How to Fix the “Encryption Type Requested is Not Supported by the KDC” Error?
Are you facing RDP connection errors and the active directory is unable to authenticate users? Your KDC encryption might be failing while disrupting your network security, leaving you puzzled and searching for solutions.
The issue might be your service account configuration to support encryption algorithms. Or Your group policy on domain controllers or clients may limit the allowable encryption types.
Whatever the reason, we'll walk you through the simple steps to diagnose and resolve this error, so that your system's encryption settings align perfectly for smooth authentication operations.
Reasons for Kerberos Authentication and Encryption Errors
If you face errors during Kerberos authentication and encryption between the client and KDC, the common reasons include:
1. Unsupported Encryption Type
Some older encryption types, such as DES or RC4, may no longer be supported by modern KDCs or may be disabled for security reasons. If the client requests an unsupported encryption type, the KDC will reject the request.
The KDC and client might have different encryption policies. So, it’s better to use newer encryption types like AES for both client and service accounts.
2. Kerberos Configuration Mismatch
Misconfigurations in the Kerberos settings on either the client or the KDC can result in unsupported encryption types. This often occurs when there’s a version or policy mismatch.
Also, incorrect settings in the client’s Kerberos configuration files or registry could lead to requesting an encryption type not accepted by the KDC.
3. Group Policy Misconfigurations
You may face an error due to conflict between the custom local or group policy settings and the service account's properties in Active Directory. When the network security allowed for Kerberos policy is set to allow only AES or newer encryption types, the server will no longer support older Kerberos encryption types in Kerberos tickets.
Also, by default, user account objects in Active Directory are not configured to use Kerberos AES encryption. Hence, the server won’t be able to negotiate encryption type for tickets.
Troubleshoot “KDC Has No Support for Encryption Type” Error
To resolve the " encryption type requested is not supported by the KDC" error, follow these steps:
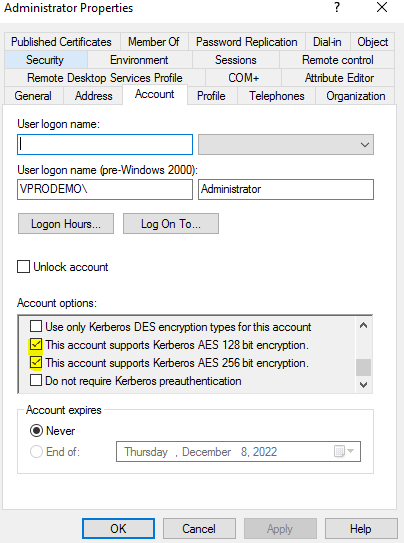
1Enable the AES Encryption for the Service Account
If the server is set to require AES encryption for Kerberos, but the service account in Active Directory has not been updated to support AES encryption, it leads to error messages. This is because the server cannot negotiate a compatible encryption type for Kerberos tickets.
To identify and enable Kerberos AES encryption for pool and service accounts, follow these steps:
- Step 1.Identify the Accounts: Determine all the accounts used as application pools and service accounts.
- Step 2.To locate the accounts in Active Directory, open Active Directory Users and Computers.
- Step 3.Locate the identified accounts.
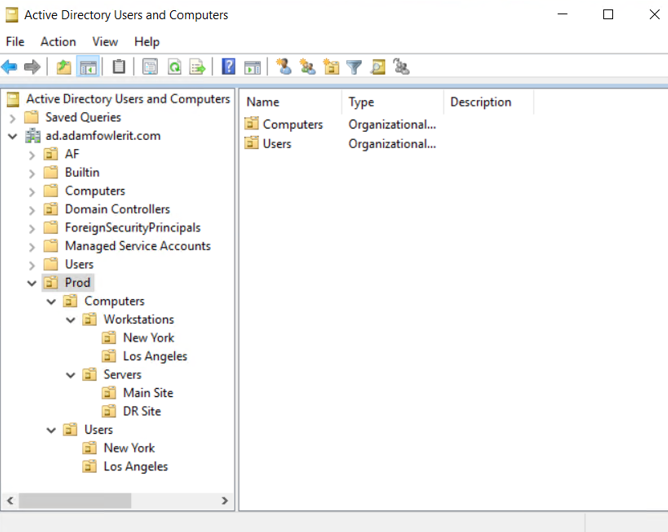
- Step 4.Modify the account properties by right-clicking the account and selecting Properties.
- Step 5.Navigate to the Account.
- Step 6.Ensure that one or both of the following options are selected:
This account supports Kerberos AES 128-bit encryption
This account supports Kerberos AES 256-bit encryption

- Step 7.Perform an iisreset on the servers.
- Step 8.Restart any SharePoint-related services running under the modified service accounts to apply the changes.
This process ensures that Kerberos AES encryption is supported for the service accounts, improving security and allowing proper authentication.
2Configure the Network Security Using the Group Policy Management Console
To allow only secure encryption types like AES, use group policy. You can configure the network setting through the following steps:
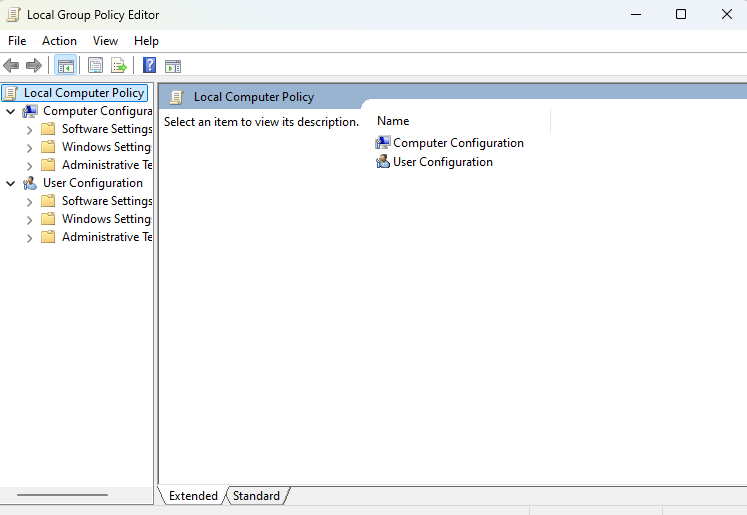
- Step 1.Open the Group Policy Management Console (GPMC) by typing gpmc.msc in the Run dialog or Start Menu search.
- Step 2.It will open the Local Group Policy Editor Window.

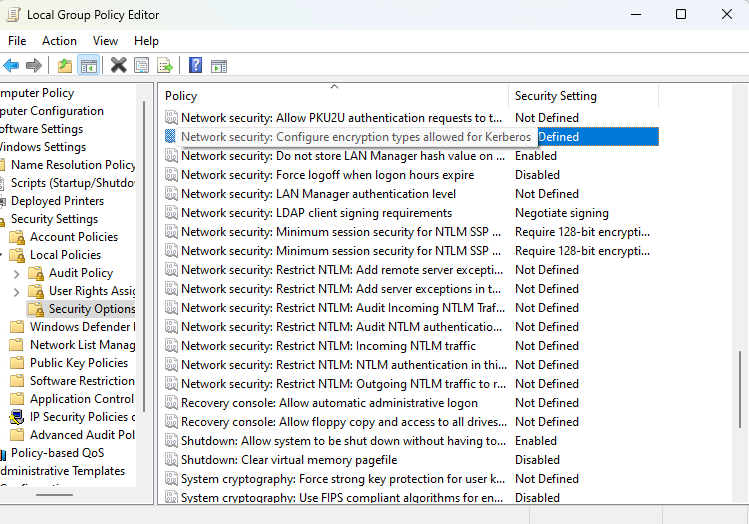
- Step 3.Navigate to:
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options. - Step 4.Locate and double-click the policy "Network Security: Configure encryption types allowed for Kerberos".
- Step 2.It will open the Local Group Policy Editor Window.
- Step 5.Check AES128_HMAC_SHA1and AES256_HMAC_SHA1 to enable these encryption types. If necessary, you can also select RC4_HMAC_MD5 for legacy support, but DES should remain unchecked for security purposes.
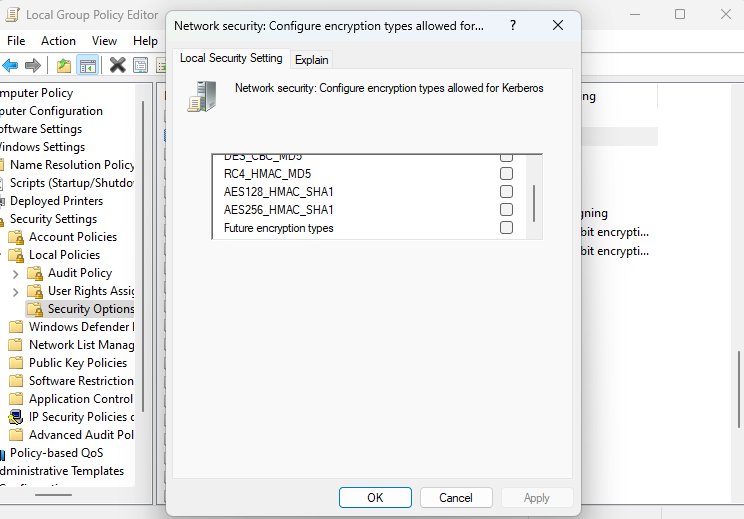
- Step 6.Click OK to apply the policy changes.
- Step 7.Close the Group Policy Editor and apply the updated policy using: gpupdate /force.
3Restart the KDC Service on the DCs
On domain controllers, restart the KDC (Key Distribution Center) service. It allows the configuration of new encryption types and the service runs smoothly.
- Step 1.On the Domain Controller (DC), open a Command Prompt or PowerShell with Administrator privileges.
- Step 2.Restart the KDC service by running the following commands:
Stop the service: net stop kdcStart the service: net start kdc
- Step 3.You can also use services.msc to stop and restart the KDC service manually.
- Step 4.Open the Run dialog, type services.msc, and press Enter.
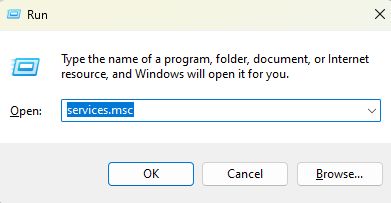
- Step 5.Scroll down to Kerberos Key Distribution Center, right-click it, and select Restart.
- Step 6.All domain controllers should restart if you have multiple DCs.
- Step 7.Close the Group Policy Editor and apply the updated policy using: gpupdate /force.
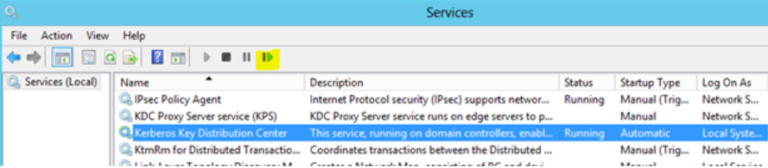
4Review Event Logs
You should check the Event Viewer logs for more detailed error messages related to Kerberos authentication:
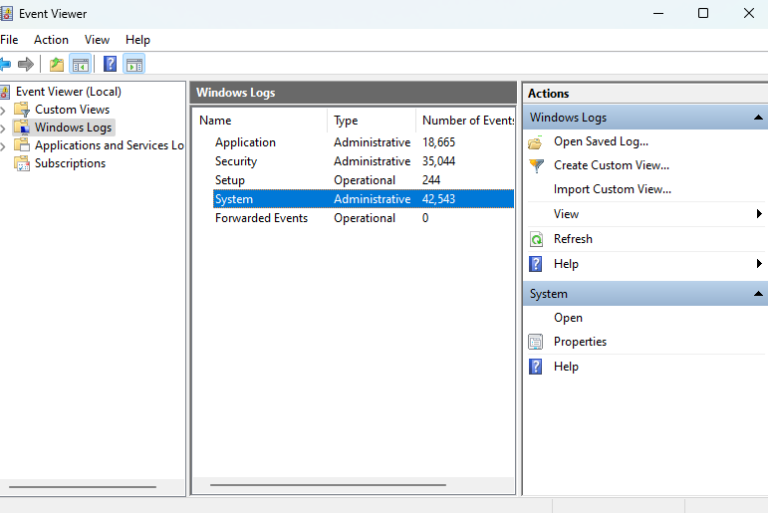
- Step 1.Go to Event Viewer> Windows Logs > System.
- Step 2.Look for Kerberos-related errors (event IDs like 14, 16, etc.) to get more information about why the encryption type is being rejected.
5Reboot Your Remote PC
You can reboot the remote PC so that any Kerberos tickets or security policies are refreshed with the new encryption settings.
- Step 1.Open a remote session to the PC or use a remote management tool.
- Step 2.In the command prompt, type: shutdown /r /t 0
- Step 3.Allow the system to reboot. Once it’s up, the PC will attempt to request new tickets and use the updated Kerberos encryption settings.
Bonus Tip: Use Free Remote Desktop Software for Windows
A reliable and error-free solution for Windows RDP support is AirDroid Remote Support. It’s designed to offer quick remote assistance, especially for Windows users, without any connection errors.
You can use it on various platforms, including Windows, Android, and iOS. It provides tools like remote control, screen sharing, voice chat, messaging, file transfer, and AR camera for troubleshooting physical equipment.
Security is ensured with AES-256 encryption, TLS 1.2, and two-factor authentication. Designed for scalability, it reduces downtime, enhances customer support, and facilitates secure remote work access.
Conclusion
KDC encryption and authentication error require compatibility between the encryption types supported by both the client and the key distribution center.
You can resolve it by updating the service account properties in Active Directory to enable AES encryption, configuring group policies to allow supported encryption types, reviewing event logs, and running the latest patches.
By following our fixes, you can prevent encryption mismatches and get secure Kerberos authentication across your system.





Leave a Reply.