How to Tell If Your Phone Has Been Cloned and What to Do
Are you unsure if someone has cloned your phone? When someone duplicates your phone's information and uses it without your consent, it's known as phone cloning. This may result in problems like identity theft and privacy concerns. By reading on, learn the warning indicators so you can identify cloning early and grab tips to prevent data cloning from your phone.
Can Someone Clone Your Phone Without You Knowing?
Yes, someone can clone your phone secretly by creating a duplicate of your phone by transferring its data or copying its SIM card, IMEI. Generally speaking, they used the following ways to clone your phone:
- SIM Cloning
- IMEI Spoofing
- Installation of Clone Software
- Backup and Restore
SIM cloning is the process of reproducing the data from a SIM card, including the International Mobile Subscriber Identity (IMSI) and the authentication key (Ki), to another SIM card. When someone creates a copy of your SIM card, then it can be used in their phones to access the mobile network.
IMEI is a unique identifier, like a mobile device's fingerprint. However, some malicious people tamper with the IMEI to clone phones and access calls, texts, and network services using specialized software or hardware tools.
Some phone cloners can be installed with no technical support. With physical access to your phone, someone can clone your apps, messages, calls, and more data to their phones for access.
By backing up the data on one phone and restoring it to another, someone can effectively clone your phone's data to their one.
How Can You Tell If Your Phone Has Been Cloned
If your phone has been cloned, several warning signs can help you spot it. You can detect potential cloning issues early by noticing changes in your phone's behavior. Let's learn how to find out if your phone is cloned.
1Unexpected Data Usage or Charges
One of the indications of phone cloning is mysterious data consumption or charges on your phone bill. As we mentioned above, someone can clone your phone SIM. In this way, the cloned SIM has the ability to access the same network services, make calls, and send texts as the original.
Hence, if your data consumption unexpectedly jumps or you get unexpected bills for services you haven't utilized, it might indicate that your phone has been cloned via the SIM.
2Unfamiliar Calls or Texts Status
Another sign of cloning is unfamiliar calls or texts in your logs. If there are calls or texts you didn't make in the logs, it is because the cloned phone made them.
Alternatively, if you haven't received calls for a long time, or your incoming messages might be marked as read without you seeing them, it also implies phone cloning as the calls and messages are diverted to the cloned phones.
3Service Disruptions
If your phone is cloned, you might also experience poor service or dropped calls. This happens because your network may be confused when it detects two devices with the same IMEI or SIM trying to connect simultaneously.
4Unusual Activity on Accounts
Note that the phone that cloned your SIM card can receive your text messages, which means it can use this to get verification codes from your social media apps to log in.
Therefore, if you saw notifications about login attempts or password changes on accounts linked to your phone, it is a red flag that your phone was cloned and your account is not secure.
5Duplicated IMEI Number
Your phone's IMEI number is a unique identifier. When your phone is cloned, its IMEI is copied onto another device as well. So, go to the "Settings" app to check your device's IMEI number. Then, contact your mobile network provider who can verify whether your IMEI number is unique or duplicated.
6Unknown or Hidden Apps
Someone might access and clone your phone by transferring data stored on your phone. Generally, this process requires a third-party app to implement.
Thus, it's important to review all installed apps on your phone. Some apps used for cloning could hide and run in the background, enabling phone cloning or spying.
Thankfully, you can review and audit all apps in your phone settings. Or you can protect your child's phone security by locating and controlling these hidden apps with the aid of tools like AirDroid Parental Control. No hidden or malicious application can escape AirDroid's eyes.
7Contact Carrier Support
If you suspect your phone has been cloned, contact your mobile operator. They can check for and confirm any suspicious activity on your account, like the issuance of unauthorized devices using your number.
Is There Any Code to Check If the Phone Is Cloned?
No, if you're looking for code to check if the phone is cloned, I'm sorry to tell you that no such code can hit all. However, you can check your device's IMEI number to help identify if it's cloned. If your IMEI number is duplicated or fails to match, it may indicate cloning.
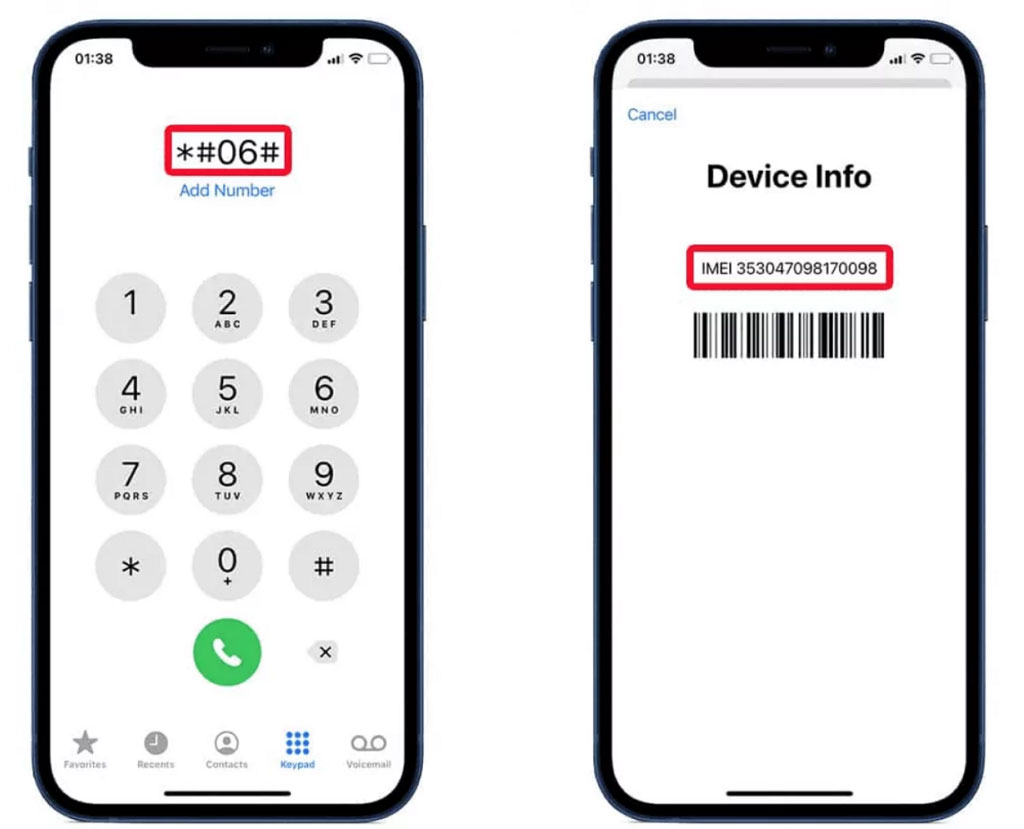
Here's how you can tell if your phone has been cloned by typing the code to check your IMEI:
- Step 1.Open the dialer app whether you are using an iPhone or Android.
- Step 2.Dial *#06#, and your IMEI number will appear on the screen.
- Step 3.Write down the IMEI and compare it with the one in your phone's settings or on the box it came in. If they differ, this could be a duplication or tampering.
- Step 4.You can also verify the IMEI with your carrier to check for irregularities or cloning signs.
What to Do If Someone Cloned Your Phone
If you confirm that your phone has been cloned, take immediate action to secure your data and protect your privacy. Here's how:
Of course, if you know who cloned your phone, contact him or her in advance and request to stop cloning and accessing your phone.
Update Your Passwords
Make sure to update the passwords on all of your accounts, such as social media, banking, and email. You need to use different and strong passwords for every account you have. To further secure your account, turn on two-factor authentication.
Switch to Another SIM or Phone
If you are a victim of SIM cloning, simply changing your password is not enough. So, we suggest to change another SIM card. But before proceeding, don't forget to update the phone number in accounts to avoid losing access, especially when you tend to use numbers for 2FA or account recovery.
Report to Authorities
It's illegal to clone your phone without your knowledge. So, contact local authorities and report the cloning incident. They can investigate the situation, assist in tracking down the perpetrator, and advise on further security measures. Reporting the crime also ensures there is a record of the problem that may need to be fulfilled for further legal or financial protection.
Factory Reset Your Phone
A factory reset wipes your phone clean of all data, including any malicious software or unauthorized apps installed by the hacker. After resetting, reinstall only trusted apps and restore data from your backup. This step ensures your phone is free of any hidden threats that may have resulted from cloning.
How to Prevent Phone Cloning
To reduce the risk of your phone being cloned or hacked right now or in the future, you can follow these simple practices.
- Avoid Public WiFi: Do not use public WiFi for sensitive activities, such as banking or even when trying to sign in to personal accounts, because they probably intercept your information.
- Avoid Suspicious Links: Don't click on strange links in emails, text messages, or websites. They could lead to malicious software that clones your phone.
- Be Vigilant about Phishing: Be careful of those spam emails and messages that seek to acquire a copy of your personal information. This is often one way hackers steal data.
- Let Your Phone Always in Your Sight: If someone else is physically accessing your phone, please keep an eye on them to prevent them from cloning your phone. If you're using an iPhone, you can also use the Guided Access feature, which limits your device to a single app.
- Do not Jailbreak your Phone: Jailbreaking your phone compromises your security settings, making you more liable to being cloned or hacked.
Conclusion
In a nutshell, phone cloning is a serious threat to personal data and privacy, as well as unpredicted charges or other strange activity on one's phone. However, being alert can help you identify and react quickly to those cases. Remember the precautions: strong passwords, reporting issues immediately, and not engaging in risky behaviors such as using public WiFi or clicking on suspicious links.







Leave a Reply.