What is a Root Certificate? An In-Depth Look at Root Certificates
Root certificates are an important aspect in internet security as they play a critical role in securing communications between your device, browser, servers, and ultimately your business. If you are hearing about a root certificate, you are in the right place.
This guide will explain everything you need to know about root certificates. Let’s delve right into it:
- Part 1 :What is a Root Certificate?
- Part 2 :What is an Intermediate Certificate?
- Part 3 :What are Root Chains?
- Part 4 :Comparison Between a Root certificate & Intermediate Certificate
- Part 5 :How to Install a Root Certificate on Android?
- Part 6 :Manage Certificates on Multiple devices to Protect Security
Part 1 : What is a Root Certificate?
A root certificate is essentially a digital certificate issued by a trusted certificate authority (CA) to authenticate software and websites you visit on your device. They often come preinstalled in your web browser and operating systems so that any time you engage a website or software, your browser or operating system checks the certificate provided by those websites against what was preinstalled.
If the certificate presented by the website/software can be verified by your browser or operating software, authentication is confirmed and trust is established. If the website or software certificate cannot be verified by your device, connection will fail to establish or you will receive a warning on the same.
Part 2 : What is an Intermediate Certificate?
As the name suggests, an Intermediate root certificate is a certificate issued by the intermediate certification authority on behalf of the trusted certification authority. This intermediate authority sits between the end user (device, operating system, web browser) and the trusted Root Certificate Authority (CA). They simply issue intermediate certificates to the end user on behalf of the trusted CA.
Beginner CAs opt to start as Intermediate CAs due to the practicalities of attaining the necessary qualifications to become a trusted CA.
Once it attains the relevant qualifications and is deemed trustworthy, the intermediate CA replaces its intermediate certificate with its own root certificates and becomes an independent certificate Authority.
Part 3 : What are Root Chains?
The root chain is a hierarchy of how root certificates are issued between the root certificate authority (CA), intermediate CA, and end entity. Also referred to as the hierarchical trust model, it captures the various certification tiers and their respective roles from top to bottom. It is essentially a three-tier chain.
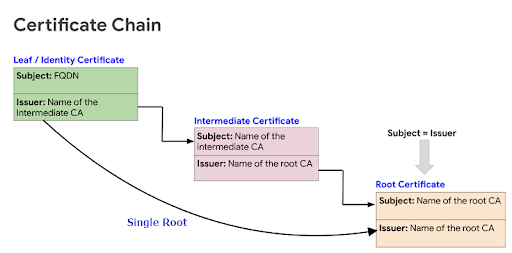
The top layer in the root chain is the end entity (websites, devices, operating systems). This layer does not issue certificates but receives them from either the CA or intermediate CA. It verifies the certificates received from these layers and establishes trust if the certificates are authenticated.
The second layer is the Intermediate CA which issues certificates to other intermediate CAs or directly to the end entities. However, it does not generate its own root certificates but rather receives them from the Root Certificate Authority.
At the bottom of the hierarchy is the Root Certificate Authority. This is the trusted authority that issues certifications to intermediate CAs or directly to the end entities (websites, devices, operating systems).
In real practice, multiple intermediate CAs exist and they can exchange certifications with each other as illustrated. Additionally, we can have a situation where there is no intermediate CA. This means the root certificate is directly issued to the entity by the root certificate authority. This is what is called a single root.
Part 4 : Comparison Between a Root certificate & Intermediate Certificate
Some of the differences between a root certificate and intermediate certificate include:
● A root certificate is issued directly to the end entity by the root certificate authority while the intermediate certificate is issued to the end entity by the intermediate CA.
● Root certificate authority has its trusted roots in stores of major browsers and operating systems. Intermediate CAs on the other hand do have these trust stores on browsers and operating systems. Therefore, the trust level of root certificates is much higher than that of intermediate certificates.
● Root certificates have a much longer lifespan of about 25 years while intermediate certificates have a lifespan lower than that of root certificates. So if the root certificate is nearing its expiration date, the lifespan of an intermediate certificate can be much lower and this adds more complexity.
● Intermediate certificates are so reliant on the root certificate authority. If its root certificate authority shuts, it also ceases to exist.
Part 5 : How to Install a Root Certificate on Android?
Sometimes, you may want to install a root certificate on your Android for testing purposes or easy authentication of the sites you trust.
When you install a root certificate on Android, it means that your Android device will automatically trust any certificate issued by that entity. It is important to note that installing a certificate that does not originate from a CA makes your device vulnerable to malware.
The following steps illustrate how to install a root certificate in Android. However, they might vary depending on your Android version and model.
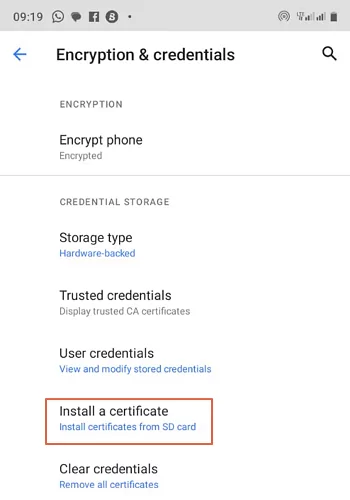
- Step 1.Once you have downloaded the root certificate on your Android, go to “Settings>Security> Encryption and Credentials then select the “Install a certificate” option.

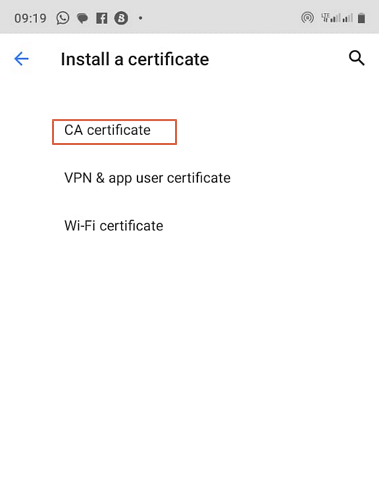
- Step 2.Next, hit the “CA Certificate” button and you will instantly receive a warning from Google.

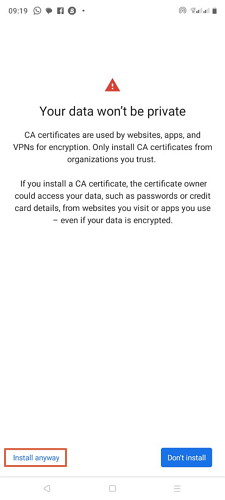
- Step 3.Hit “Install Anyway” and browse the root certificate you want to install. Once you select it, it will automatically be installed on your Android.

- Step 4.Tap “OK” on the subsequent prompt to confirm the action.
However, this certificate will be installed in the User certificate store and not the System certificate store. If you want to install it in the System certificate store, you have to root your Android device.
Part 6 : Manage Certificates on Multiple devices to Protect Security
Well, managing multiple devices to protect security in an organization can be quite complex. For one there are often multiple distributed devices that make it difficult for technical teams to deploy and manage security solutions like root certificates.
This is where a good enterprise Mobile Device Management (MDM) like AirDroid Business can help you manage and add certificates on multiple devices in your enterprise.
Here is a guide on how to add a certificate to Android phones with AirDroid Business:
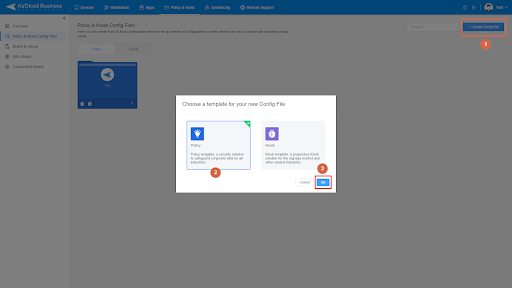
- Step 1.Log into AirDroid’s Admin Console, and head to the "Policy & Kiosk" Section on the dashboard, and click "Policy & Kiosk Config Files"to create a new policy by simply clicking on "+Create Config File".

- Step 2.Next, hit the “CA Certificate” button and you will instantly receive a warning from Google.

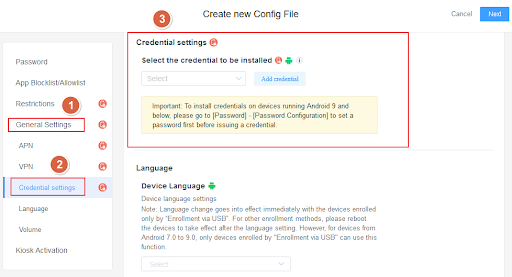
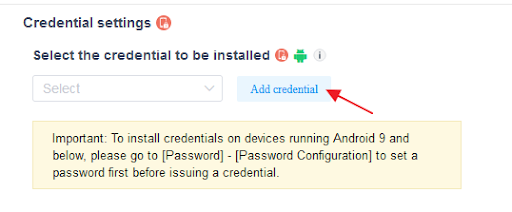
- Step 3.Click on [General Settings], and find the "Credential settings" section. Here, you can configure the "Credential settings" Policy.

- Step 4.You can then click the "Save" button on the top right corner. Head to the policy to apply it.

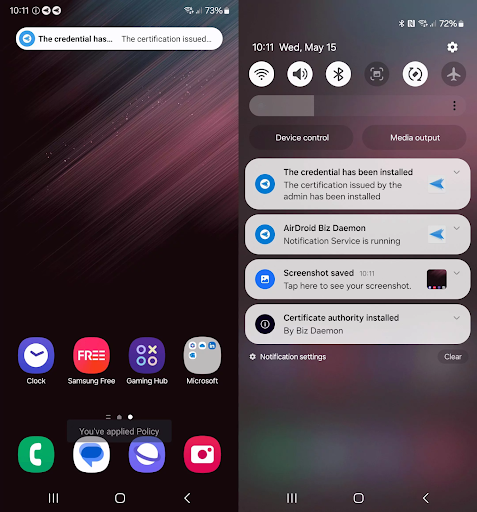
- Step 5.After applying the credential policy, you should check the application result on the target device as shown below:

Wrapping up
That’s it!We hope you now know a thing or two about root certificates more so its role in the security and safety of your business website and devices. As a business, you should manage your certificates properly across your devices using an MDM for business to ensure your sensitive data and other information are always safe from unauthorized access.







Leave a Reply.