[2024 Updated] What Are GPOs in Windows?
Q: What Are GPOs in Windows?
Group Policy Object (GPO) is a set of commands & task execution templates implemented on bulk devices to ensure uniformity and consistency in a work environment.
Microsoft has facilitated business administrators with Group Policy to manage and enforce security configurations for many official devices. It provides firm control over applications, OS, and network settings for managed devices to provide a restricted and controlled working environment.
Group Policy Object (GPO) is accessed through the Microsoft Management Console Group Policy Editor.
- 1 : Usages - What Are GPOs Used for?
- 2 : Compare Different Types of GPOs
- 3 : Computer Configuration vs. User Configuration
- 4 : Pros and Cons of Group Policy Objects
- 5 : How to Create/Edit/Delete GPOs(with Example)
- 6 : How to See What GPOs Are Applied?
- 7 : What Is the Relationship Between Active Directory (AD) and GPOs?
1Usages - What Are GPOs Used for?
Enforce Security and Behavior Settings
GPO enables administrators to enforce consistent security settings and behavior within Windows server environments.
For example, in an organizational unit of employees in a company's finance department, a group policy can be applied to re-authenticate after a screensaver activates. It will ensure that the computers that are not being used are locked and only accessed by authorized personnel.
Through these policies, the risk of security breaches can be decreased. It also makes the process of updating or modifying policies easy through the approach of centralized management.
Deploy Internal Wireless Network Profile
A Group Policy can be deployed for seamless and secure Wi-Fi connectivity across all company devices.
This method automates the configuration settings for the wireless network, reducing the need for manual setup and ensuring that all devices have consistent and secure access to the corporate network.
WSUS/Update Settings
Using Windows Server Update Services (WSUS) to manage Windows updates lets administrators control the deployment of updates, ensuring that all systems are secure with the latest fixes.
It also reduces the risk of interruptions from automatic updates by enabling testing and scheduled deployments.
Firewall Policies
GPOs help manage and enforce firewall policies in a business environment. Firewall policies regulate incoming and outgoing traffic with a set of predefined rules and play an important role in safeguarding the security of the network.
These rules determine how the traffic will flow by allowing or denying connections, ensuring that the system is protected from unauthorized access, data breaches, and malicious attacks.
Managing access and restrictions
GPOs allow administrators to prevent end-users from accessing system settings, which can lead to high-security risks.
The command prompt allows running various commands that can lead to changes in system settings and access to restricted files.
Using GPOS, admins can prevent access to the command prompt and control panel to ensure end-users cannot make changes in the system without the admin’s permission.
2Compare Different Types of GPOs
After profoundly understanding what are GPOs, let’s discuss their types:
| Types | Local GPOs | Non-Local GPOs | Starter GPOs |
|---|---|---|---|
| Scope | For single Windows computer or user. | For one or more users or computers. | Templates for Group Policy Settings. |
| Configuration Position | Local GPOs exist by-default on Windows computers and accessed through Group Policy Editor. | Group Policy Management Console. | Group Policy Management Console. |
| Application | Applied to local computer, but are overridden by non-local GPOs. | Applied to Active Directory Objects and override the local GPOs. | Provide templates as baselines which help to create new GPOs. |
| Useful for | Setting policies on a single computer in a specific domain. | Providing centralized management for domain environments. | Creating and having pre-configured group of settings, which could help in creating future policies. |
3Computer Configuration vs. User Configuration
In Windows, group policy objects (GPOs) are classified into two main categories: computer configuration and user configuration.
These categories allow administrators to customize settings according to their system—or user-level requirements. You can also check the device to see what GPOs are applied.
Scope
- Computer Configuration: It affects all the users who log on to the computer as the policies are applieds.
- User Configuration: The policies are applied to the user profile, so they affect the user environment on every computer they log into.
Impact of policies
- Computer Configuration: Policies such as installing security software significantly impact settings that should remain consistent across all users' computers.
- User Configuration: Policies that are applied to personalize a user's environment, such as specific software restrictions for users and desktop backgrounds.
Policy management
- Computer Configuration: Mainly focuses on system performance and security by implementing machine-level policies and settings.
- User Configuration: They are mainly concerned with ensuring that the system's behavior and access remain consistent for users and provide a better user experience.
4Pros and Cons of Group Policy Objects
Pros
- Centralized Management
GPOs provide a centralized platform to store official files under high security and allow pre-configured settings and configurations for new users in the organization, saving time and resources for manual installation and settings. - Efficient password policy setup
GPOs allow administrators to enforce password input policies for official devices. Admins can set standards for password length, reuse password options, and the addition of upper- and lower-case letters, numbers, and symbols. - Enhanced Security
GPO offers various security policy settings for enhanced security. These include strong authentication, account lockout settings, software and app restrictions, and preventing access to device settings. - Automation for administrators
GPOs facilitate administrators by automating various routine tasks that can take a lot of time if done manually. Patch management and auto-updates streamline device performance.
Cons
- Complexity
Efficient GPO management requires a clear understanding of AD and Group Policy; otherwise, it can lead to security vulnerabilities. - Dependency on Active Directory
Most organizations do not have AD infrastructure, so they cannot leverage GPOs, as they are dependent on AD. - Slow Processing
GPOs have a sequential implementation of actions. It means it will take a longer time to configure all GPOs if you need to implement multiple GPOs - Lack of Search option
GPO does not contain any option like 'Search' or 'Filter' to sort out specific settings and manage them instantly. - Recent actions updates
GPO cannot display the latest settings or changes made in it. So, it becomes problematic if a wrong action is triggered unintentionally and will be hard to find out.
5How to Create/Edit/Delete GPOs(with Example)
Managing Group Policy Objects is essential for IT administrators. Follow these steps to create, edit, and delete them efficiently.
Creating a New GPO for displaying Interactive Logon
- Step 1: Press the Windows + R button to open Run command and type ‘gpmc.msc’ to open Group Policy Editor.
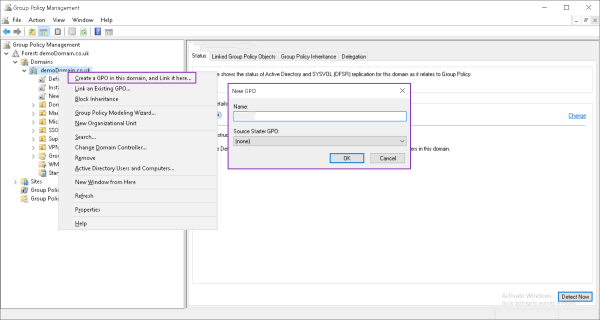
- Step 2: Select the relevant domain and choose ‘Group Policy Objects’ tab. Right-click on the container and select ‘Create and Link a GPO Here’ to create a new GPO. Name it relevant to the policy you will add and click ‘OK.’
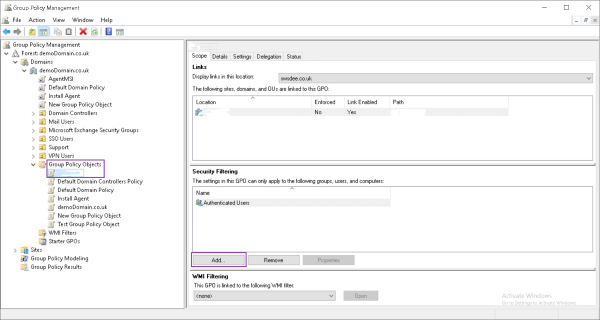
- Step 3: When the GPO is created, you need to specify the devices to which it will apply. Expand the Domain, select the new GPO, and click 'add'.
Editing a GPO for managing Windows update settings
- Step 1: Right-click on the GPO you want to edit and select the ‘Edit’ option from the menu.
- Step 2: Choose certain settings options, customize them, and save to apply changes. For example, you can manage WSUS settings from the computer configuration option. Choose the policies option and select ‘Administrative Templates.’ Choose Windows components and then Windows Updates.
- Step 3: Choose the ‘Configure Automatic Updates’ option, customize various options as required, and press ‘OK’ to apply them.
Deleting A GPO
- Step 1: Right-click on the GPO you want to delete from the OU or the domain.
- Step 2: Select the ‘Delete’ option and confirm the deletion of a specific GPO.
- Step 3: To completely delete the GPO, select it from under the ‘Group Policy Objects’ container by right-clicking on it and selecting ‘Delete.’
6How to See What GPOs Are Applied?
Using the Group Policy Management Console, you can access the ‘Group Policy Results’ feature and check out what GPOs are applied to the computer or the user. Another way is to check through the command prompt. Here are the detailed steps:
By using Group Policy Management Console (GPMC)
- Step 1: Press the Windows + R key to open the run command, type ‘gpmc.msc’ to open the group policy, and press ‘Enter’.
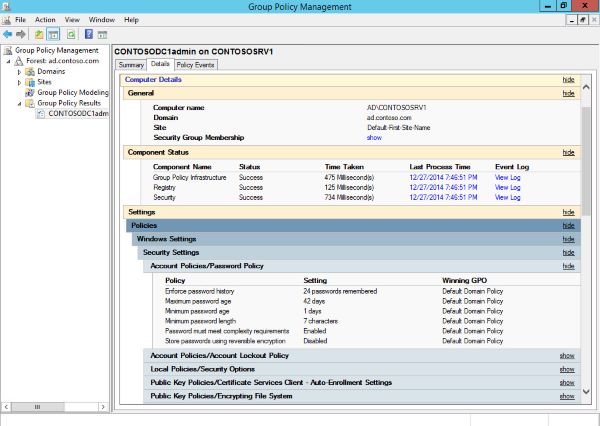
- Step 2: To generate the reports, right-click on the target domain and select ‘Group Policy Results’.
- Step 3: Choose a computer or user for whom you want to view the GPOs. Follow the instructions to complete the process, displaying all the information related to applied GPOs and settings.
By using Command Prompt
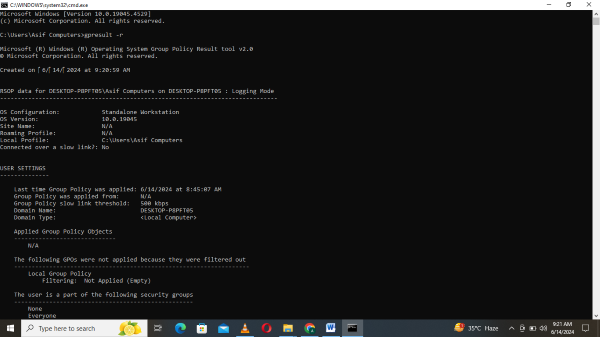
- Step 1: Open the run program using the Windows menu bar and type ‘cmd’ in the search bar. Press enter to open the command prompt.
- Step 2: Type ‘gpresult / scope computer or user/ v’ in the command prompt and press enter.
7What Is the Relationship Between Active Directory (AD) and GPOs?
Active Directory and GPO are active components of the Microsoft Server environment, collaborating to develop an effective and secure working environment.
An active directory is a database that stores information about various network resources, including user data and computers.
It offers a centralized platform to manage network security for all devices in a specific domain. The primary functions of AD include authentication and authorization of devices that try to enter the network.
AD has another concept known as Group Policy Objects (GPOs), which serve as ways of achieving certain goals and policies regarding these resources, including security settings, program installation, and even desktop settings. GPOs are contained in AD and can be linked to multiple sites, domains, and OUs.
8Conclusion
Let’s have a short conclusion about what are GPOs. Group Policy Object (GPO) is a feature in Active Directory that enables enterprises to manage and secure networks to ensure compliance with regulations and a smooth working environment.
They help administrators enforce security policies for access management, password setting, and software installation on official devices.
GPOs have three common types: local GPOs, non-local GPOs, and starter GPOs. Users can choose any of them based on their specific needs and scope.
GPOs provide significant user benefits, including centralized management, enhanced security, and access controls.
Admins can easily edit, create, or delete GPOs using the Group Policy Management Console and try various tools to check which GPOs are implemented on their devices.









Leave a Reply.