How to Manage Root Permission on Android Devices?
Rooting an Android device, which unlocks the full potential of the device is a double-edged sword. On one side, it opens doors to customization and advanced controls, while on the other, it exposes devices to potential risks.
The decision to root largely depends on the usage and context. Together, we'll explore the Magisk Root Permission Manager, detailing the process of rooting with Magisk and then delving into the intricacies of managing root permissions effectively.
1 What is Rooting?
Rooting means gaining elevated privileges on an Android device. This elevated access, often referred to as "root access" or "superuser" permissions, allows users to delve into the device's operating system. It gives access to customization and modifications beyond what's typically allowed.
When you root an Android device, you gain the ability to remove pre-installed apps, optimize performance, and even install custom ROMs. Rooting gives users a level of control and personalization that goes beyond the manufacturer's default settings.
2 What is a Root Permission Manager?
For a layman, an app permission manager is a tool/app that allows you to view, alter, grant, or restrict permissions to the apps. In the rooted devices, individual apps can be granted permission to get elevated access. The permission manager can allow or restrict such access. For example, you can use a root permission manager to allow or disallow an app to make changes to system files. This cannot be done in unrooted devices.
3 How to Manage Root Permission on Android Devices?
Now, let's venture into a tool that adds finesse to this power play – the Magisk Permission Manager. We'll explore how to root your device with Magisk and then fine-tune those permissions with a touch of expertise.
Magisk Permission Manager
Magisk Permission Manager is a sophisticated tool that helps in managing root permissions on Android devices. It serves as a gateway to unlocking advanced customization while maintaining a vigilant eye on security.
This manager not only roots your device efficiently but also provides a nuanced approach to controlling and customizing root permissions.

Root Android Devices with Magisk
- Begin the Magisk installation process by downloading the latest stable release.
- Ensure you don't unpack the ZIP file, as TWRP flashes complete ZIP files.
- Connect your device to your computer via USB, select "Transfer files" on your phone, and copy the Magisk ZIP file into the Download folder.
- Safely disconnect your phone, reboot it into recovery (usually by pressing Volume Down and Power keys simultaneously), and select Recovery mode from the menu.
- Once in TWRP, tap Install, navigate to the Download folder, and choose the Magisk ZIP file.
- Confirm the installation by swiping the blue slider. TWRP will handle the installation process, displaying a success message.
- Reboot your device, and voila, it's rooted with Magisk.
- Check the Magisk Manager app for installation status and enjoy the enhanced capabilities on your rooted device.
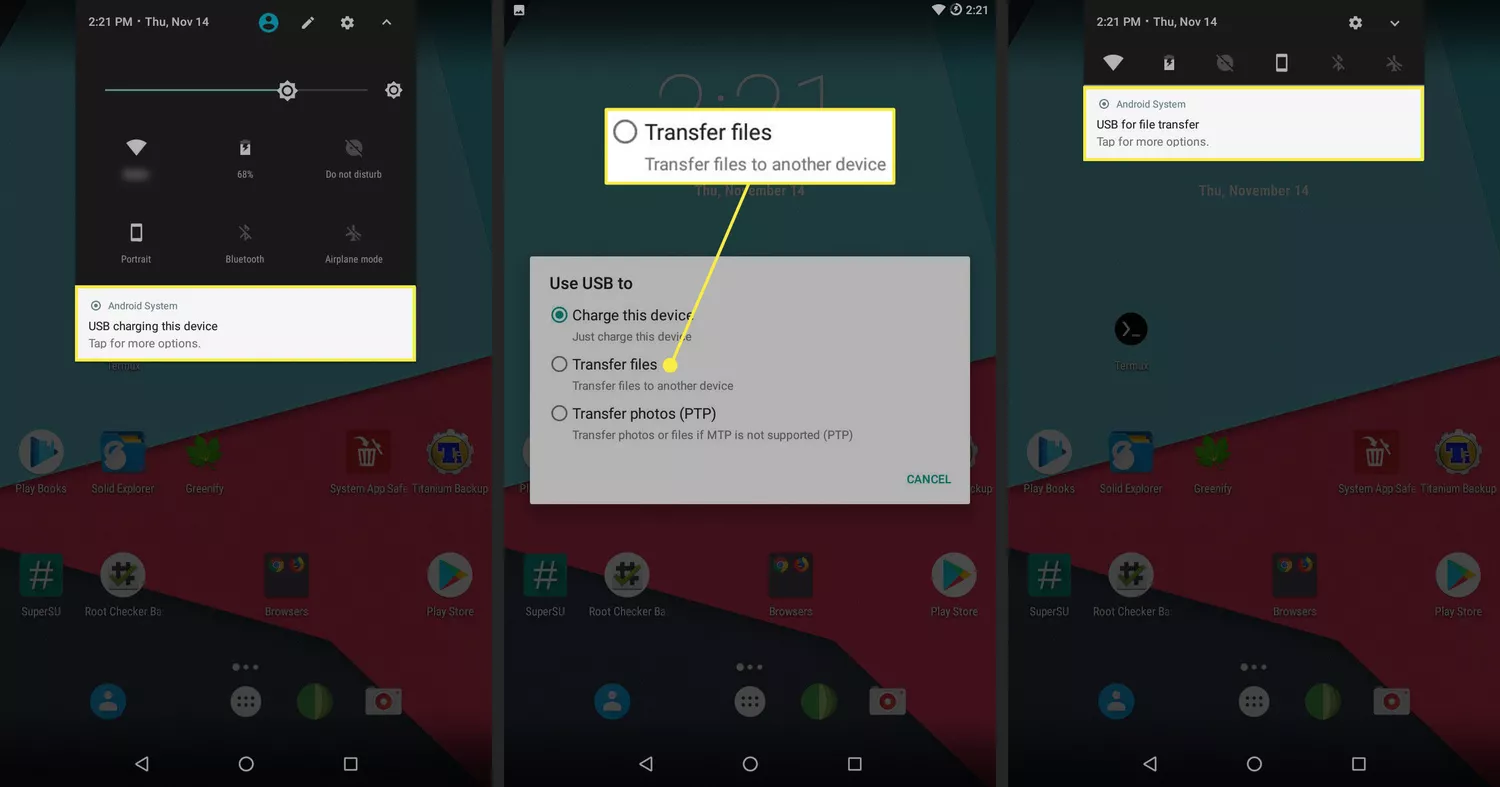
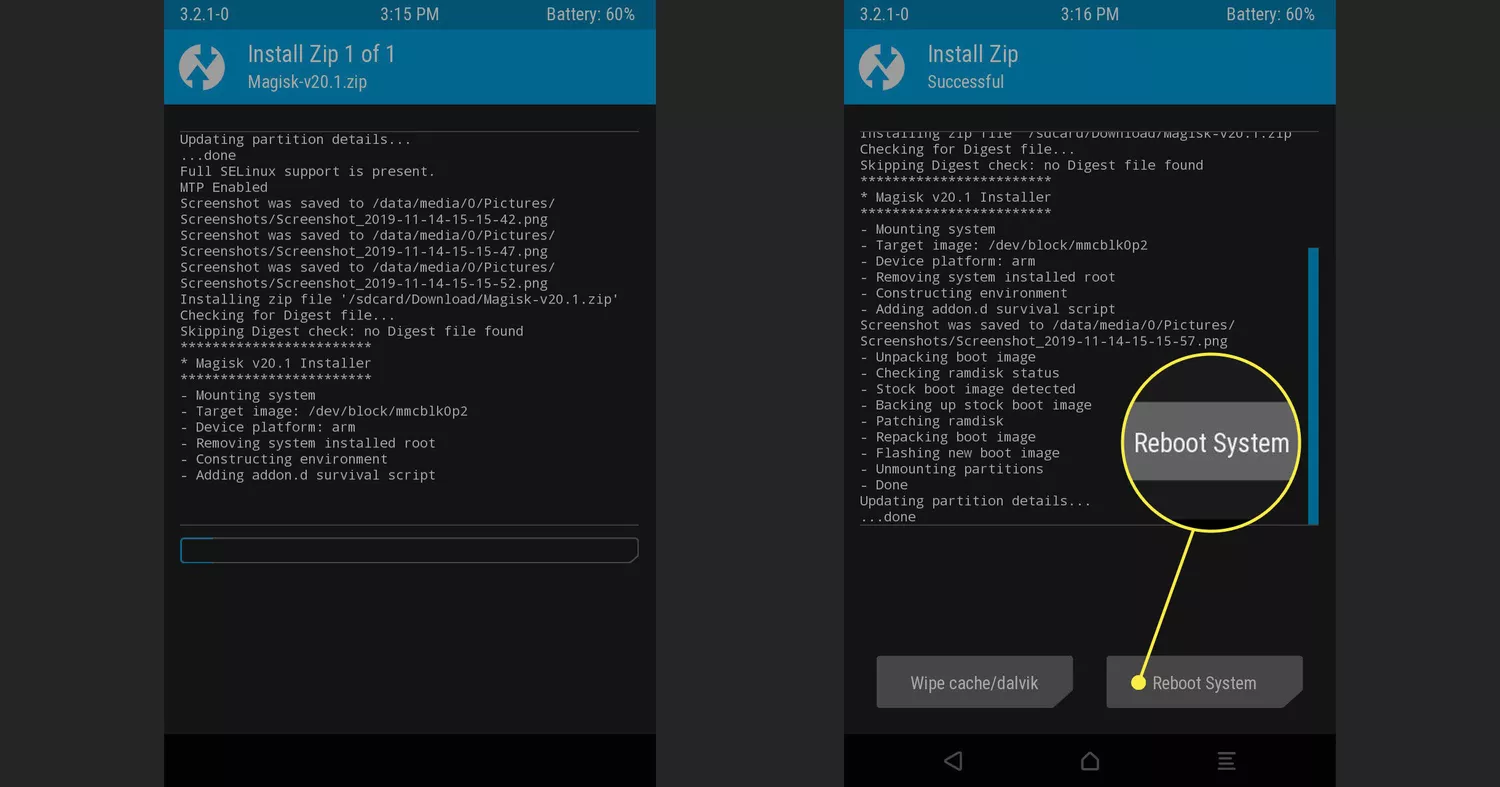
Manage Root Permissions with Magisk
- After successfully rooting with Magisk, the next phase involves managing root permissions with finesse.
- Launch the Magisk Manager app on your device.
- Within the app, access the 'Settings' menu and enable the 'MagiskHide' option to keep your root status discreet from certain apps.
- Open the Magisk Manager app and go to the "Superuser" section. Here, you will find a list of apps installed on your device. Toggle the switch next to each app to grant or deny root access to that particular app.
- To further manage app permissions, you can use modules specifically designed for that purpose. Magisk offers various modules that allow you to control the root access of individual apps. You can find these modules in the Magisk Manager app or on community forums.
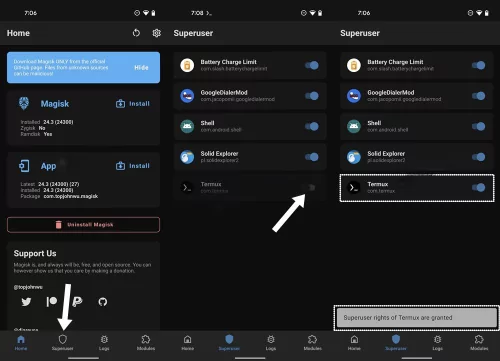
4Benefits and Risks of Rooting Your Business Android Device
According to the data collected by Verimatrix 36 Android devices out of every 1000 worldwide are rooted in the year 2024.
However, where users love rooting their devices for enhanced control over their Android devices, rooting has its downsides as well. Let’s explore both sides of the coin.
Benefits of Rooting Android Devices
- Install Custom ROMs:
You get the liberty to install a new ROM on your Android device. In short, you can renew your phone’s software. It helps solve performance glitches, customize the UI, and make your smartphone even smarter as updated ROMs typically undergo more frequent updates and use fewer resources.
- Remove Bloatware:
By rooting your device, you get the power to get rid of pre-installed stuff which isn’t of much use to you but you cannot remove it from your device. Isn’t it annoying to have your device littered with apps you would never use? Rooting allows you to ‘root it out’ altogether. For example, according to Statista, on average, every smartphone has 80 to 100 apps. Around 20% to 30% of apps are unused and are merely occupying space.
- Block Ads:
Imagine using all apps and games without those annoying pop-up ads. It becomes way more fun. Rooting allows you to block them permanently. For example, rooted devices with AdAway and other similar tools can block ads for each and every app.
- Expand Storage:
Gaining some extra space is another huge benefit of rooting as it allows you to move some apps to an SD card while keeping a few in your device’s memory.
- Optimize Battery Life:
With rooting, you can allow and disallow apps to use battery. By automatically closing the apps you are not using, you can significantly enhance battery life. For instance, Greenify is an app used by rooted devices to hibernate apps in the background and optimize battery life.
Risks of Rooting Android Devices
- Bricking Risk:
One of the most dreadful risks associated with rooting is bricking. In case you missed a step during the process, or accidentally flashed a corrupt zip file, it can render your device completely useless. Although bricking is quite rare and there is just 1% chance, to avoid bricking your device, always rely on trusted platforms for downloading apps and do thorough research on the steps for rooting before you start.
- Warranty Void:
Once your device has been rooted, and a problem arises in it, you can no longer claim its warranty.
- Security Vulnerabilities:
Rooting can lead to security breaches as is made evident by verimatrix that its is easier for hackers to get access to rooted devices as some built-in security features have been disabled due to rooting.
- Update Issues:
Another problem with rooted devices is that in some cases, the changes made during rooting will result in blocking the latest updates. The system updates might not get installed due to these changes.
5How to Check Device Status to Ensure Safety
Now, let's explore how businesses can effectively navigate this crucial aspect of device management and maintain a secure digital environment.
Root status of managed Android devices
In the realm of mobile device management, checking the root status of managed Android devices is a critical security measure.
With the AirDroid Business admin console, IT teams and administrators gain insight into whether a device is rooted or unrooted.
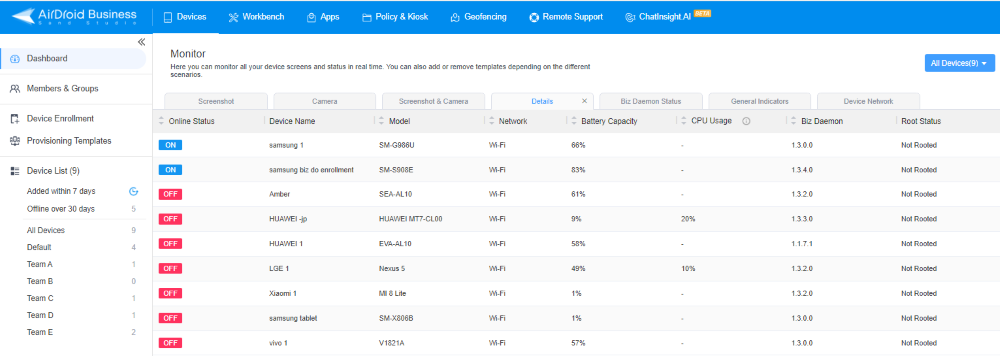
This feature serves as a proactive defense against potential security threats. It also acts as a security checkpoint, allowing organizations to enforce policies that prevent rooted devices from connecting to the secure network.
Hence, businesses can fortify their mobile security strategy and uphold data protection standards by staying informed about the root status of their devices.
6How to Get Rid of Your Android's Root?
Should users decide to unroll their devices, Magisk Manager provides a straightforward solution. Here's a concise guide:
- Open the Magisk Manager app on your device.
- Navigate to the bottom of the screen and tap "Uninstall."
- A confirmation message will appear. Confirm your decision by tapping "Complete Uninstall."
- Magisk Manager will initiate the uninstallation process. Once completed, a message prompts you to reboot your device.
- After the reboot, Magisk will be entirely removed, and your device will return to its unrooted state.
7Tips to Protect Your Rooted Devices
In the world of rooting, great privileges come with great risks. To enjoy the perks of rooting, you need to be extra vigilant about protecting your devices and data against unauthorized access and issues like bricking and maloperation. Here is how you can ensure safer operation while enjoying the status of a superuser:
Ensuring Device Security
As you know now rooting can render your device vulnerable to serious security risks putting at stake not just the device’s health but also your data and privacy, you need to be extra cautious. Here are a few steps to safeguard your device and data;
- For your financial apps, consider using biometric verification or 2 factor verification to restrict access.
- Make sure you have an authentic root permissions manager like Magisk installed to grant permission only to the trusted apps and manage all permissions vigilantly.
- Install apps from trusted sources only e.g. Google Play Store.
Practical Tip: Never forget to read user reviews before installing any app even when it is from a renowned platform. Moreover, take some time to thoroughly learn about the developer’s reputation.
Backup and Recovery Solutions
Timely backups done through trusted apps like Titanium help ensure that you have a full-fledged resource containing all your data and system files in case of a malware attack or a lost device.
Practical Tip: Keep your backup secure in a cloud or on another device.
Data Encryption
When encryption is enabled on an Android device, the data cannot be accessed by an unauthorized entity even if the device is lost or stolen.
Practical Tip: Consider using a strong decryption key to avoid data breaches and keep your important information unreadable.
7Conclusion
In navigating the complexities of rooting and managing Android devices, businesses must strike a delicate balance between customization and security.
Rooted devices, while offering advanced capabilities, present inherent risks. Proactive measures, such as routine root status checks strategic app management, and the root permission manager are paramount.
Notably, tools like AirDroid Business elevate this balancing act. With features like root status monitoring, AirDroid Business provides a vigilant eye on device integrity. This, coupled with its intuitive admin console, ensures businesses can seamlessly manage and secure their Android devices.
Understanding the delicate interplay between control and protection ensures businesses harness the benefits of rooted devices. It also helps in safeguarding against potential threats.







Leave a Reply.