[Explained] What Is Remote Desktop Port 3389
The demand for remote connectivity to desktops in the distributed workforce has introduced many remote access technologies. However, Remote Desktop Protocol (RDP) via port 3389 is the standard and popular way to access and control desktop computers remotely.
Using RDP port 3389, a user can connect and control the remote desktop as if they are sitting in front of it. In this guide, we will explain in detail the remote desktop port 3389, covering its working principle, security risks, and other details.

Part 1. What Is RDP Port 3389?
A port is a virtual endpoint where network connections begin and end. It is a software-defined number linked to a network protocol and managed by the computer's OS. Every port is linked to a specific service/process. It helps the computer differentiate between the different nature of traffic. For example, the port for email is usually 25 for SMTP, while it's 80 for HTTP and 443 for HTTPS.
Port 3389 is the default port for Microsoft's Remote Desktop Protocol (RDP). It facilitates remote access to Windows computers via the RDP. RDP is Microsoft's proprietary protocol that empowers remote connections to another computer or server. Simply put, the RDP port 3389 is vital to enable remote desktop connections to other computers and transmit data such as screen visuals, mouse/keyboard inputs, etc.
Part 2. How Remote Desktop Works Using Port 3389?
A remote desktop is a physical computer/server that a user can control from a far location via a network connection.
To better understand how port 3389 facilitates remote desktop connections, let's discuss the steps on how remote desktop connections are established and the role of port 3389 in the connection process:
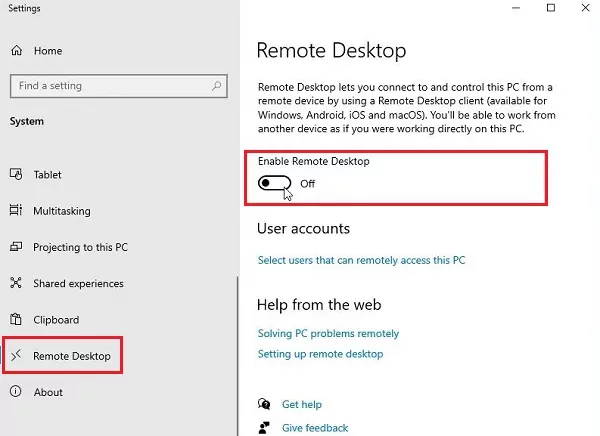
Step 1. Enabling Remote Desktop Option
The first step is to enable Remote Desktop on the remote desktop. To do so:
- Click Settings > System > Remote Desktop.
- Enable Remote Desktop and confirm.
- Fastest app that can root any Android devices.
- Safe and riskless
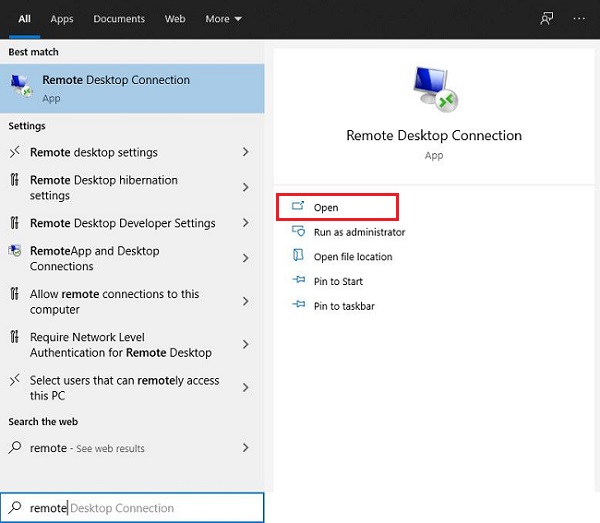
Step 2. Send the Remote Connection Request
From the Start menu, search for remote desktop connection and click the best match option.
Enter the remote desktop name or IP address and click Connect.
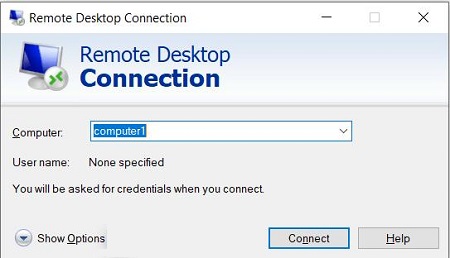
Once done, the remote connection request is sent to the remote desktop. The request targets the RDP port 3389 on the remote desktop, as the remote server listens to this port for all the incoming RDP connections.
You may also be asked to enter the login credentials to access the remote desktop. These credentials are also transmitted through the port 3389.
Step 3. Session Initiation and Data Transmission
Once the connection is completed, you can access and control the remote desktop from your local computer. Here, the role of remote desktop port 3389 is to facilitate data exchange, such as screen updates, keyboard/mouse inputs, and other controls. This way, port 3389 acts as a crucial data transmission point during remote sessions.
We can sum up the role of port 3389 in the connection process in the below three points:
- Serve as the entry point for all RDP connection requests
- Transmit user credentials.
- Transmit data back and forth between the local and remote desktop during the entire session.
Part 3. Security Risks of Port 3389
The port 3389 is crucial for remote desktop connections but comes with security risks. Hackers can leverage the open nature of this port to compromise security and penetrate systems.
Here are some of the key security risks of port 3389:
Brute-force Attacks
A brute-force attack is a hacking technique where attackers use trial-and-error to guess the login credentials. Attackers find exposed RDP servers on the internet and conduct brute-force attacks to breach credentials. So, if you have set a weak password, attackers can crack it and get unauthorized access to the system.
Misconfiguration
It is not uncommon for users to misconfigure remote desktop connection (RDP). For example, RDP servers may be unintentionally exposed directly to the internet. These misconfigurations provide a gateway for attackers to penetrate into the system.
Security Vulnerabilities
In the past, many known vulnerabilities linked to RDP were exploited by hackers. For instance, BlueKeep was the security vulnerability related to RDP (CVE-2019-0708), which allowed attackers to connect to an unpatched target system using RDP.
Man-in-the-Middle Attack
RDP clients do not verify the identity of the RDP server when initiating encryption. This vulnerability allows attackers to intercept traffic and establish their own encryption. This leads to a "man-in-the-middle" attack where sensitive data can be exposed.
Best Practices to Secure Remote Desktop Connections
Although port 3389 has security risks, they are avoidable if you play your cards correctly. In this perspective, below are a few best practices to secure remote desktop connections:
- Strong Password: Set up a strong password for RDP access that combines uppercase/lowercase letters, numbers, and special characters. A strong password will make brute-force attacks ineffective.
- Use Network Level Authentication (NLA): NLA is a security measure that needs user authentication to access a network server. Enable NLA to protect the system from malicious attacks.
- Limit Access by IP Address: You can configure firewall rules, specify trusted sources (IP addresses), and ensure that only those sources can access the system via RDP.
- Use VPNs: A Virtual Private Network (VPN) creates an encrypted connection between the user and the remote server. In this approach, a user must connect to a VPN before accessing the remote desktop. This eradicates the concern of exposing port 3389 to the public internet and man-in-the-middle attacks.
- Keep System Patches: Keep Windows servers and clients patched with new security patches. This helps address security vulnerabilities before hackers exploit them.
In short, you can secure RDP port 3389 in multiple ways. All it requires is carefully evaluating the loopholes and implementing security measures accordingly.
Part 4. How to Change the Default Port 3389
Some users tend to change the default RDP port 3389 to a different one due to multiple reasons, such as:
- Hide the RDP host from port scanners that search for Windows hosts on the network with an open 3389 port.
- Reduce the chances of becoming victimized by RDP vulnerabilities.
- Reduce brute force attacks.
- Bypass network restrictions where remote desktop port 3389 is blocked.
Here are the simple steps to change the default port 3389:
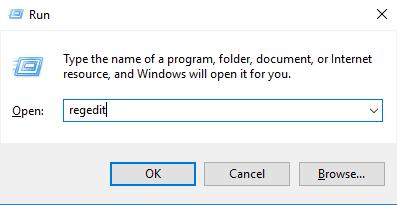
- Step 1.Press Win + R and type regedit in the Run dialog box.
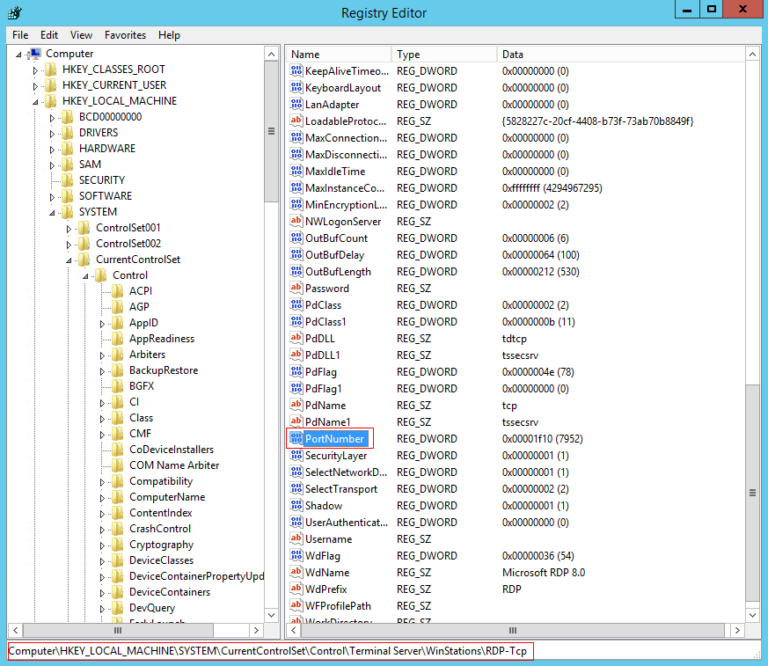
- Step 2.In the Registry Editor, go to
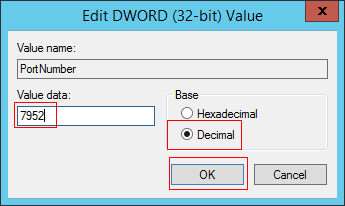
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp - Step 3.Double-click PortNumber.
- Step 4.Check the port number and click OK.
- Step 5.Restart your computer.
This way, you can easily change the RDP default 3389 port to a different one.
Precautions to Take When Changing the Port
- Make sure the firewall allows traffic from the new port. If not, you should update the firewall rules.
- Choose the port that is not commonly used by other services.
- Note down the port number.
- Set your network profile to private to add an extra layer of security.
Part 5. Better Remote Desktop Solutions
Configuring and using Microsoft Remote Desktop is complicated and vulnerable to security breaches. So, what if we tell you there is an even easier, faster, and more secure remote desktop solution? This solution is known as AirDroid Remote Support.
AirDroid Remote Support is a powerful all-around remote access and support solution for businesses. It provides an internet-based pathway to connect to a remote computer or smartphone from another computer or smartphone. There is no involvement of port 3389, which makes it more secure and reliable.
Why AirDroid Remote Support is the best remote desktop solution is evident from its below list of features:
- Real-time Remote Control: Seamless interface to connect and control remote computers or smartphones over the internet connection.
- Screen Sharing: Mirror a remote computer screen to provide support.
- File Transfer: Drag-and-drop support for file transfer.
- Messaging and Voice Chat: Support text messages and voice chat during the remote support session.
- Black Screen Mode: Patented black screen mode to turn the screen of the controlled device black and protect confidential content.
- Controllable Keyboard and Clipboard: Control the keyboard and clipboard of the remote desktop
All the above features of AirDroid Remote Support make it a comprehensive remote support solution for quick IT support, secure remote work access, better customer support, proactive monitoring, and more.
In short, AirDroid Remote Support is a modernized and advanced remote access solution and an ideal alternative to Microsoft Remote Desktop Protocol (RDP).
Conclusion
Port 3389 is a dedicated port for Microsoft's Remote Desktop Protocol (RDP) and facilitates remote desktop control. However, it is one of the favorite targets of hackers due to its vulnerabilities and more chances of unintentional misconfigurations. Therefore, you have to make sure to secure the RDP port 3389 using the above tips and tricks. In contrast, you can avoid that all by using AirDroid Remote Support, the most convenient, secure, and fast way to remote control computers.










Leave a Reply.