- Keep control with encrypted connections.
- Access files and manage apps securely from anywhere.
- Get notifications without risking your data.
- Log out remotely to keep your privacy intact.
- Transfer files seamlessly without sacrificing security.
How to Stop Someone from Accessing Your Phone Remotely [2025 New Updated]
Reliable remote support tools are key to smooth remote work.
Try AirDroid Remote Support for free to enjoy smooth remote control or help on your devices.

Imagine this: You're home, relaxing after a long day, scrolling through your phone's photos and messages. Suddenly, something strange happens—apps open on their own, or your friends receive messages you didn't send. It hits you: someone might be controlling your phone remotely.
It's unsettling to think about, but it's more common than we'd like. If you're concerned about this, don't worry. We'll walk you through how to stop someone from accessing your phone remotely.
How Much Do You Know about Remote Access?
Remote access was originally made to help professionals fix problems or get files from afar. Now, it's more common and riskier, as almost anyone could potentially control your phone without you knowing. They could:
- Spy on you through your phone's camera and microphone.
- Mirror your phone's screen to watch what you're doing.
- Track your location and know where you are.
- Read your private messages, look at your photos, and even access your bank details.
- Intercept or send messages and make calls using your phone.
- Sync your contacts, passwords, and other sensitive information.
We'll call out some of the more obvious signs below that indicate someone is remotely accessing your phone.
7 Signs to Tell If Someone is Accessing Your Phone
If you think someone might be accessing your phone remotely, there are seven signs to watch for.
| Signs | Description |
|---|---|
| Apps Opening or Closing Automatically | Applications on your phone may open or close without any manual input. |
| Unexplained Replies to Messages or Emails | Messages or emails are being replied to without your input, and you haven't set up any automatic responses. |
| Screen Flickering or Anomalies | Your phone screen might flicker or briefly go black. |
| Microphone or Camera Activation | If your microphone or camera activates without you using any related app. |
| Surge in Data Usage | A sudden and unexplained spike in your phone's data usage could indicate that someone is transmitting data from your device. |
| Unusual Heating or Rapid Battery Drain | If your phone heats up excessively or the battery depletes quickly without significant use, it may suggest that remote access software is running in the background, increasing the device's workload. |
| Unexpected Notifications | You might receive unusual notifications, such as alerts from security software or unexpected system permission requests. |
How to Stop Someone from Accessing Your Phone Remotely
If you suspect that someone is remotely accessing your phone, follow these steps immediately to cut off their access:
- Close all running apps and exit any background processes.
- Disconnect all connections and turn on Airplane mode.
- Go to Settings > Apps and check for any unfamiliar apps. Uninstall any that you do not recognize.
- Go to Settings > Privacy Settings/App Permissions to see which services and permissions are active. If anything looks suspicious, remove their access.
- In Settings > VPN, look for any VPN profiles you don't recognize and remove them.
- Restore network settings, app preferences, and privacy settings to their default states.
- Use the built-in security app to scan for any malware or suspicious apps and services.
- Update passwords and security settings.
- Change your phone's lock screen password, and update your facial recognition and fingerprint settings. Also, update passwords for app lock, like Note apps, File Managers, WhatsApp, etc.
NOTE: Once you've done all these steps, you should have cut off any remote access to your phone. But keep in mind, there's still a chance someone could get back in when your phone goes online again. So, after reconnecting, back up your phone and then do a factory reset.
11 Tips to Prevent This from Happening Again
Worried about someone continuing to access your phone remotely? Try these preventive measures:
1. Reset your Wi-Fi and set a new password.
2. Check the accounts linked to your phone, like Google, Samsung, or iCloud, for unfamiliar logins or devices.
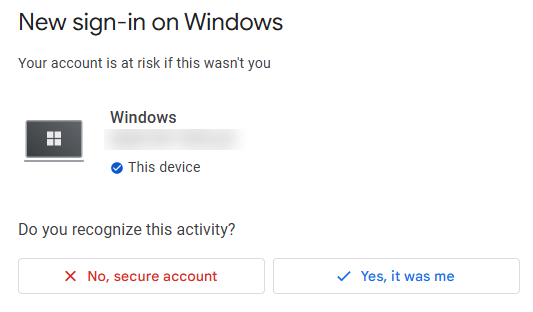
For example, on Google, visit https://myaccount.google.com/, go to Security > Recent security activity, and see which devices are logged in. If you find any unfamiliar devices, click on them and choose "No, secure account" to remove them.
3. Regularly update your account passwords, including personal, social media, and email accounts, and make sure two-factor authentication (2FA) is enabled.
4. If your account has recovery contact options, check for any unfamiliar numbers or emails and remove them immediately.
5. When using Bluetooth or screen mirroring, especially with someone else's device, don't select "Always trust this device." Ensure you disconnect completely after each use.
6. Keep your phone's system updated to protect against viruses or suspicious apps.
7. Avoid connecting to untrusted hotspots or public Wi-Fi.
8. Only install apps from official sources, and avoid downloading APKs from unknown websites.
9. Be cautious with app permission requests, only granting those that are necessary.
10. If you have call forwarding set up, verify the number is yours, and change it if it's not.
11. Enable usage tracking features like Screen Time or Digital Health to see if apps or services are consuming resources when you're not using them.
12. Be wary of links from unknown sources.
Bonus: Worry-Free Remote Access and Control on Your Phone
Sometimes, it's not about clicking a sketchy link or downloading a virus. It might just be that you used a remote transfer tool and forgot to log out, especially on a public device. This can open up your phone's content to prying eyes. If you're worried about that, check out AirDroid Personal. It's a free and secure tool for remote file transfers that helps you:
Conclusion
Now that you know what to do to stop someone from accessing your phone remotely in case it does happen, you can rest assured. With just a little precaution, you shouldn't have to face this problem. Thanks for sticking around till the end!
FAQs














Leave a Reply.