A Comprehensive Guide to Microsoft Endpoint Manager
What is Microsoft Endpoint Manager (MEM)?
- Microsoft Endpoint Manager is a broad suite for device management with five major services including Microsoft Intune, co-management, and Microsoft Defender for Endpoint.
- Combining these services has provided enterprises more comfort and abilities to control, organize, and secure official devices through a centralized management system.
Let’s discuss these services in detail and how they can help streamline and secure official devices.
1Key Services Provided by MEM
| Name | Definition | Features included |
|---|---|---|
| Microsoft Intune | A cloud-based end-point management solution facilitating MDM and MAM for large enterprises to ensure security, compliance and controlled working environment. | User and device management, conditional access, compliance policies, app management, and security configuration. |
| Configuration Manager | Formerly known as System Center Configuration Manager (SCCM) is a management tool based on corporate and on-premises infrastructure facilitating system management activities like reducing manual work, increased productivity, and efficiency. | Patch management, remote control, software distribution, OS deployment, update management, hardware and software inventory management. |
| Co-Management | SCCM (System Center Configuration Manager) and Intune when collectively used to manage devices is called co-management. | Remote control, remote wipe, factory reset, modern provisioning, conditional access, compliance policy management, and security. |
| Endpoint Analytics | A tool that provides deep-insights of organizational working procedure and the quality of user experience, enabling IT teams to improve productivity and reduce costs using pro-active approach to handle the device configuration changes that can affect user experience. | Custom device scopes, Anomalies to detect device health, enhanced device timeline, and device query to get data access about configuration and state of devices. |
| Microsoft Defender for Endpoint | A comprehensive solution for detecting, preventing, protecting, and automating the investigation and response to threats on endpoints. | Cloud security analytics, threat intelligence, flexible enterprise controls, auto-deployed deception, and network detection and response. |
2Highlights of Different Services & What They Can Help
Now you understand what is Endpoint Manager. MEM offers multiple services, each of which serves a different purpose. So, enterprises must analyze their specific needs, infrastructure, and goals while choosing MEM services.
Secondly, a clear understanding of the highlights of every tool is also necessary to choose the best option.
1Microsoft Intune
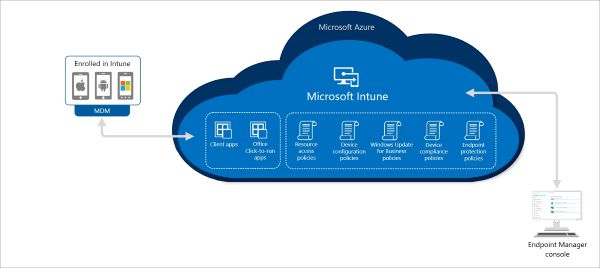
Microsoft Intune is a pro-active tool that works based in a modern way facilitating multiple device management based on SAAS apps infrastructure.
It promotes automation of tasks and provides flexibility for employees to use any device to remotely access the applications and corporate data to perform their duties.
It provides MDM services like seamless device enrollment, configuration and deployment of certificates, apps and security tools like deploying VPNs, applications, and setting passwords on devices.
It can integrate with other Microsoft services like Windows Autopilot and Microsoft Defender for Endpoint.
(Microsoft 365 Premium includes Intune and no separate subscription is required with it.)
(Image credit: Highstream)
Highlight: It offers Cloud-based management, MDM and MAM services, and integration with multiple Microsoft services.
2Configuration Manager
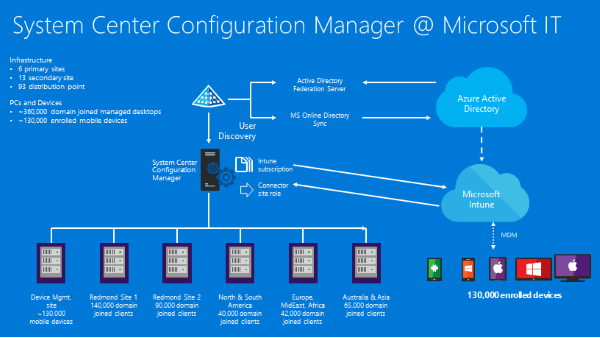
It works in a traditional way facilitating single device management and allows manual actions to manage on-premises devices.
Configuration manager has a reactive approach. It utilizes Microsoft SQl Server as a distributed change management database and SQL Server Reporting Services to generate reports for better tracking of activities.
Integration with Delivery Optimization, Background Intelligent Transfer Service, and BranchCache helps to manage content on networks and between the devices.
Configuration Manager also integrates with some other services like Microsoft Azure, certificate services, DNS, Group Policy, Windows Deployment Services, Remote desktop and remote assistance, and WSUS to extend management services.
(Image credit: Microsoft)
Highlight: Being the part of Intune, it allows on-premises management, streamlined deployment of different OS devices, compliance settings, and endpoint protection.
3Co-management
Co-management is the collective utilization of Intune and configuration manager features. If we install SSCM client on a device end enroll the same device to Intune, it will give both benefits.
However, it is quite difficult to manage two authorities on a single device. Co-management helps to maintain a balance between both of them to ensure productivity and avoid conflicts.
Requirements to Enable Co-Management
The device must contain Windows 10 version 1709 or newer and joined to Azure AD and on-premises AD DA.
User must have Intune license for using co-management.
For licensing user needs Microsoft Entra ID P1 or P2. Moreover, the Enterprise Mobility + Security (EMS) subscription includes both Entra P1 or P2 and Intune.
Methods
Existing Clients: With Windows 10 or later devices already having SSCM installed, we simply setup hybrid Azure AD and enroll devices to Intune.
New internet-based clients: With Windows 10 or later devices having Azure AD and enrolled to Intune, we only need to install SSCM.
Highlight: Co-management offers consistent user-experience with more flexibility to manage workload and security for devices by leveraging cloud-based security measures.
4Endpoint analytics
End-users experience long boots and other issues due to legacy hardware, un-optimized software configurations, and impacts of configuration changes.
These issues are unable to diagnose and rectify due to availability of limited sources to visualize the user-experience. As a result businesses have to bear costs and time is wasted. End-points Analytics is a useful tool to analyze such issues because it provides deep-insights of user experience, enabling IT teams to identify and troubleshoot issues.
For data collection, Intune Service Aministrator role is required and it normally requires 48 hours to view the advanced analytics after you buy the license.
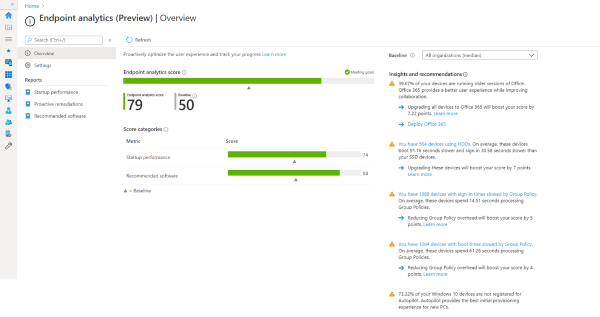
Highlight: It helps to gain insights into health and performance of devices, understand and improve user-experience, and track the trends over time to prevent potential issues.
5Microsoft Defender for Endpoint
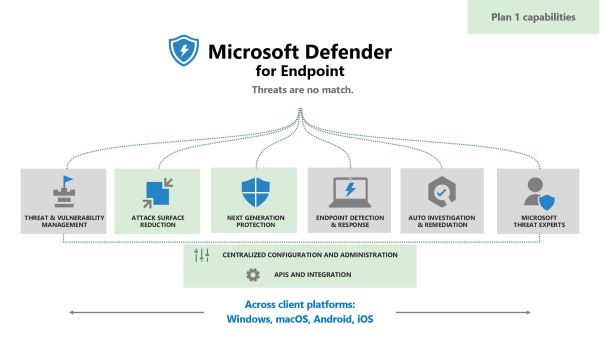
It's a core part of Microsoft 365 Defender, which combines and orchestrates the capabilities of Microsoft Defender for Endpoint, Microsoft Defender for Office 365, Microsoft Defender for Identity, and Microsoft Cloud App Security.
Microsoft Defender has seven pillars which completely define its role and functions. These pillars are threat and vulnerability management, attack surface reduction, next generation anti-virus, endpoint detection and response, auto-investigation and remediation, Microsoft threat experts, management and APIs.
It directly integrates with Microsoft Defender for Cloud, Microsoft Sentinel, Microsoft Defender for Cloud Apps, Microsoft Defender for Office, Skype for Business, and Intune.
(Image credit: Microsoft)
Highlight: It ensures advanced threat detection and prevention against them by automating routine tasks to reduce burden on IT staff. For enhanced security, it integrates with Microsoft.
3Getting Started With Microsoft Endpoint Manager
- Buy License
Before choosing MEM services, you need to know the licensing requirements and each service has a unique requirement. (However, now Microsoft Configuration Manager has become the part of Intune. So, getting Intune license will enable you to access Configuration Manager features). - Get Familiar with Microsoft Intune Architecture
Carefully analyze the benefits and requirements of every service MEM provides and then choose the best one that suits your business needs. For example, some companies wish to provide a better user experience. They should choose Endpoint Analytics as it will provide them information about how their organization is working and what quality of user experience is provided, so they can improve operational efficiency. - Deployment & Enrollment
Start by deploying MEM and enroll multiple devices as it supports various OS like Android, iOS and Windows. MEM offers different device enrollment methods like automatic enrollment, Windows auto-pilot deployment program, and bulk enrollment. You can choose any type based on the methods your devices support. - Device Configuration
With MEM, configure the devices to align with organizational needs. It includes setting up device profiles, managing updates for OS and apps, and customizing policies and settings for all managed devices to ensure uniformity and optimal performance with high security. - Enforce Policies
Create security policies and enforce them on all managed devices from a centralized dashboard to meet all business endpoints. Policy management includes setting strong password complexities, remote actions like remote wipe and factory reset, device encryption. - Data Confidentiality
Utilize data protection measures like access controls, remote monitoring and control tools, data encryption to prevent unauthorized access and safeguard critical information saved on devices which can otherwise cause financial and reputational loss. - App Management
Allow all devices with different OS to access and download apps from valid sources like Microsoft Store. Manage apps on all devices by remotely installing, deleting, or updating apps on them. Ensure that only known apps are allowed to install on managed devices to ensure compliance.
4How Your Business Can Benefit From Microsoft Endpoint Manager?
IT teams have faced new challenges in managing devices as employees collaborate with the team and higher management to ensure consistent and productive work while working from home or other workstations. Here are some benefits Windows Endpoint Manager has provided to the IT managers for efficient device management:
- Improved End-User Experience and Productivity
Microsoft Endpoint Manager offers a hybrid working environment to its users, enabling employees work from office or home without communication barriers.
It allows businesses to provide a friendly, secure, and flexible working environment so they can dedicate work and improve productivity.
Businesses can also achieve high productivity by initiating the rollouts for app installation and updates, which results in better device performance. - Enhanced Security
MEM provides a centralized platform to manage all the security measures for robust security. It helps to monitor, update, and configure devices on the network when required.
It is efficient at access management by customizing the policies for personal devices to limit device usage and prevent access to certain apps and features. - Enforcement of compliance policies
Enterprises can easily manage and enforce policies for devices using MEM. It allows automation and enforcement of guidelines for deploying apps, their security, and the configuration of devices with conditional access to device features and apps.
These policies help enterprises ensure compliance with industry-specific standards to avoid penalties, fines, and other legal issues.









Leave a Reply.