- Network compliance management.
- Bulk-configure corporate devices to connect to the office Wi-Fi automatically.
- Configure the use of VPN according to the needs of the company.
- Disable network sharing to reduce the risk of unauthorized access.
Comparing Wi-Fi Security Types: Which is Best and How to Change
In most cases, the strongest compatible security protocol will be WPA2 or even WPA3. Upgrading your WiFi to the latest possible security protocol prevents unauthorized access along with the hacks, data breaches, and heavy data hoarding that can come with it.
Changing WiFi security type is easy. Users need to use an internet-connected device to access their router's admin console, navigate to the security panel, and choose the most robust security protocol supported by their router and devices.
1What do the different WiFi security types mean?
There are four different WiFi security types, each with different features.
Wired Equivalent Privacy
Introduced in 1997, WEP uses the RC4 stream cipher for encryption and static keys that must be manually configured for key management. Because of its numerous security vulnerabilities, WEP is prone to unauthorized access. Bad actors can guess the static key to decrypt the encryption key and gain access to the user's data and content. As a result, WEP has largely been deprecated in favor of the stronger security protocols on this list.

WiFi Protected Access
WPA came six years after WEP to address security issues with its predecessor. Although still based on RC4, WPA uses temporal key integrity protocol (TKIP), which dynamically changes keys to enhance security. The WPA also used 256-bit keys, a significant improvement over WEP, which was limited to 64—and 128-bit keys. While stronger than WEP, WPA is still prone to unauthorized access, so it has been phased out, save for some legacy systems, in favor of WPA2.
WiFi Protected Access II (WPA2)
WPA2 succeeded WPA in 2004 as the standard for wireless security in personal and enterprise WiFi networks. When properly implemented, WAP2 is highly secure, relying on the advanced encryption standard (AES), which was originally developed by the US government and is so strong it would take billions of years to crack. WPA2 is also paired with the counter mode cipher block chaining message authentication code protocol, which improves upon WPA's key management.
WiFi Protected Access III (WPA3)
WPA3 came in 2003 and represents the highest level of cybersecurity: It makes WiFi networks highly resistant to brute force and other attacks. WPA3 is widely used in enterprise environments, especially in sensitive industries such as banking, healthcare, or education. WPA3 abandons the pre-shared key (PSK) encryption method in favor of simultaneous authentication of equals (SAE) for key exchange.
Multiple redundancies exist for security, such as key management, which prevents the compromise of session keys even if a long-term key is compromised. Finally, WP3 also introduces unique encryption to each connected device, preventing the entire network from being compromised, even if a single one is.
2How to change WiFi security type?
Most people are accustomed to interacting with their WiFi through the dropdown list on their laptop or mobile phone. As a result, they will often go to this area in an attempt to change their WiFi security type there.
In actuality, users must follow these steps.
What is the security type of my WiFi?
- Step 1.Access router's admin console
- Use a browser connected to the WiFi network for which you wish to change the WiFi security type. If you are unsure whether you are connected to the right network, check the nameplate on the bottom of your router or connect to it directly with an ethernet cable.
- Type in the address of your router's admin console. It is most often http://192.168.1.1 or http://10.0.0.1/, but the instructions packaged with your router may provide more detailed information on the exact address.
- Step 2.Enter your username and password
- Upon entering the correct address for the router's admin console, you will encounter a login screen—type in your username and password, often "admin" (note that this is case-sensitive).
- You may have to contact your internet service provider if it is not "admin" or you do not remember the custom password you set.
- After logging in, navigate to the router's security panel. The exact user journey to get there will vary from router to router, but in most cases, it will be under Wireless Settings, Wireless, or Settings.
- Step 3.Check your WiFi security type
- If you choose the correct option, you will see a screen with the following key details: the network name, its security type, version, encryption, your password, mode, channel width and its transmit power. This step is where you learn how to find security type of WiFi.
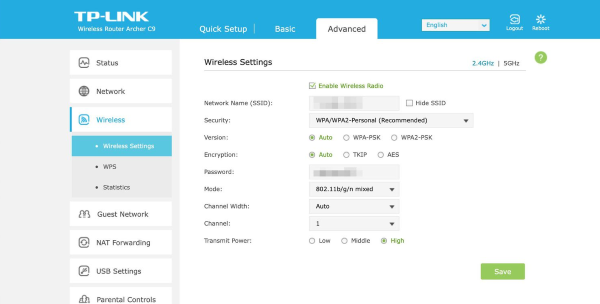
- Step 5.Change the Wi-Fi Security Type
- You should avoid Wired Equivalent Privacy (WEP) and WiFi Protected Access, the first generation of WPA that has mainly been phased out. While WPA3 offers the most robust cybersecurity protection, users cannot indiscriminately choose this option because it requires the latest hardware. Your router may not provide it, or your laptops, tablets, or mobile phones may not yet support it.
- At the minimum, people should choose WPA2-PSK. If this option is unavailable, you may need to update your firmware. You can find a detailed explanation of the different WiFi security types in the section below to choose the one that is best for your WiFi network.
- Step 6.Save changes
- Click save to put the changes into effect.
3What are the benefits of securing your WiFi network
Most of the literature about securing WiFi networks focuses on worst-case scenarios. While it is important to highlight what can go wrong, this type of storytelling does not always inspire people to take action. People will assume that these disasters will not happen to them.
Because of this reality, it is equally important to highlight the numerous benefits of securing a WiFi network.
Data security
Individuals and businesses that secure their WiFi networks ultimately secure their data. They can rest easy knowing that the chances of hackers stealing their data are slim to none.
Dealing with compromised personal or financial information is an enormous amount of work. Victims may need to cancel and reissue credit cards, change passwords, and monitor their online accounts for suspicious activity. These tasks are stressful and take time away from more important life matters.
Fast and reliable connectivity
As mentioned earlier, unauthorized internet access often leads to slower connectivity. If neighbors use your internet for data-intensive uses, your household may quickly hit its daily cap. Your internet service provider will thus throttle your speed to reduce bandwidth, affecting your legitimate use.
Individuals who secure their WiFi network will never have to deal with sudden, unexpected drops in internet speed. When they need to use the internet for work or school, they can always rely on a consistent and reliable connection.
Peace of mind
Whether they are against individuals or businesses, cyber-attacks are extremely stressful affairs. For example, many small business owners report suicidal thoughts in the wake of a ransomware attack that brings their operations to a halt. Even if the negative feelings may not always be as extreme as suicidal ideation, victims may feel depressed, anxious, scared, and other negative sentiments.
When people secure their WiFi networks, they do not have to worry about the havoc a cyber attack can create on their lives or business. They have peace of mind that they have taken necessary measures to protect their WiFi from unauthorized access and cyber-attacks.
Business continuity
Unauthorized WiFi access can lead to serious disruption for businesses. To prevent data breaches, businesses must strengthen their systems, investigate the incident, warn any third-party stakeholders if their data or assets have been compromised, and develop a detailed plan to prevent similar occurrences in the future.
Incident response drains resources. Businesses that secure their WiFi network in advance can spare themselves this exhausting rigamarole. Instead, they can maintain business continuity and focus on what matters most: growing their business.
4Who can gain access to unsecured WiFi?
People tend to overlook the security of their WiFi. They assume their WiFi is not important enough for people to exploit. The reality, however, is that every WiFi has a range of potential attackers.
- Unauthorized users - These can be complete strangers, such as people walking past your home or guests who need the internet but don't ask for your permission.
There may also be specific use cases for accessing your network. Some users may use your internet for data-intensive tasks, such as downloading, streaming, or gaming, rather than their own.
Children or teens in the area may use your WiFi to bypass the parental controls on their home network and access prohibited content.
While this type of unauthorized use may seem mostly harmless, it does affect the WiFi owner.
They may get their internet throttled by their internet service provider, resulting in lower speeds and even the possibility of additional fees. - Data thieves - Some data thieves will access WiFi to intercept personal information. They may try to obtain financial data, such as credit card information or credentials to bank accounts.
They will then use this information to make unauthorized withdrawals from your accounts.
Alternatively, they can steal general information about the user, which can then be resold on the darknet.
Although less common, WiFi has also been an attack vector for corporate espionage. Hackers will target the WiFi of a known employee to gather data about confidential trade secrets or other information that will benefit competitors. - Hackers — Some hackers may use a WiFi network to cause general mischief, such as locking out legitimate users with a new, unknowable password.
Others may leverage WiFi access for more severe crimes. For example, hackers could use the connectivity of a group of WiFi networks as part of a more significant cyber attack.
A ransomware operator could use WiFi as an attack vector to install ransomware on all the devices on the network.
This ransomware would lock people out of their devices or workstations and only restore access if a ransom is paid, most often in cryptocurrency, which is harder for authorities to trace.
5Strengthening your cybersecurity
Cybersecurity is a complex and ever-changing field. However, individuals and businesses must start with the basics before going to advanced cybersecurity measures, which involve choosing the right WiFi security type.
In general, users should avoid WEP and WAP security protocols in favor of WAP2 or WAP3, which are far more secure options. These latter-generation security protocols have stronger protections in terms of encryption and key management, so your WiFi network and devices remain secure.
Strengthening your WiFi security type will prevent all the bad actors, including unauthorized users, data thieves, and hackers, from victimizing you. There are numerous advantages to proactively choosing a best-in-class security type. Users secure their data, enjoy peace of mind that they are generally safe, and experience fast internet. Enterprises will also benefit from business continuity.
From the foundation of a strong WiFi security type, individuals and businesses can exercise best practices that protect their data, connectivity, and productivity.









Leave a Reply.