.
- To achieve Browser: HTTP/HTTPS; Web API; WebRTC; programming languages like C++, C#, or Python; sandboxing and so on.
- To achieve Isolation: Containerization; streaming; zero trust architecture; threat Intelligence; etc.
Part 2 : Key Cyber Threats that RBI Can Effectively Mitigate
Web browser isolation is extremely helpful in protecting devices and enterprises from cyberattacks. Here are the major cyber threats RBI can handle.
XSS
XSS, also known as cross-site scripting, is a type of cyber threat that injects malware scripts into seemingly harmless websites to target unsuspecting browsers. The script then runs on the browser app and steals sensitive personal or corporate data. Moreover, attackers can use XSS to commit website defacement.
Cookie Theft
Cookie theft is also called session hijacking. It is a type of hacking in which an attacker will steal a user's browsing cookies to gain unauthorized account access. Cookie theft can bring serious losses of personal information, financial data (e.g. online banking), confidential business data, and more.
Malware & Ransomware
Remote browser isolation can effectively prevent certain types of malware and ransomware, for example, adware, spyware, and browser hijacking. These cyber threats harm operating systems badly and impact device usage.

Spam & Phishing
Spam and phishing are simple but dangerous cyber threats that target personal information and can result in shutdown devices. They are headaches of enterprises which lead to data and financial loss.
Drive-by Downloads
A drive-by download refers to the unintentional download of malicious software when accessing a website. It can significantly harm the browser and overall system of the device.
DNS Attacks
DNS attacks are a serious threat to browser security. Cybercriminals can alter the DNS records to redirect a domain name and IP address, or to bypass network firewalls. However, an RBI browser enables security-related configurations.
Part 3 : How Does Remote Browser Isolation Work in Browsing Security?
The RBI technology mainly leverages cloud technology. Its mechanism can be done through remote browser isolation software.
● The cloud server and the cloud browser will run together in a dedicated networking environment.
● In the network, the RBI software processes the redirected user's URL request including - filtering web content, cookies, web storage data, and files; webpage rendering; and user interaction actions.
● Next, the safe and well-handled webpage will be delivered to the user's device.
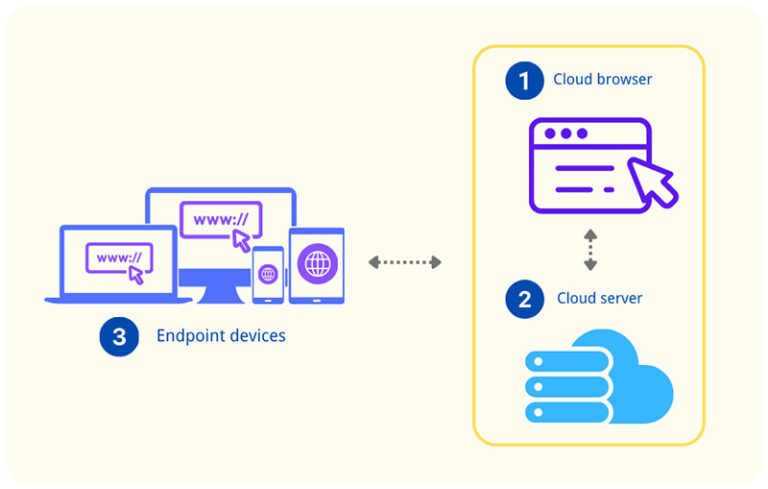
When coming to the detailed web browsing process, it is more intuitive to see web browser isolation's ability to improve browser security.
The working process of (RBI) remote browser isolation involves the following aspects.
1) DNS Lookup
When a user inputs a website, the browser starts with a DNS lookup to translate the domain name into an IP address. In remote browser isolation, this lookup process is intercepted, redirected, and held within an isolated environment, not in the local device.
2) TCP and TLS
In the context of web browsing, TCP (transmission control protocol) takes on the role of establishing the communication between cloud browser and server while TLS (transport layer security) is a cryptographic protocol to secure the connection.
Once the TCP connection starts, a TLS handshake is initiated over the established TCP connection, and all data will encrypted and exchanged between the browser and the server.
Remote browser isolation doesn't directly be in the connection, but it does add an additional security layer to the whole process.
3) Rending
Rendering is the process of converting webpage codes into a visual display so that the user can read and interact with it. It contains parsing code files, creating DOM and CSSOM, and compositing elements.
RBI provides a shielded area for the rending process.
4) HTML Sanitization
HTML sanitization or HTML cleaning is used to filter out unsafe elements in an HTML document. It checks the user's input, HTML tags, embedded scripts, and special characters.
RBI solutions can help remove malicious factors instead of sending the actual web to the user.

Part 4 : Remote Browser Isolation Types and Examples
Cloud-Based RBI
Cloud-based remote browser isolation is when the device does not perform the browsing online, but rather the web traffic goes through a cloud-hosted sandbox which fully protects the device and servers to which the device is connected to.
Menlo Security is an example of a cloud-based RBI technology to secure device browsing.
On-Premises RBI
On-Premises RBI is another way to protect your device while browsing. This method is adjacent to traditional RBI and involves a separate hosted service which is hosted on-premises in the company’s internal IT environment.
An example of a service provider that can help you set up on-premises RBI is Ericom Shield.
Pixel Streaming
Pixel streaming is by far the most labor-intensive type of RBI, but it is also one of the safest. By only allowing the device to receive the images of a website and not the code, you fully protect the device from malware and malicious content.
Symantec is an example of a security product that can help enable enterprises to set up pixel streaming as an RBI solution.
Browser Plugin-Based RBI
The last type of RBI we will cover is the browser plugin-based RBI, which helps to protect companies and their devices by using a browser plugin. The browser plugin is able to restrict websites from having an impact on the device.
AirDroid Business Kiosk Browser is a great example of a browser plug-in-based RBI, which can be installed on all company devices through its Kiosk Browser mode. Kiosk Browser locks devices specifically to prevent malware and malicious scripts from running.
Part 5 : Pros and Cons of Browser Isolation
Pros
- Safety
Increased safety of devices is the most obvious pro of using RBI while browsing. It is a clear need for companies that are at risk of malicious attacks due to the need to browse online for company operations. As we stated, the potential for online threats is almost higher than it has ever been. Online safety is paramount in enterprise environments. - Mental Wellness
Having improved security has other benefits as well, such as employee peace of mind, employer peace of mind, and security of personal information. In environments where a company is hosting the personal data of its clients, it is especially important to keep this data safe and secure. Clients, employees, and management can rest assured that website browsing will not pose a threat to the safety and security of the company. - Great for Public Image
RBI is great for public image in the sense that not having protection against malware and ransomware is negative for public image. Data leaks are a company’s worst nightmare in today’s world. Companies must protect client and user data for their image and reputation.
Cons
- Cost
The cost of setting up remote browser isolation can be great, especially in enterprise environments. For methods that involve pixel streaming, enabling RBI can be very laborious on a system and may cost an extreme amount due to the resources required to handle the workload. The costs associated with more intensive RBI methods might be mitigated by choosing a different method.
For example, the browser plug-in method for remote browser isolation is a more affordable method than using pixel streaming as a solution. - Degraded Browser Performance
Slower performance is a possibility from some methods of RBI, namely pixel streaming and cloud-hosted browser isolation. This is because there is an extra step being completed in the process. Rather than your device communicating directly with the network and website, there is another process that must occur before an image is displayed on your screen.
Methods like browser plug-ins do not have this delay, however.
Part 6 : Other Approaches for Browser Security
There are other approaches for browser security that you can also take. In this section, we’ll explore some of the other options which may work for you.
Secure Web Gateway (SWG)
A Secure Web Gateway, also known as a SWG, is an option that helps to filter internet traffic to prevent cyber threats.
Cloud Access Security Brokers (CASBs)
A Cloud Access Security Broker or CASB is a type of software that monitors the online activity of users in order to prevent the possibility of cyber attacks. This methodology involves the use of security policies to determine what is and is not allowed.
Built-in Pop-up Blockers
Built-in Pop-up Blockers help to remove the possibility of pop-ups appearing on the screen, which can be accidentally clicked on and start malicious downloads or executions of code. Pop-up blockers are generally a good idea to have involved in one’s security plan.
Same-Origin Policy (SOP)
Same-Origin Policy is a method that prevents websites from running scripts unless the script is associated with the same website. This helps prevent cyber attacks, which may come in the form of running malicious scripts in the background.






Leave a Reply.