Role-based Access Control: Definition and Examples
RBCA (Role-based access control) is integral to enterprise security and management. It helps to manage access for multiple users based on their concerns and designation so that the enterprise can keep the confidential files secure and limited to concerned authorities only.
1Definition of Role-based Access Control
1.1What is Role Based Access Control (RBAC)?
Role-based access control is an advanced security mechanism that restricts system/network access for users based on their role in an enterprise environment.
Using RBAC, administrators can analyze employees' responsibilities and group them to distribute roles and access for optimized management and security systems.
Some crucial factors in managing access can be based on authority, designation, responsibility, and job competency. RBAC is commonly utilized in healthcare, finance, telecommunication, manufacturing, retail, education, and IT.
It is a primary security factor adopted worldwide in organizations to manage permissions and access to sensitive data based on the roles and responsibilities assigned by designated authorities. Providing employees with the necessary data or information ensures they remain productive and focused on their responsibilities.
1.2Key concepts related to RBAC
- Different Roles
In RBAC, role refers to the permissions granted to the users based on their job description and the responsibilities they need to fulfill in a business network.
Roles define the duties of users and access to the organization network or database required to perform their duties.
Some significant roles include admins, managers, employees, developers, and auditors. Each role has a pre-defined set of permissions to access official data efficiently and manage it through RBAC.
- Users
Users are individuals who are assigned different roles based on their qualifications and experience.
They interact with the system, each with different access levels and business requirements to perform their duties.
Users might include employees, customers, contractors, and other entities. Each user is answerable to the assigned duties.
- Define Permissions
Permissions are the actions management approves for users to perform within the system.
- Components
Permissions consist of two main factors: actions and scope. Actions are specific operations allowed to users, while scope tells where the action can be performed.
- Actions:
Actions are the specific operations that define what users can perform. The most common actions in RBAC are read, write, execute, and delete.
1.3Advantages: Why Companies Apply this Rule?
- Improved Security
RBAC helps grant permissions by role because it limits access to only the resources necessary for a specific job. - Regulatory Compliance
RBAC makes it easier to implement, track, and audit access rights, ideal for organizations subject to industry compliance standards such as HL7, HIPAA, and GDPR. - Enhanced Collaboration
RBAC supports improved functionality and clarity of roles and responsibilities in a company while providing employees with suitable access to resources. - Operational Efficiency
RBAC enables administrators to change the roles of all users in one session without changing individual permission, making it efficient. - Reduced Administrative Overhead
RBAC manages user access rights from a centralized platform, thus decreasing the number of issues related to the increased number of users and functions. It also allows easy modifications for access controls, which helps in crisis management.
2Role Based Access Control Example
Example 1- RBAC in Company-device Management
Mobile Device Management Solutions are widely used to integrated into organizations to manage and secure devices from a centralized position, also add limitations for device, app, and internet usage.
Some MDM solutions have built-in support for RBAC. They are comprehensive options to manage access controls. One of them is the AirDroid Business MDM.
Setting up RBAC with AirDroid Business MDM allows organization owners to limit access of the employees. Organizations can assign permissions based on employee positions. They are not allow to access options that without granting permissions. Then they are not allowed to access options that without granting permissions.
Implement RBAC Strategy to Manage Devices Safely
AirDroid Business allows staff to be classified into various roles for easy content and access management. These roles include super admin, admin, team members, and viewers by default, while custom roles can also be added.
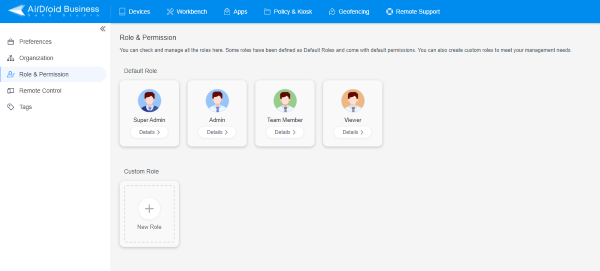
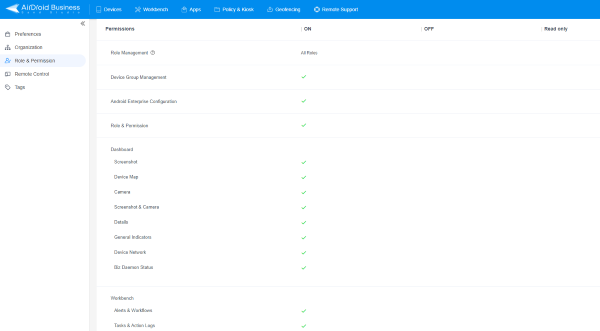
In the role and Permissions tab, admins can define different permissions for different roles as required for business demands. These permissions include options like read-only, workbench, App management, device settings, and more.
Example 2-RBAC in Finance
In a financial institute or organization providing financial services, RBAC plays a significant role in safeguarding sensitive records of various entities. Financial institutes contain an extensive database of people with their sensitive financial information.
Usually, a financial institute has financial analysts, accountants, finance managers, operational managers, auditors, and many other positions. There is a big difference between the designation of a cashier and the branch manager, and the level of access for both positions varies greatly. Similarly, every position needs to have a different level of access to the database based on the necessary information required for each role.
Based on their roles, they are granted permissions. For example, an accountant gets permission to manage transactions, edit account information, and prepare records. An auditor only gets read-only permission to access all financial records and the database to generate reports. Similarly, the financial analyst can only access financial tools and cannot make any changes.
Example 3-RBAC in Cloud Services
RBAC helps manage access to the cloud data, keeping it confidential from malicious entities. Various entities work to manage cloud services, including cloud administrators, developers, DevOps engineers, and other related persons.
The first step is to define the roles of each entity involved and then grant permissions for access based on the roles.
Some examples of roles and permissions are:
The cloud administrator has complete control over all resources, including storage, data, network configurations, and virtual machine management.
End-users are provided limited access to the applications and storage space they purchase.
3How to Plan Your Access Control Strategy?
Implementing role-based access control requires strategically planned implementation, as it directly impacts organizations' security. This complex task requires a series of steps to ensure effectiveness, security, and productivity.
- Understanding the Business Needs
The first and foremost step is to analyze your business requirements. Without analyzing the requirements, directly moving to RBAC can result in a downfall and a lack of security.
You need to carefully analyze the technologies, job descriptions, supporting processes, and other important factors to plan the access control strategy. - Plan the Scope of Implementation
After carefully analyzing your business needs, move to planning the scope of implementing RBAC to identify how RBAC can align with the organization’s needs.
You will be able to analyze and narrow the scope, which will help you define access controls for different users. - Define Roles
This step becomes straightforward once you have analyzed business needs and what individuals can perform. Based on this analysis, you can easily assign roles and permissions.
Admins can manage to grant permissions to access data by individuals and groups using RBAC. - Implementation
Finally, roll out the RBAC in slots to avoid disruptions and make things easier. It is highly recommended that you regularly check performance and take feedback from users to improve it over time.
4Compare Different Access Control Methods
RBAC vs. ABAC vs. ACL vs. PBAC
| RBAC | ABAC | ACL | PBAC | |
|---|---|---|---|---|
| Abbreviation | Role-based Access Control | Attribute-based Access Control | Access Control List | Policy-based Access Control |
| Basis of control | RBAC grants access rights depending on the roles of users | ABAC controls access | It lists the specific permissions attached to computing resources. | It set policies to define conditions for access. |
| Dynamic adaptation | Limited as it contains static roles. | High because of dynamic attribute evaluation. | Limited as it contains static lists. | High due to dynamic policies. |
| Restrictiveness | Restrictive because access is granted based on user role. | Highly restrictive as it specifies granular access controls. | Depends on the permissions defined. | Less restrictive than other methods. |
| Security | High as users are provided access to necessary data. | High because of evaluation of multiple dynamic attributes. | Depends on how maintained, but normally secure. | Less secure if policies are not clearly defined. |
| Example | Corporate IT systems | Cloud services with dynamic attributes | File system permissions | Regulatory compliance environments |
5You May Want to Know
Are there any limitations of role-based access control?
Yes, there are some limitations in RBAC. It can be a complex and challenging task to manage for large organizations, especially when roles overlap.
RBAC is static in nature, so it cannot adapt to changes in job functions. Managing roles can be challenging as role and user growth is very common in business environments.
Moreover, there are access control techniques you should know with deep business knowledge to incorporate them efficiently.
How does RBAC work?
RBAC works on the basis of roles defined and the permissions granted by administrators based on each role’s job description and needs. This includes assigning roles for each employee and defining access and limitations for them to keep data confidential and accessible to the designated authorities only.
It is an efficient way to manage data access for different levels of employees.
For example, access to confidential data for staff, admins, managers, directors, and CEO remains different as authorized. RBAC also helps create groups to easily manage permissions when the number of employees is hundreds or thousands.
What are the three primary rules for RBAC?
Role assignment, role authorization, and permission authorization are the three primary rules of RBAC.
- Role assignment means the user must be assigned some role to access the data; otherwise, access to data is not granted.
- Role authorization means users can only activate roles for which they are authorized by the administration, preventing unauthorized role activation.
- Permission authorization means users can access resources if their active role requires permission.
6Conclusive Note
As a security measure, RBAC plays an integral role in ensuring data confidentiality and automation in business activities. It is based on three basic rules that clearly define what it contains and how it works.
These three rules are role assignment, role authorization, and permission authorization. RBAC helps enterprises set permissions based on responsibilities so everyone can effectively perform their jobs without wasting time.
Hence, it also optimizes costs and efforts to perform routine operations. Although it can be a complex process and needs high business knowledge to incorporate effectively, once done, it can save costs and labor and result in enhanced productivity and compliance with industry regulations.






Leave a Reply.