How to See Who Is Logged into a Remote Computer? [2025]
Need to know who's accessing a remote computer? Worried about someone getting into your account without permission?
This article explores various methods about how to see who is logged into a remote computer. By implementing these techniques, you can maintain control over remote access and ensure the security of your network.
Ways to See Who Is Logged into a Remote Computer in Windows
Here's a comprehensive toolbox of methods to see who is remotely logged into a computer:
Method 1: Use Command Prompt or PowerShell
To see who is logged into a remote computer, you can use the "Command Prompt" or "PowerShell" tools.
Step 1: Open the "Run" box by pressing the "Windows + R" keys. Type "cmd" or "PowerShell" and press "Enter."
Step 2: The Command Prompt / PowerShell window will appear. Enter one of the commands below and press "Enter," replacing RemoteComputerName with the name of your remote computer.
quser /server:RemoteComputerName
query user /server:RemoteComputerName
Query information from multiple computers:
quser /server:computer1 & quser /server:computer2 & quser /server:computer3
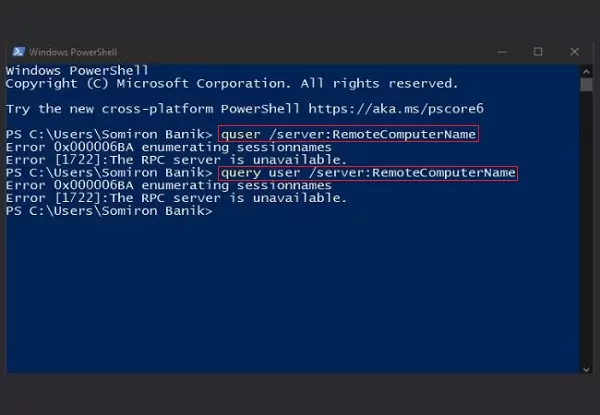
Step 3: Once you execute the command, the terminal will show you the name of the user who is currently using the remote computer.
You can also use the Get-CimInstance cmdlet in PowerShell to check if someone is using a computer on the network (Equivalent to Get-WmiObject. But starting in PowerShell 3.0, this cmdlet has been superseded by Get-CimInstance.):
Get-CimInstance -ClassName Win32_ComputerSystem -ComputerName $computername | Select -ExpandProperty username
Method 2: Use Windows Sysinternals Tool
The Sysinternals Suite is a set of tools used for troubleshooting. To manually install the Sysinternals Suite on Windows 10, you can follow these steps:
Step 1: Download the Sysinternals Suite from the official Microsoft Sysinternals Suite page.
Step 2: Once downloaded, extract the contents of the zip file to a folder of your choice on your Windows 10 system.
Step 3: Install using PowerShell (If you prefer to use PowerShell, you can install the Sysinternals Suite with the following command.)
winget install sysinternals --accept-package-agreements
Step 4: Follow the instructions and wait for a few minutes. The Sysinternals Suite will be successfully installed on your Windows computer.
If you have this suite installed on your computer, you can use the "PsLoggedOn" command [ PsLoggedOn \\RemoteComputerName ] through PowerShell or Command Prompt. Here's how:
Step 1: Launch "Command Prompt" or "PowerShell."
Step 2: Once the screen appears, paste the following command. Instead of RemoteComputerName, enter the actual name of the remote system.
PsLoggedOn \\RemoteComputerName
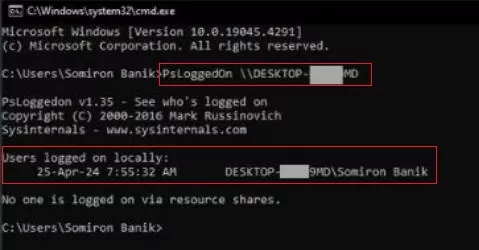
Step 3: The names of the logged-in users on the remote system will now be displayed.
Method 3: Use NBTSTAT Command
To see who is logged into a remote computer using the NBTSTAT command, you can follow these steps:
Step 1: Open the Command Prompt by pressing Windows + R, typing "cmd," and pressing "Enter."
Step 2: Type the following command and replace RemoteComputerName with the NetBIOS name of the remote computer you want to check:
nbtstat -a RemoteComputerName
nbtstat -A IP Address (If you only know the IP address)
Step 3: Press "Enter." The command will display the NetBIOS name table of the remote computer, which includes the names of logged-in users.
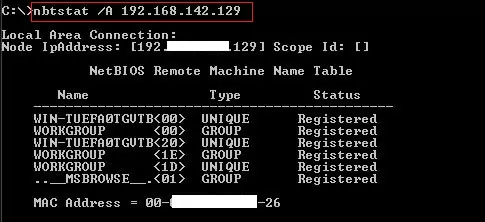
However, this method has limitations for identifying active users specifically for remote access. Here's why:
NBTSTAT primarily focuses on NetBIOS names, a legacy name resolution protocol that predates Active Directory and may not always reflect current usernames.
It only shows usernames for shared resources on the remote machine. If a user is logged in but hasn't accessed any shared resources, NBTSTAT won't pick them up.
Therefore, while NBTSTAT can provide some information about network devices, it shouldn't be solely relied upon to identify active remote users. Consider it as a supplementary tool along with other methods mentioned in this article.
Method 4: Use Event Viewer
Event Viewer offers a window into system security events, providing valuable legal data for auditing purposes. To identify successful login attempts, follow these steps:
Step 1: Open Event Viewer (search for it in the Start menu or taskbar search).
Step 2: Then, navigate through the tree structure on the left panel to Windows Logs > Security.
Step 3: Next, look for events with Event ID 4624. This specific event message indicates "An account was successfully logged on."
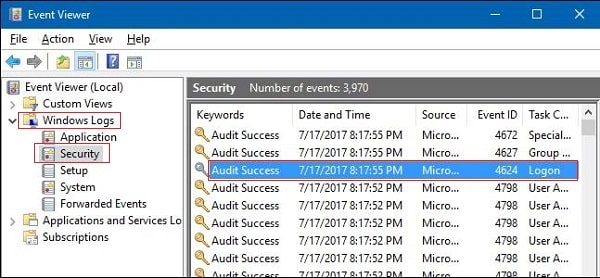
By reviewing the details of these events, you can collect valuable information about the user who logged in, including their username, domain (if applicable), and the workstation used to access the remote machine.
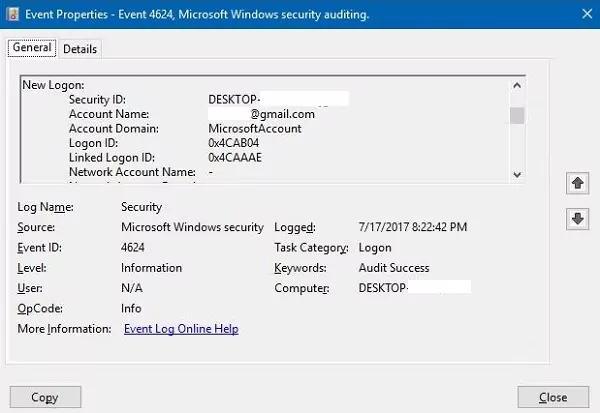
This information can be crucial for identifying unauthorized access or investigating suspicious activity. However, it is worth noting that this function is avaibale only if you have admin right to the windows computer or windows server.
In addition, if you do not enable logon auditing, Windows will not log information such as these logon events and usernames to the security log. To enable logon auditing, please view the following steps:
Step 1: Type "gpedit.msc" in the start menu or search box to open the Local Group Policy Editor.
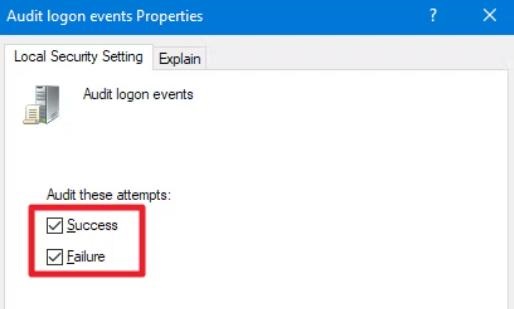
Step 2: In the left pane, go to "Local Computer Policy" > "Computer Configuration" > "Windows Settings" > "Security Settings" > "Local Policies" > "Audit Policy. " In the right pane, double-click to open the "Audit logon events" setting.
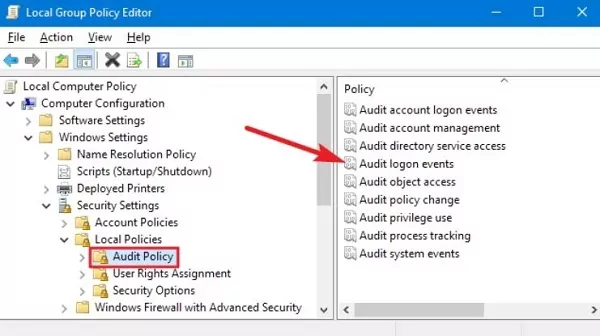
Step 3: Open the Properties window and check the "Success" and "Failure" options to enable Windows to record successful or failed login attempts. Then click the "OK" button.
Method 5: Use Task Manager
While Task Manager might not always provide a clear distinction between local and remote users, it can be a useful tool for quick checks on a local machine that also supports remote access functionality. Here's how to use it:
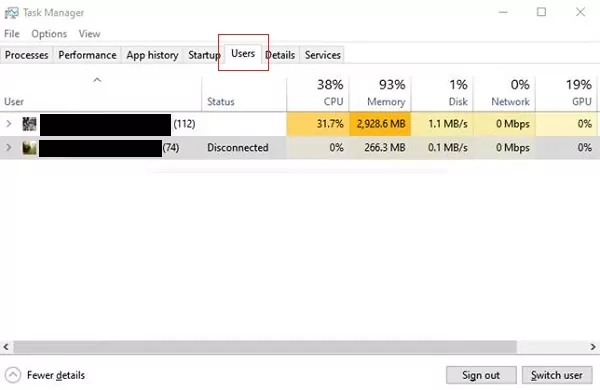
Step 1: Firstly, right-click on the taskbar and select "Task Manager." Or you can use the Ctrl + Shift + Esc key combination to open Task Manager.
Step 2: After that, look for a dedicated "Users" tab (availability depends on the Windows version) and then click on the "Users" tab. If present, this tab displays a list of users currently logged in locally, including those logged in remotely to the same machine.
Method 6: Use Remote Desktop Services Manager
For systems configured as Remote Desktop Session Hosts (RDSH) in Windows Server, use the Remote Desktop Services Manager tool to manage and monitor remote desktop sessions.
To open "Remote Desktop Services Manager" through Microsoft Management Console, follow these steps:
Step 1: Open the Run window, type "mmc," and press "Enter." Next, a new pop (regarding the Microsoft Management Console) will come, and click on the "Yes" option.
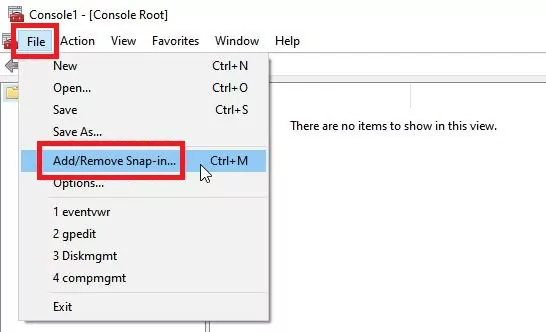
Step 2: Go to the File menu, and select "Add/Remove Snap-in."
Step 3: Under "Available snap-ins," choose "Remote Desktop Services Manager," then click "Add."
Step 4: In the "Select Computer" dialog box, decide if you want to connect to the local computer or another one. If selecting "Another Computer," either enter the computer name or use "Browse" to find it. Click "OK."
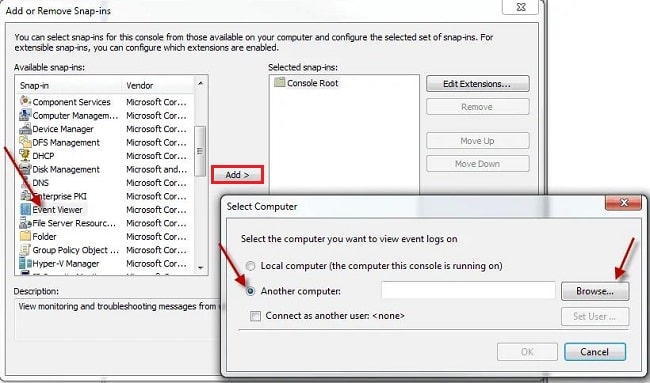
Step 5: In the "Add or Remove Snap-ins" dialog box, click "OK."
Therefore, you can easily use this command to see who is logged into a remote computer.
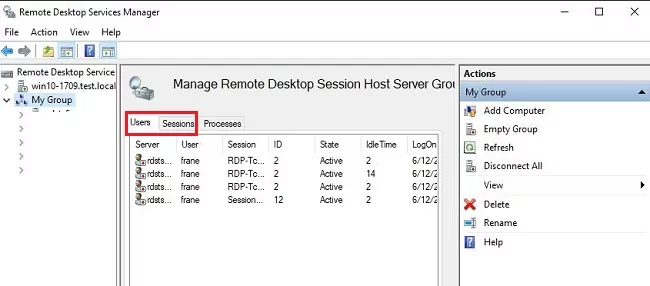
After entering into the "Remote Desktop Services Manager" interface, simply click on the "Users" tab to see all details about the users.
In the same way, you can also see all the active remote desktop sessions including usernames, session IDs, connection details, etc by clicking on the "Sessions" tab.
Important Considerations:
- Not all methods work universally. The available options depend on the operating system and remote access configuration of both the local and remote machines.
- Certain methods, like PsLoggedOn, require administrative privileges on the remote machine.
- While these methods reveal currently logged-in users, they don't necessarily indicate active usage. Consider session duration or activity logs for a more complete picture.
How to Check Remote Login Users on Linux
Are you wondering who might have logged into your remote Linux system? There are 2 simple ways to monitor and see the remote log-in on Linux PCs – through log files and command line utilities Take a look!
Method 1. Via Log file
Linux maintains the all the login activities including user logins in the log files. Users can examine these log files to analyze both successful and failed login attempts. Here are the two common log files for various Linux distributions:
For Debian/Ubuntu: /var/log/auth.log
For RHEL/CentOS/Fedora: /var/log/secure
To check entries related to SSH logins in these log files:
- Step 1: Open the terminal.
- Step 2: Use “grep” with the above command to filter the SSH (remote) login attempts.
- Step 3: To view active logins, check the entries like "Accepted password for [user] from [IP]."
Method 2. Using Command Line
Besides log files, you can also use commands to view the logged-in users (including SSH entries) and their activities directly. Some useful commands include:
Who: Shows the list of currently logged-in users.
W: Displays the detailed activities of logged-in users and their active processes including user’s login time, idle time, and active commands.
Last: Shows the list of last logins of users, extracting data from the /var/log/wtmp file to display the username, terminal, IP address, and login time.
lastlog: Shows the most recent login.
ss -tnp | grep sshd: Shows active SSH connections
Bonus Tip: To check the log-in sessions in real-time, use the watch command (like watch -n 1 'who').
Thus, you can easily see the logged-in history of Linux systems through log files and command files, ensuring the security of your system and files.
Tips: Bolstering Your Remote Access Defenses
Maintaining control over remote access goes beyond identifying users. Now, consider the following additional security measures. Let's get started!
Enforce Strong Passwords
Implement complex passwords for all remote access accounts and enforce regular password changes. Don't use passwords that are easy to guess or weak.
Enable Multi-Factor Authentication (MFA)
Add an extra layer of security with MFA, requiring a secondary verification method like a code from your phone or security token. This significantly increases the difficulty for unauthorized users to gain access, even if they manage to steal a password.
Limit Remote Access Users
Restrict remote access permissions to authorized personnel who genuinely require it for their work. Avoid granting broad access privileges unless absolutely necessary. The principle of least privilege dictates that users should only have the access level required to perform their designated tasks.
Utilize VPNs
Consider using a virtual private network (VPN) to create a secure tunnel for remote access, encrypting data transmission. VPNs add an extra layer of security by ensuring that data travels through an encrypted channel, even over public networks.
Monitor Login Attempts
Implement tools to monitor login attempts, allowing you to detect and potentially block suspicious activity. These tools can raise red flags for unusual login attempts, such as attempts from unexpected locations or at odd hours. By monitoring these attempts, you can take proactive measures to investigate and potentially block unauthorized access.
Through combining these mentioned methods with robust security practices, you can ensure that only authorized users gain access to your remote computers, safeguarding your valuable information and systems.
Bonus Tip: A One-in-All Remote Desktop Solution for Personal and Enterprise Use
If you want a complete remote desktop solution for your small business or personal use, try AirDroid Remote Support. Unlike traditional protocols (RDP, VNC, SSH), AirDroid offers a suite of advanced features with a friendly interface and cross-platform compatibility.
It is ideal for IT teams, allowing them to manage their complete IT infrastructure from a single interface. Besides, companies can rely on AirDroid to provide real-time customer service and remote assistance.
Some of its key features include:
- Remote Access: Access and control remote devices from anywhere with a single click. It offers both attended and unattended remote access.
- Device Management: Supports lightweight management to perform functions like running scripts, troubleshooting multiple devices, deploying software, executing commands without direct log in, role assigning, and more.
- Log Recording: Provides comprehensive logs of support session with timestamps, user IDs, and actions taken. It also allows exporting logs for auditing or reviews.
- Batch Capabilities: Multi-device screen sharing, batch file transfer, Android/iOS AR camera.
Conclusion
This article outlines various simple ways to view who is logged into a remote computer. Now, you can easily identify the remote users and undertake actions to guarantee the security of your network. It’s best to take implement full-proof security arrangements in advance to avoid facing any unauthorized access.
Moreover, we also talked about how AirDroid Remote Support can transform the way businesses provide remote assistance to their clients. Get its trial version to streamline all your IT infrastructure from a single platform.
Thank you!





Leave a Reply.