What Does BYOD Stand for? - Detailed Guide
The use of mobile devices for work has increased exponentially across different industries over the last few years. Instead of company-owned mobile devices, the use of personal mobile devices has become a common norm. This is because companies are adopting a modern policy called BYOD.
However, what does BYOD stand for? Actually, BYOD means Bring Your Own Device, which indicates that employees bring their personal devices to work and use them for business purposes.
In this post, we will explain every aspect of BYOD in the workplace, from its benefits and shortcomings to its working and implementation, helping you know better about BYOD.
Part 1. What is BYOD?
BYOD stands for Bring Your Own Device. It is a popular corporate policy that states that employees use their personal mobile devices for work instead of company-owned dedicated work devices. Employees connect their personal devices to the enterprise systems and networks and access corporate data as per their roles in the organization.
Starting from smartphones and tablets to desktops and laptops, employees can use any personal device for work. Most companies use internal apps that employees install on their personal devices to get access to the corporate network and perform their allotted work. BYOD policy offers more flexibility and freedom to the employees and enhances productivity with reduced expenditure.

Part 2. How Does BYOD Work?
Now that you know what does BYOD stand for, it is time to learn the working of BYOD policy. The main idea of BYOD is to securely integrate the employees' personal devices into the company's IT infrastructure. A mobile device management solution is at the heart of BYOD implementation. Here are the simple procedural steps to make BYOD work.
Device Compliance: Any personal device that any employee wants to connect to the company's network must comply with certain corporate guidelines. For example, there should be an updated antivirus, certain security measures, and customized settings to ensure device compliance.
Register Personal Devices: Employees need to register their personal devices in the MDM software. Only registered devices are authorized to access the company's network with restricted access levels.
Establishing Connection: The registered personal devices can connect to the company's network through proper authentication. Connecting through a VPN is always preferable to keep the connection private and the internal data secure.
Use Cloud-Based Apps: Companies keep their internal apps in the cloud-based repository. Any employee with a registered personal device can access the cloud-based repository to install any available corporate app. Hence, there is no need to install the apps on personal devices, and this saves device storage and prevents offline security breaches on the apps.
Part 3. What are the Advantages & Disadvantages of BYOD?
Every corporate policy comes with certain benefits along with some disadvantages. BYOD is no exception, but the benefits of BYOD outweigh the drawbacks. Here is a glance at the advantages and disadvantages of BYOD.
Advantages:
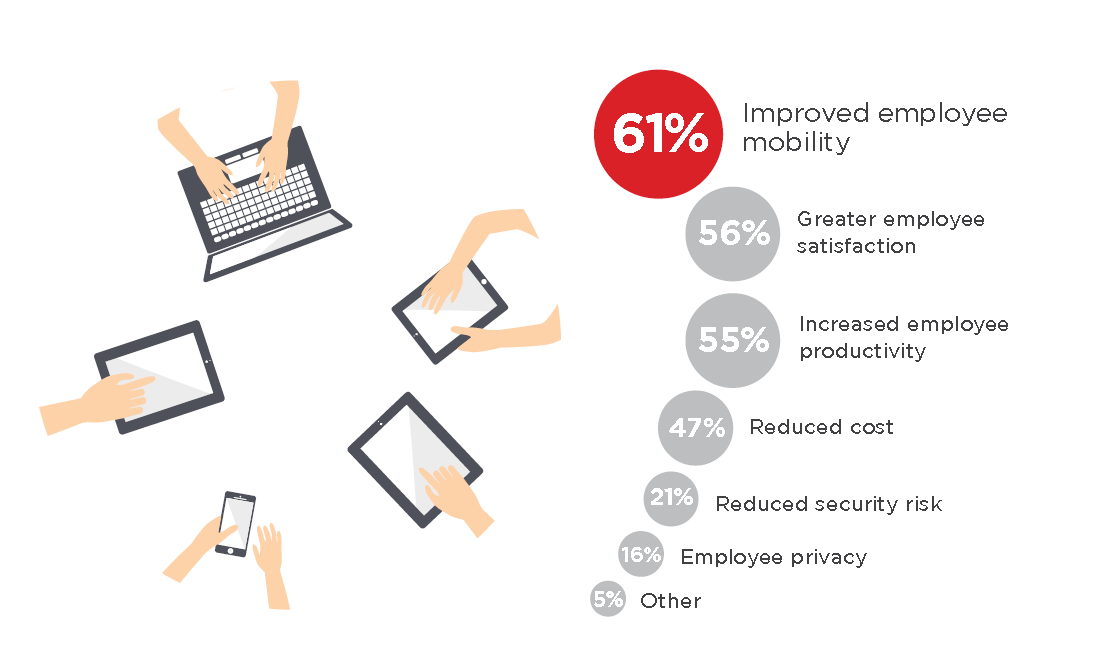
1Employee Satisfaction
Employees are more satisfied working with their devices than dedicated company-owned work devices. This is because too many restrictions exist on company-owned work devices that take time to get used. Besides, they can keep in touch with their personal stuff easily while taking a short break from work.
2Cost Saving For Employers
One of the primary BYOD benefits is that it significantly saves employers' costs. Companies do not have to purchase dedicated work devices for employees as they bring their own personal devices to work. Similarly, there are fewer expenditures on upgrading devices and device maintenance.
2Better Productivity
Since employees are more comfortable on their personal devices than on company-owned devices, productivity increases. Besides, they can instantly respond to work-related tasks from their personal devices anywhere. Moreover, employees can collaborate remotely from anywhere and be more productive in their work approaches.
Disadvantages:
1Complex Security Policies
Since personal devices can vary in terms of software and hardware specifications, it becomes difficult for companies to design a simple protocol to protect the devices from security breaches. That is why there is likely to be an increase in the complexity of different security protocols to keep the company’s network safe when accessed from personal devices.
2Greater Security Risk
The chances of a data breach are higher in personal devices than in company-owned devices. This is because employees are likely to use their personal devices for personal purposes after working hours. During such periods, employees may not follow security measures, which can put the devices in danger of security breaches.
3Distraction for Employees
Employees are likely to have personal apps installed on their devices apart from the corporate apps. Unless the employee is loyal, he can waste time accessing personal apps like social media apps and games. This is why the use of personal devices at work can be a distraction for a certain section of employees instead of productivity.
4Privacy Issue
There is a two-way privacy issue when employees use personal devices for work. The personal data and activities can get exposed to the company’s network. Similarly, sensitive corporate data can be exposed through personal devices. That is why BYOD offers limited privacy for the employer as well as the employees.
Part 4. What are the BYOD Access Levels?
BYOD policy has provisions for different access levels to ensure the privacy and security of the company’s network and corporate data. Here are the three main BYOD access levels that companies follow for employees, partners, contractors, vendors, and visitors.
1No Access
In this access level, no personal device is allowed to connect to the company’s network. This is mostly applicable to external contractors and visitors with personal devices where security measures are not followed as per the company’s policy.
2Access only for approved devices
In this access level, only the personal devices that are registered and approved by the IT admins can access the company’s network for internal data and resources. In certain cases, some external devices can have special approval and permission to access the company’s network on demand.
3Full Access
In this access level, certain employees with specific personal devices can have full access to the company’s network and resources. This is mostly applicable to the admins, top management team, and IT team.

Part 5. What is the Robust BYOD Policy?
Security is the main concern in the general BYOD policy. That is why companies modify the general BYOD policy into the robust BYOD policy that takes care of security issues. The robust BYOD policy includes all the benefits of BYOD but overcomes the challenges by implementing additional steps. Here are some important steps that the robust BYOD policy covers.
1Reliable MDM Tool
A reliable MDM tool not only regulates the BYOD access level but also monitors personal devices in terms of apps installed, app activities, and device usage and performance. It gives admins the power to remotely access the connected personal devices to uninstall malicious apps and wipe corporate data.
2Restricted Internet Access
The Internet is the source of data security in the company’s network through the connected personal devices. That is why there should be a list of websites and apps that are harmful and should be blocked from personal devices so that employees cannot access them.
3Customize Access Levels
All approved personal devices cannot have the same access levels. Rather, the access levels for personal devices should be regulated based on the roles of the employees in the organization.
4Firewalls and Antivirus
Every approved device must have the recommended firewall and antivirus installed. Admins should have the power to force update the devices with the latest versions of firewall and antivirus as and when available.
5Device Lockdown
There must be an option for the admin to lock down the connected device personal devices when the devices are stolen or lost. This will help the company to protect its sensitive data stored in the devices from external access.
Part 6. How to Support BYOD Policy Securely?
To implement and support the BYOD policy securely, you need a reliable MDM solution that can execute the policy practically. MDM stands for mobile device management, which is any software that allows IT admins to manage the personal mobile devices used by the employees for the company’s work.
Starting from registering personal devices and regulating access levels to remotely access and control the approved devices, MDM tool is at the heart of the implementation of the BYOD policy.
There are options for device enrolment as well as user enrolment. The devices can have access levels based on the roles of the users enrolled.
A professional MDM solution can blacklist websites and apps that the connected personal devices cannot access or install. This tightens security significantly by eliminating the potential sources of security breaches. Besides, an MDM tool helps the admins to fetch information about the connected devices, such as operating system version, device usage, apps installed, and their versions.
Admins can remotely control the connected devices and make changes in the settings as per the company’s security policy. Similarly, they can push updates of corporate apps and firewalls and force the devices to get them updated instantly. Additional security options like factory reset, device lockdown, and kiosk mode in an MDM tool help in implementing the BYOD policy securely.
Conclusion
We have answered your question, “what does BYOD stand for?” Since mobile work devices have become an integral part of companies dealing in technology, BYOD policy has become a popular choice due to its benefits. We have stated the advantages along with the disadvantages for proper judgment. We have also explained the working of a robust BYOD policy and how a reliable MDM solution plays a major role in implementing BYOD policy securely.






Leave a Reply.