Device-Centric Security: RBAC Meets Mobile Device Management
According to AAG, there were 236.1 million ransomware attacks worldwide in the first half of 2022. Such figures highlight the need for solid access management systems in industries like healthcare, aerospace, and even in Government.
As one of the mobile security solutions, Roles Based Access Control (RBAC) restricts system access solely based on the roles of individual users within an organization. Imagine making sure your employees can only access the precise information they need on company devices, nothing more, nothing less.
This article will explore RBAC, exploring how it effectively manages access, its practical applications, and why businesses should opt for this approach.
- 1 :What is Roles Based Access Control (RBAC)?
- 2 : How Does RBAC Manage Access?

- 3 :Examples of Common RBAC Permissions
- 4 :Why is RBAC Beneficial for Organizations?
- 5 :Comparing RBAC and ABAC: What Sets Them Apart
- 6 :Applying RBAC: Real-life Scenarios
- 7 :Common Pitfalls in RBAC Implementation
- 8 :Strengthen Your Mobile Security with AirDroid Business MDM
- 9 :Final Thoughts
1What is Roles Based Access Control (RBAC)?
RBAC, or Role-Based Access Control, operates like a digital security guard. It grants varying access levels based on job roles, much like VIP and standard passes at a club. (Managers get VIP passes, while regular employees have standard ones.)

This approach guarantees people can only handle information and perform tasks essential to their roles. When organizations put RBAC in place, they not only decrease the chances of cyber threats but also shield sensitive data, adding an extra level of safety.
RBAC revolves around three core principles which are:
- Role Assignment: In a system, users are given specific roles that define their permissions. This means access is granted based on predefined roles rather than individual or arbitrary permissions.
- Role Authorization: Once roles are defined, they carry certain permissions. Simply possessing a role does not guarantee automatic access; the key is confirming the role has the correct authorizations. This highlights the need to validate and approve roles themselves rather than focusing on individual users.
- Permission Authorization: In this setup, users don’t directly receive permissions. Instead, they acquire them through their assigned roles. By having a role, users can perform the necessary functions associated with their roles. This approach reinforces the connection between permissions and roles, preventing unauthorized access.
2How Does RBAC Manage Access?
Kicking things off, role assignment is the primary step. It's the starting point for determining who can access specific resources. Roles and permissions collaborate, carefully reviewing each access request against a list of allowed actions. The system then definitively allows or denies entry, adhering closely to established rules.
These designated roles make up the backbone of the access control system. Each role carries a specific set of permissions that clearly define the level and method of access to resources, so users can only possess access pertinent to their specific job roles.
Roles and permissions work together seamlessly, thoroughly examining every access request against predefined criteria. The system promptly responds, either granting or denying entry based on well-understood protocols.
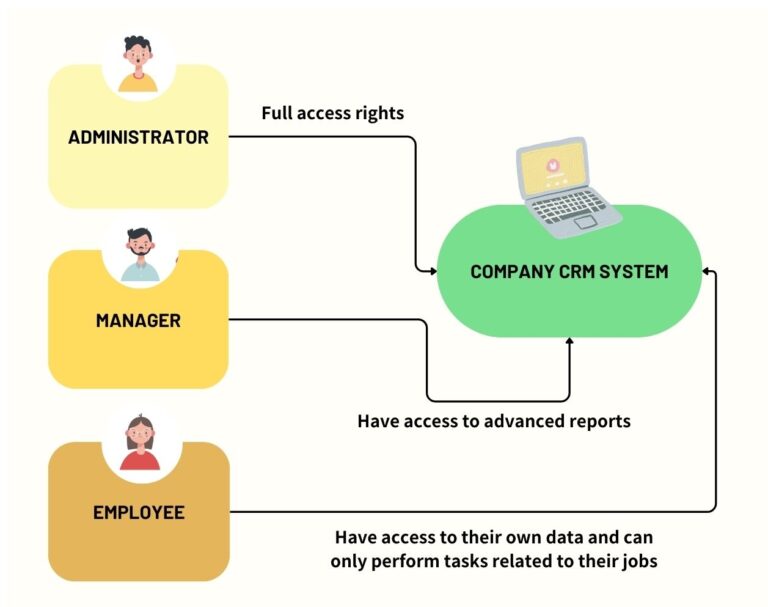
3Examples of Common RBAC Permissions
Common RBAC permissions vary depending on the industry and organization, but here are some general examples:
Adjust screen timeout on Android at scale with AirDroid Business:
- Create
- Read
- Edit
- Delete
- Approve
- Manage
- Upload
- Download
- Access Control
- Report Generation
- Configure settings
Remember, these permissions are just examples, and specific permissions will vary based on the organization's needs and the systems in use. It's important to carefully define and assign permissions for users.
4Why is RBAC Beneficial for Organizations?
RBAC implementation provides a range of advantages for organizations across sectors, significantly enhancing their overall security posture. Here are several key benefits:
Efficient Access Management
RBAC streamlines access by assigning specific roles to individuals. Users are only granted access to the information and resources necessary for their job functions.
Simplified Administration
It simplifies the process of granting and revoking access rights. This makes it easier for administrators to manage permissions, especially in large organizations with numerous users.
Enhanced Security
RBAC reduces the risk of unauthorized access and data breaches. By limiting access based on roles, it minimizes the potential for human error or intentional misuse.
Compliance and Auditing
RBAC helps organizations comply with industry regulations and standards. It also facilitates auditing processes by providing clear records of who accessed what information.
Adaptability to Organizational Changes
RBAC allows for easy role adjustments as employees change positions or take on new responsibilities.
Reduction in Administrative Costs
With clear role definitions and automated access management, RBAC can reduce the time and effort spent on manual access control processes.
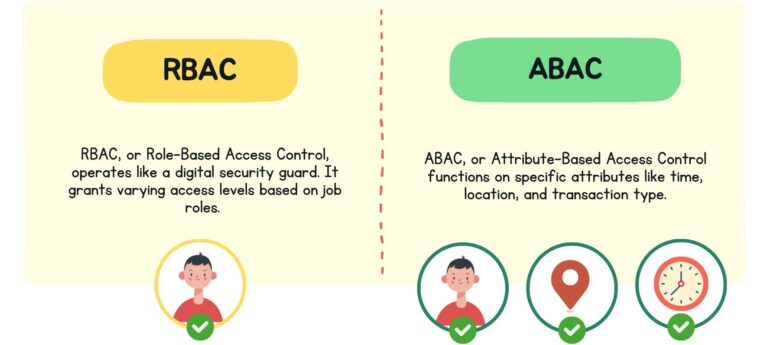
5Comparing RBAC and ABAC: What Sets Them Apart
Both RBAC and ABAC (Attribute-Based Access Control) are popular approaches which aim to secure organizational data. However, they use different methods to achieve this goal.
● RBAC (Roles-Based Access Control)
RBAC functions by assigning specific roles.
For instance, a regular employee can access the CRM system, but the capability to extract advanced CRM reports is reserved for managers. This establishes a structured access framework aligned with distinct job functions.
● ABAC (Attribute-Based Access Control)
On the other hand, ABAC functions on specific attributes like time, location, and transaction type.
For example, access to company networks or software might be restricted to regular business hours and familiar locations to prevent hacking attempts.
In essence, RBAC provides a foundation of access controls based on specific roles, while ABAC offers a more flexible approach based on various attributes and environmental factors.
6Applying RBAC: Real-life Scenarios
RBAC’s ability to tailor access is vividly illustrated through diverse permissions across varying sectors.
Healthcare Industry (Using Hospital Workstations and Tablets)
- Doctors, using hospital workstations and tablets, have access to comprehensive patient records, allowing them to view medical history, diagnosis, treatment plans, and lab results.
- Nurses, equipped with hospital tablets, can access vital signs, medication schedules, and care plans for assigned patients.

Manufacturing and Production (Using Industrial Terminals and Handheld Devices):
- Engineers, equipped with laptops and handheld devices, have access to design and modify production processes, manage automation systems, and conduct quality control.
- Maintenance staff, utilizing ruggedized handheld devices, have access to troubleshoot and repair machinery, view equipment diagnostics, and order replacement parts.

Logistics and Transportation (Using Fleet Management Systems and Mobile Devices):
- Drivers, equipped with company-provided mobile devices or tablets, have access to their assigned routes, delivery schedules, and shipment details. They can also update shipment statuses and report any issues in real-time through the fleet management system.
- Fleet Managers, equipped with desktop computers and specialized fleet management software, have elevated access to oversee the entire fleet's performance. They can analyze data on fuel efficiency, maintenance schedules, and driver performance to optimize operations.

These examples underline RBAC’s adaptability, demonstrating how it deftly manages permissions, addresses sector-specific challenges, and balances accessibility and security.
7Common Pitfalls in RBAC Implementation
While implementing RBAC can yield significant benefits, it comes with its share of challenges often arising from oversights and misconceptions.
📌 Overly Broad Role Definitions
● Challenge: Giving extensive permissions to a role can expose sensitive data unnecessarily.
● Example: Allowing all hospital staff access to patient records, risking security.
📌 Role Engineering Oversight
● Challenge: Failing to accurately define and assign roles can lead to unauthorized access to critical system settings.
● Example: In a hospital, non-medical staff gaining access to sensitive patient records due to role mismanagement.
📌 Lack of Regular Audits and Updates
● Challenge: Neglecting to update and audit access controls can result in security vulnerabilities and non-compliance.
● Example: Failing to update access permissions in a government agency after personnel changes, leading to former employees retaining access.
📌 Failure to Revoke Access Timely
● Challenge: Not promptly revoking access for departing employees or role-changers can expose vulnerabilities.
● Example: Failing to promptly revoke building access for a departing employee, potentially allowing unauthorized entry.
📌 Insufficient Training and Awareness
● Challenge: Lack of understanding about RBAC's significance and proper usage can undermine effectiveness.
● Example: Employees in a financial institution not comprehending the importance of RBAC, resulting in inadvertent sharing of sensitive financial information.
Acknowledging and addressing these common pitfalls is crucial for successful RBAC implementation, securing organizational assets, and promoting operational efficiency across industries.
8Strengthen Your Mobile Security with AirDroid Business MDM
In situations where you need to handle a large number of mobile devices, relying solely on RBAC might fall short.
AirDroid Business MDM steps in as a tailored solution for businesses looking to efficiently manage, monitor, and secure their employees' mobile devices.
Through MDM implementation, you can enforce policies, deploy applications, and safeguard sensitive data across various devices, resulting in a considerable boost to mobile security.
9Final Thoughts
In the face of mounting cyber threats and the evolving landscape of remote work, Role-Based Access Control (RBAC) has assumed unprecedented importance.
By accurately assigning access privileges based on an individual's role within an organization, RBAC stands as a robust defense against data leakage, making it more crucial than ever in today's digital environment.






Leave a Reply.