[Explained] What Is TCP Port 135 and What Is It for?
TCP ports are integral components that help direct traffic to the appropriate services on your computer, and each port corresponds to a specific application. For this reason, it is important to understand what they are and how they can affect your device. TCP Port 135, in particular, plays a significant role in network communications, especially in the Windows OS.
In this article, we will delve into what TCP 135 is used for, its security implications, and what's the best way to enhance the security of your device.
Part 1. What Is TCP Port 135 Used For?
TCP Port 135 is essential when you want to connect remotely clients and servers. In reality, it is primarily used for RPC endpoint mapping. To make things clearer, RPC (Remote Procedure Call) is the protocol that an application utilizes to request a service from an app found on another device in the same network. Therefore, it allows software to communicate and request services over a network, making remote support possible.
With TCP 135, you are signaling what services are available on your device. In addition to this, you are also showing what ports other devices can connect to them. For this reason, it is easy to understand that port 135 is crucial for remote access, management, and support.
As we've already mentioned, port 135 is mainly used for RPC communications. In more detail, it is used in:
- Microsoft DCOM Services – DCOM relies on RPC services for communication, and TCP 135 helps it locate the appropriate service endpoint.
- Windows Management Instrumentation – a WMI connection can succeed only when the remote device has permitted incoming traffic on port 135.
- Windows Remote Management – WinRM uses this port to facilitate remote management capabilities.
- Microsoft Exchange Servers – MS Exchange Servers utilize TCP port 135 for some administrative and operational tasks.
Part 2. Is Port 135 a Security Risk?
Given the role of this port, it is easy to understand the security implications it has. It is a fact that many cyber-attacks target this particular port due to its accessibility and its role in remote communications. For example, port 135 is often associated with:
- Unauthorized Access – when you leave port 135 open, you might open a road for potential data breaches. Hackers can exploit the open port to gain unauthorized access to your network, making you vulnerable to various malicious activities and attacks.
- Denial of Service (DoS) Attacks – it is known the RPC contains a flaw that will make it fail upon a malformed request to port 135.
- Worms – the Blaster worm is one type that has been widely used to exploit vulnerabilities in the RPC services. The worm allows access via various ports and manages to spread over port 135.
- Spam – port 135 is exploited in popup spam in messenger services within a network.
All of these risks highlight the importance of robust security measures. One of these is to learn how to avoid the vulnerabilities that are associated with the TCP Port 135.
Part 3. Should Port 135 Be Open?
Since there are so many risks when it comes to TCP 135, you might be wondering whether you should leave it open or not. The truth is that there is no definite answer to this question since it highly depends on your specific network requirements and your overall security measures. However, we can compare these two cases so that you can draw your own conclusions.
Case 1 – TCP Port 135 Is Open
In the first case, we are examining the pros and cons of leaving port 135 port. The most significant benefit is that you can rest assured that your RPC communications will function correctly. You and the other network administrators will be able to access and manage your devices remotely.
Nevertheless, the drawback of leaving this port open is that you are also leaving your network open to potential attacks. We have already explained the risks in the previous section.
Case 2 – TCP 135 Is Closed
The second case explains the pros and cons of having TCP 135 closed. The advantage is that you eliminate the risks associated with this particular port. If you are concerned about your security, this is something you should carefully consider.
However, closing port 135 means that the apps and services that rely on RPC communications might fail. This might disrupt your business operations, especially if remote management is essential for your organization.
Steps to Open and Close Port 135
One simple solution to this issue is to learn how to open and close port 135. This way, you can open it when you need it and close it when you won't be using it. In this section, we are going to show you how to open and close it.
To open the TCP port 135:
- Step 1.Click the Windows icon, go to Settings > Update & Security, and click Windows Security from the sidebar.
- Step 2.Click Firewall & network protection and then click the Advanced settings option.
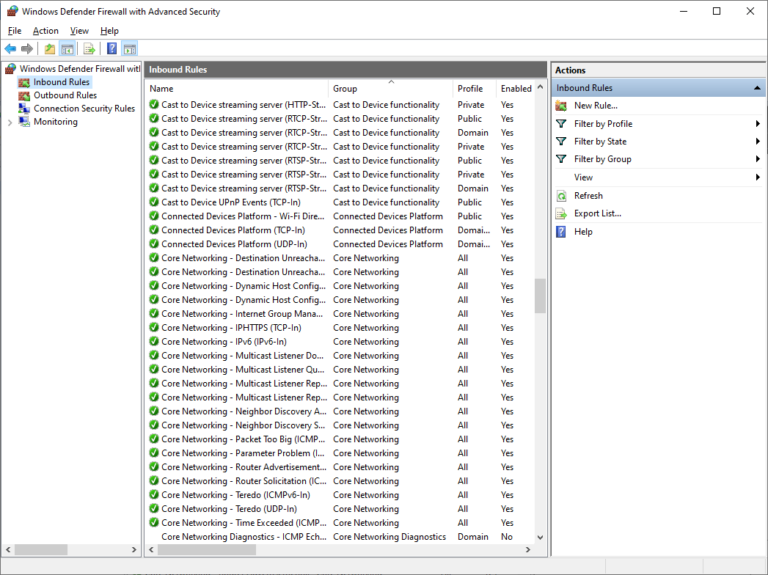
- Step 3.In the new window, click on Inbound Rules from the left sidebar, and New Rule from the right sidebar.
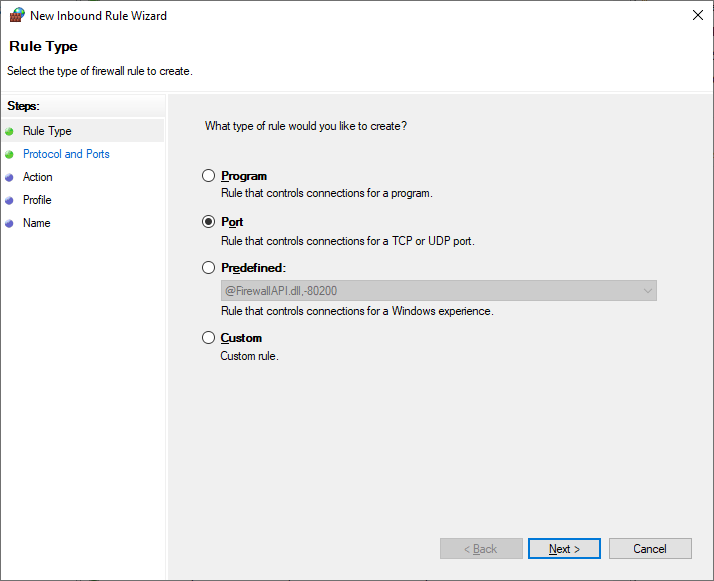
- Step 4.Select the Port option and click Next.
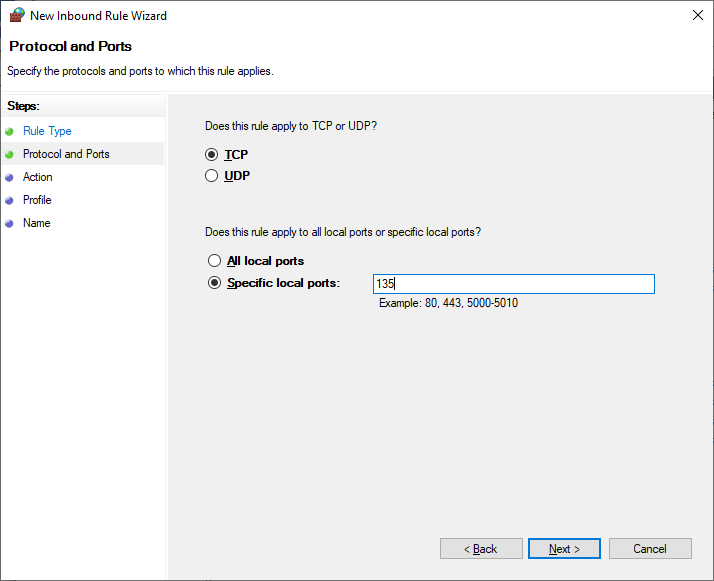
- Step 5.Choose the TCP option and type 135 in the Specific local ports field. Click Next to continue.
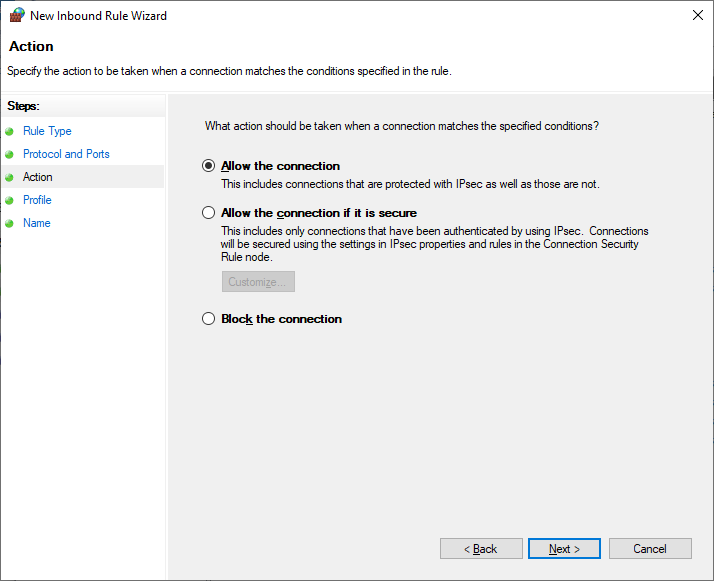
- Step 6.Select the Allow the connection option and click Next.
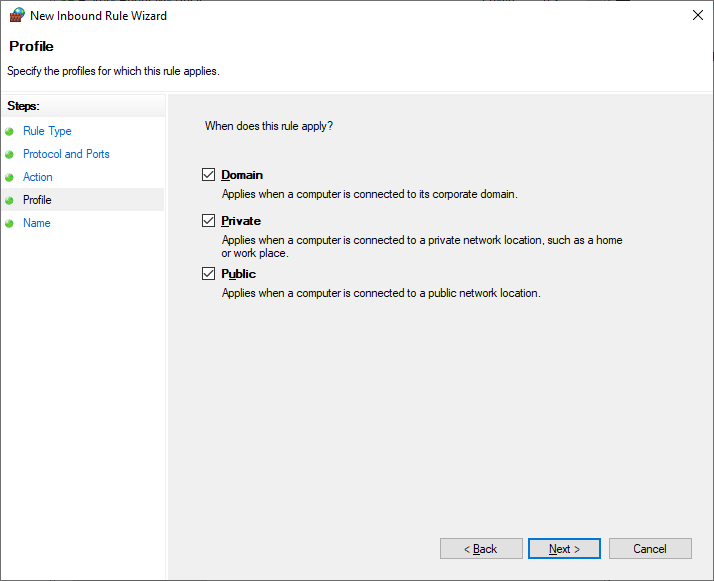
- Step 7.Specify when the rule applies by checking the appropriate option, and click Next.
- Step 8.Give a name to the rule you have just created and click Finish to save it.
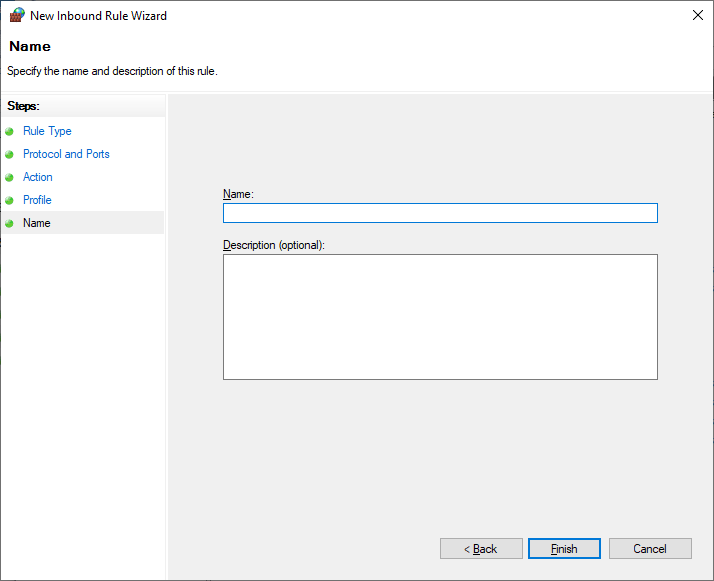
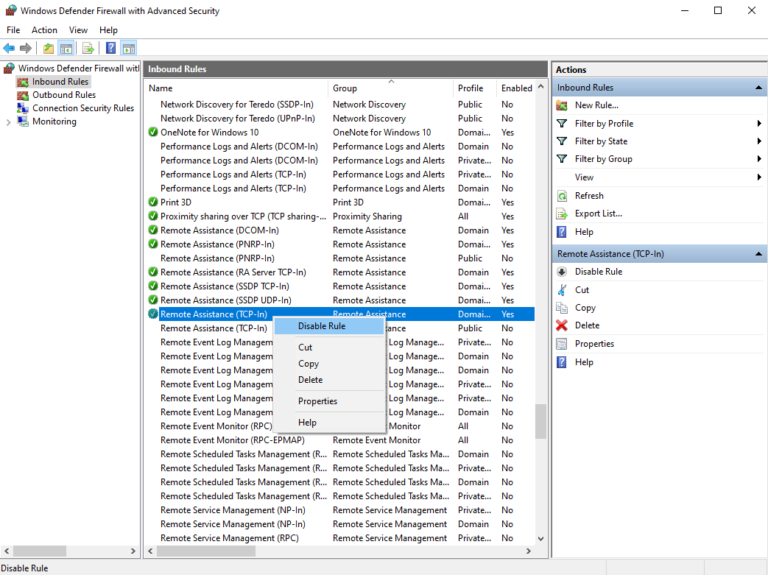
To close the TCP 135:
- Step 1.Follow the steps 1 and 2 from the above guide to access the Inbound Rules window.
- Step 2.Find the rule that allows traffic on port 135. For example, it can be the rule you have created above.
- Step 3.Right-click on the rule and click Disable Rule to temporarily close it or Delete to completely remove it.
Part 4. Most Secure Remote Support Software – AirDroid Remote Support
If the security issues associated with port 135 concern you, the best solution is to find another secure and reliable remote support tool. AirDroid Remote Support stands out as a great option that will satisfy your needs for quick, easy, and secure remote assistance. The app has been designed with both security and convenience in mind, and for this reason, it boasts a set of innovative features that facilitate the process.
But what makes AirDroid Remote Support such an essential tool for your organization is that it takes your security seriously. The app ensures that remote sessions are secure, with end-to-end encryption, thus protecting your data during transmission. Other key features include:
- Screen Sharing – you can easily share your screen in real-time to provide synchronous assistance and accurate troubleshooting.
- Voice and Text Chat – communicate effectively with the person you are assisting via voice and text.
- Controllable Clipboard and Keyboard – make the most out of your remote connections by taking over keyboard control operations.
- Permissions & Management – assign permissions to the team members and devices that are going to use remote assistance to enhance protection.
- Black Screen Mode – one of the innovations that the app brings to the table is this mode that blacks the screen of the unattended device so that you can continue working without worrying about the privacy of your data.
In Conclusion
TCP Port 135 plays a critical role in network communications. However, you should also be wary of the security risks that it’s hiding. If you place great importance on security, AirDroid Remote Support offers a compelling choice, allowing you to avoid the port 135 risks. Try AirDroid Remote Support today to experience an enhanced remote assistance experience.








Leave a Reply.