Award-winning Security Management Software: For All Sizes of Businesses
In the corporate sector, work is now optimized with digital systems utilizing the latest technologies to achieve greater accuracy. The purpose of shifting corporate data from traditional hardware devices to the cloud or online storage spaces was to keep the data safe and easily accessible at any time.
But unfortunately, criminals have also changed their tactics and are now primarily engaged in cybercrime and online scams.
Hence, the ratio of data breaches and cybercrimes has increased significantly in recent years.
To overcome these security issues and manage organizational activities through digital devices, we have wonderful security management software that was also awarded as the best for all business sizes.
- 1 : Digital Information Security & Cyber Security in Business
- 2 : What is Security Management Software?
- 3 : Select Security Management Software Based on Your Requirements

- 4 : Evaluate Based on Current & Future Needs
- 5 : Our Tips: Prevent Risks by Adopting These Actions
- 6 : Manage & Protect Your Corporate Device and Data
Part 1. Digital Information Security and Cyber Security in Business
Digital information and cyber security are the primary elements to improve the overall working of enterprises. These terms help businesses sort out all kinds of risks and threats related to data breaches.
They securely manage unauthorized access to data that can cause disruption, amendments, or failure for businesses.
Here are some important factors that companies must apply to avoid severe consequences like financial or reputational loss:
Update device software
It is easier for cybercriminals to attack devices with outdated software. Therefore, they exploit such devices more frequently. Businesses should update their devices and software regularly so they do not fall victim to cybercriminals.
Access Controls
Administrators must work on security policies to manage strong passwords and set user authorization. Access to corporate devices with multiple authentication factors and permission-based access are additional features that improve digital information security.
Security assessments
An organization must conduct security tests regularly to maintain a secure and functional working environment. Organizations should also plan incident actions for sudden cyber-attacks to secure their data.
Employee's Training
Training sessions for employees are crucial since they are responsible for the organization's overall success. They can handle cyber-attacks well if they are well-informed about security measures and precautions.
Part 2. What is Security Management Software?
Security management combines specialized tool sets developed specifically for commercial purposes.
The primary objective of it is to provide organizations with special features like MDM and UEM software, anti-virus software, and many other solutions that enhance the security of their employees, assets, and customers.
Security services use it to safeguard large businesses smoothly and efficiently. It includes protocols for organizing various security policies to control and lockdown access with strong and multi-factor authentication.
An effective security management system provides features such as alarm management, reporting and tracking, video surveillance, fire detection, and emergency response management.
Part 3. Select Security Management Software Based on Your Requirements
1. For Mobile Devices
AirDroid Business MDM is an innovative tool that empowers enterprises to remotely monitor and control corporate-owned Android devices for better management and security. It helps control and manage multiple devices simultaneously, increasing productivity.
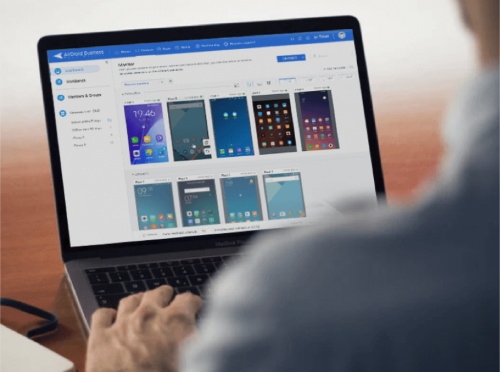
Remote Device Monitoring & Controlling
IT administrators can provide remedial solutions to employees by remotely controlling their devices. They may also access the unattended devices for immediate action if there is a risk of damage or if any necessary action has to be taken, but the individual is not responding.
App Management
The corporate device can be configured to run single or multiple apps. It also helps enhances device security by restricting apps with malicious content and increases productivity by blocking all unnecessary apps from being installed on Android devices.
Alerts & Workflows
Businesses can automate routine tasks such as app updates and device configuration to enhance efficiency. Additionally, alerts and workflows enhance security by alerting administrations about cyber-attacks and risks. For example, when unauthorized access is detected, devices lock down automatically.
Location Tracking and Geofencing
A company can track the location of individual employees in real-time through corporate devices. They can check the exact location and guide customers regarding their delivery status. Additionally, it enhances security by notifying administrators if a device enters an unsafe area.
Kiosk Mode
With this secure manage software, You can select a few apps to run on all corporate devices that your business demands. Safe web browsing in incognito mode is enabled on the devices to keep the data secure.
Creating Reports
Using reports, large enterprises can gain insight into device usage including the most frequently used apps. Reports are also used to provide metrics for evaluating security threats and to monitor compliance with policies.
Set Restriction Policy
You can impose certain restrictions on corporate-owned devices. Several device settings can be restricted, including the rotation of the screen, the camera, and the volume. It contributes to improving the security of devices by setting strong password policies and restricting apps and websites.
2. For UEM Software
Microsoft Intune is one of the best applications for unified endpoint management. It is cloud-based software that provides a single dashboard to manage all endpoint devices, including mobile phones, desktop computers, wearables, and tablets. Microsoft Intune supports businesses in customizing the security and management policies for relevant corporate devices, ensuring endpoint security.

Benefits for Businesses:
IT administrators can easily manage and protect the user identities involved in a business as a single user or as a group using Microsoft Intune.
Intune controls the devices using various policies. It uses Azure Active Directory to save devices and manage permissions. With the Admin center, businesses can easily control the devices for official use.
3. Antivirus Software
McAfee is a software company serving cyber security. It is widely used by individuals, small businesses and large enterprises because it offers a wide range of features that help every community to protect their data.
McAfee not only provides antivirus software but also provides cloud security services for cloud-based applications. VPN is another great service McAfee provides to hide the user identity and access location-based data.
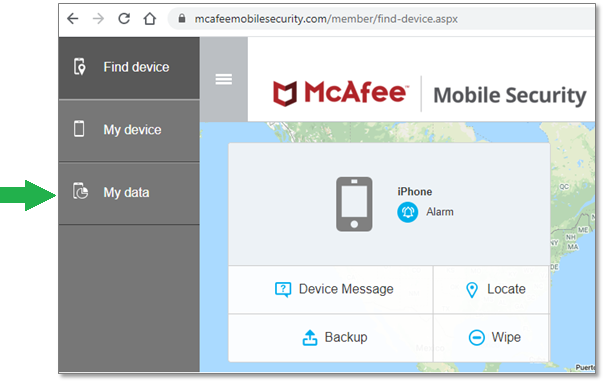
Benefits:
It provides comprehensive protection to large enterprises against cyber threats like malicious content, malware, and phishing. Additionally, it also provides advanced protection against real-time threats.
Businesses can deploy security policies and compliance to meet industrial standards, reducing costs and improving productivity.
4. Firewall and Network Security Management Software: Kaspersky Internet Security
Kaspersky software provides a two-way firewall and complete protection of your devices without interrupting their speed. With the VPN and password security management tool, you can keep your activities private and protected.
It automatically detects files with malicious content and blocks their access to devices. Its security features include expert virus check and removal, password safety check, data leak checker, stalker ware detection, app management, and anti-phishing.
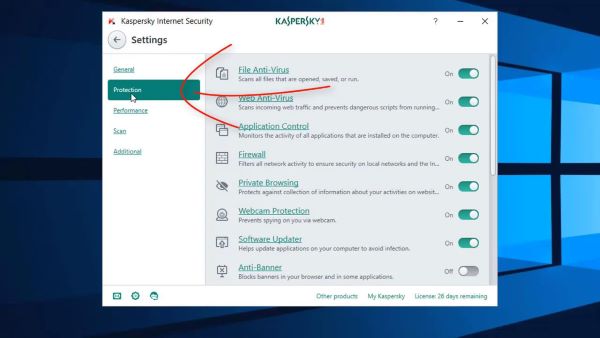
Benefits:
Its features, like a hard drive health monitor and an expert PC health check, help diagnose the devices' health and keep them fully operational.
Kaspersky also allows enterprises to provide remote IT support to troubleshoot device issues.
5. Data Loss Prevention Software
Data is a crucial element for every organization, and there are many hurdles to managing the data. Sometimes data is lost, and it causes serious concerns for the company.
Digital Guardian is a widely used tool to prevent data loss. The basic reason for its acceptability is how it helps organizations deeply monitor and protect data before it gets lost.
It is easy to deploy with minimal resources to locate and protect the organization's confidential data.
Benefits:
DLP software provides analytics and reports for threats and strategies to eliminate risks.
It reduces the stress for the team to deploy and maintain because it supports cross-platforms and is easy to use.
Part 4. Evaluate Based on Current and Future Needs
Here are the key factors that every organization must consider for better security management:
- Security: Before selecting software, confirm that an authorized developer company develops it to avoid data leakage and further issues.
- Deployment: The software must be user-friendly and intuitive to be easily deployed and utilized it.
- Costs: The cost and features of the software are two parallel things. Compare the feature list and costs with other tools, then choose the best one with more relevant features at a reasonable cost.
- Support: You must check whether the software you choose facilitates customer support for installation and maintenance. Don’t forget to verify whether they respond to a message sent using their provided contact details.
- Customization: The software must be able to change the policies and settings with time, as the business grows.
Part 5. Our Tips: Prevent Risks by Adopting These Actions
Enterprises must adapt these actions to prevent cyber security risks:
Content Filtering: Use web filtering software to classify the content on your organization’s network. The software will separate malicious websites and other threats and block their access to your devices. It will help prevent your employees from accidentally accessing unwanted and harmful content.
Log Management & Analytics: You can monitor your organization’s network activities and find potential threats to instantly remove them with the help of log management and analytics. It collects data from various sources, like network devices, servers, and applications. With this data, you can quickly analyze the threats and take quick actions to save your data.
App and Patch Update: You can keep your business secure by updating all the devices and applications instantly using security patches and updates as they become available. The risk of cyber threats increases if they are not updated regularly, as such applications and devices are more convenient to target. You can also set up schedules for routine updates.
Antivirus: Antivirus is a basic remedy that every device user must implement. Whether you are an individual user or running an organization, it is mandatory to install antivirus software that monitors every activity to detect and destroy malicious files from devices before they spread and damage the system.
Access Rights Management: Managing the access rights of every individual working in an organization is crucial. It is possible to use various management software that specifies the roles of owners, managers, admins, and other teams to define the limits of their ability to access the organization’s data. It helps keep the company’s confidential information private.
Part 6. Manage and Protect Your Corporate Devices and Data
Digital information security and cyber security are trending topics in the corporate sector. Every industry needs digital devices, and their need for cloud-based data storage and file sharing is increasing. Hence, every enterprise must adopt security policies like content filtering, auto-update of devices, and antivirus software to apply better security measures.
With the advancement in technology and diverse use of cloud computing, it has become necessary for every enterprise to regularly keep up with the emerging trends in security management techniques. The latest trends in security management include artificial intelligence and machine learning.
They help to find and eliminate threats from enterprise devices. AirDroid Business MDM is one of the best security management platform that provide a comprehensive list of features to support the trending security issues for Android enterprise devices.






Leave a Reply.