Trusted Credentials on Android: Everything You Need to Know
Android device security is one aspect you can’t afford to ignore, particularly, from an enterprise level cybersecurity perspective. Talking of Android device security, trusted credentials on Android is one of those essential security features, you ought to know, particularly, if you are running an enterprise where your team uses multiple Android devices to access services from software or websites.
If you are new to trusted credentials on Android and you don't know about its role in device security, then you are in the right place! We have compiled this quick guide to take you through a step-by-step guide on everything you need to know about trusted credentials on Android.
Part 1 : What is a Trusted Credential on Android?
For starters, trusted Credentials on Android are a collection of digital certificates that often come preinstalled on your Android device. They help authenticate the entities (mobile apps, websites, and accounts) you access using your Android device to ensure your device only communicates with genuine entities.
Your device checks whether the entity’s digital certificate corresponds with what is in its trusted credential list. If the certificate is validated, your device can establish secure and encrypted communication with the respective entity.
These certificates come from either a third-party app or trusted services like the root certificate authority. They are stored either in the system or user partition section within their respective stores.
For example, trusted root certificates are stored in the trusted root certificate authority store.
Part 2 : What Trusted Credentials Should I Disable for an Android Device?
While trusted credentials are important in securing your device's communication with other entities, disabling these credentials gives you more control of your Android device.
That said, you should only disable expired certificates, those you no longer need, certificates from sources that are not legitimate, or those that are suspicious.
If you spot spyware credentials, don’t hesitate to remove them.
Remember, you can spot suspicious certificates by simply installing a trusted antivirus on your Android device. Also, make sure you disable target trusted credentials carefully because incorrect disabling can trigger several potential consequences that can be both annoying and risky in terms of your device's security.
Always avoid disabling trusted credentials that come preinstalled in your Android because these are coming directly from the trusted/legitimate certificate authority. This means they are rarely breached compared to those later installed.
Part 3 : How to Add/Remove Trusted Credentials
While a majority of your Android trusted credentials come preinstalled, you can still add or remove them depending on your need. It is also worth noting that you should be careful what trusted credentials you are adding or removing.
Take you time to make sure the credentials you want to install come from a legitimate source.
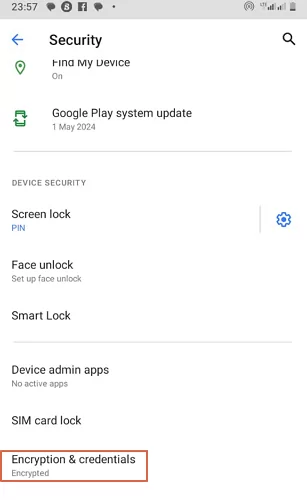
Once you are ready, here are the steps to access encryption and credential options on your Android device.
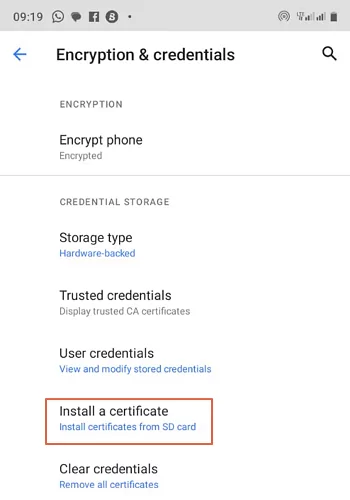
- Step 1.Once you have downloaded the root certificate on your Android, go to “Settings>Security> Encryption and Credentials then select the “Install a certificate” option.
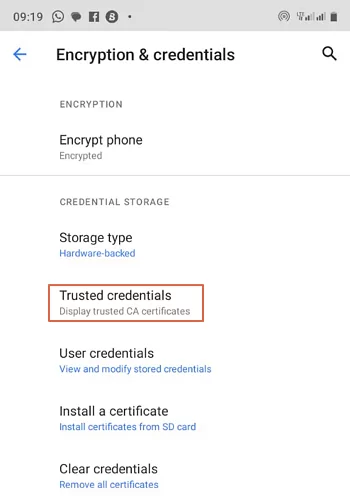
- Step 2. Scroll down and tap the “Encryption & Credentials” option. At this point, you can add or remove trusted credentials as follows.

To Remove Trusted Credentials
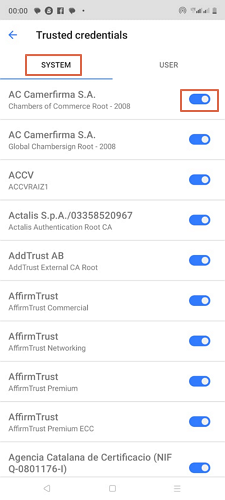
- Step 1.Choose “Trusted Credentials”.

- Step 2. In the next screen, select the category of trusted credentials you want to remove. You can select the “System” tab or “User” tab then Slide the bar beside the certificate to disable it.

To Add Trusted Credentials
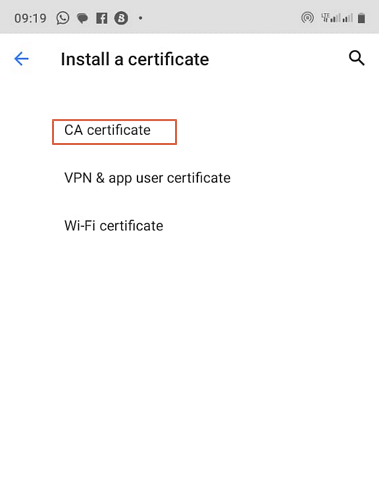
- Step 1.Choose the “Install a Certificate” option.

- Step 2.Select “CA certificate”.

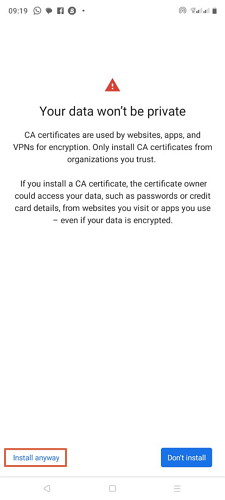
- Step 3.In the pop-up warning screen, choose the “Install Anyway” option and browse the trusted credential you want to install.

Part 4 : Risks You Should Know When Removing Trusted Credentials
While removing trusted credentials from your Android gives you the power and control you might need in your Android device, it exposes your devices to several risks including:
● Blocked access to some services and websites because your device lacks the certificates to validate them.
● Applications in your Android that depend on certificates may fail to work properly.
● If you accidentally remove legitimate certificates, you compromise secure connectivity to services and websites. This exposes your Android device to potential security risks.
● Your device might start popping up security warnings every time you try to access some websites, especially those that are SSL encrypted.
Therefore, when removing trusted credentials, be sure that the target certificate is the right one you want to get rid of.
Part 5 : MDM Solution: Credential Management on Enterprise Devices
If you are an enterprise ecosystem with multiple Android devices for employees, managing credential certificates for the safety of enterprise data and services can be a tedious task for your IT team. This is even more difficult when the devices are remotely located because you will probably commit a resource to move around the respective locations.
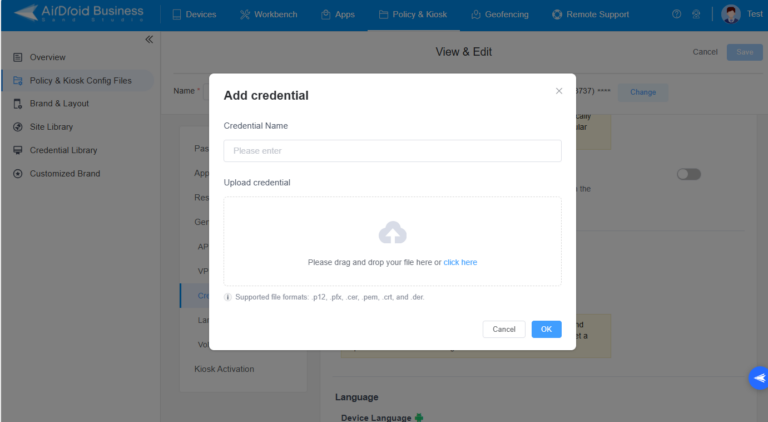
Fortunately, with a good enterprise Mobile Device Management (MDM) solution, you can seamlessly handle credential management on enterprise devices on a single platform irrespective of their location. An enterprise-level MDM solution like AirDroid for Business lets you set a credential certificate policy that transforms how you deploy and manage certificate credentials across the relevant devices in your organization.
AirDroid Business lets you add/edit the certificate policy and apply it to all devices at a go. Again, you can keep track of the expiration of all the certificates you added. In a nutshell, it helps you manage credential certificates for the safety of your device data.
Wrapping up
Trusted Credentials play a significant role in your Android devices, albeit, they can also pose risks if misused or compromised leading to data breaches or other security incidents in your business. Fortunately, you can leverage a reliable MDM solution like AirDroid for Business to set and manage credential policies for your multiple devices for data safety and secure access to services.
Frequent Asked Questions







Leave a Reply.