Ensuring Secure Network Connection at a Remote Site [Comprehensive Guide]
In today's digital age, when online connectivity and remote work are critical, setting up a safe network connection at a distant location is a bedrock of modern business infrastructure. It's vital to effortlessly and dependably link up and communicate with remote spots, whether for business, education, or other uses.
Are you anxious about ensuring your data stays safe as it travels across the web from one far-off location to another? Look no further! Together, we'll explore uncomplicated but essential techniques to secure network connection at a remote site.
- Why Set up a Secure Network Connection at a Remote Site
- How to Set up a Secure Network Connection at a Remote Site
- What Is Secure Network Connection Remote Site Protocol
- The Importance of Setting up a Secure Network Connection at a Remote Site
- Best Practices - Choosing More Secure Remote Access Software
Why Set up a Secure Network Connection at a Remote Site
Just picture a business that has branches spread across the globe. They have crucial data that needs to be transferred between these locations. However, sending it without protection is like mailing a postcard open for anyone to read. That's hardly secure!

So, they devise a way out — by establishing a secure network connection, they ensure that the information they share is shielded from prying eyes.
Establishing a secure connection aids in protecting our details from crafty cybercriminals. No matter if it's for giant corporations or just for us ordinary individuals, a secure network connection acts like a robust padlock for our virtual data, making sure it doesn't end up with undesired parties.
As more people are working remotely, setting up satellite offices, and collaborating globally, securing network connections on remote sites has turned into a complete and critical task. This intricate situation comes from the challenge of ensuring easy remote access without compromising the safety of sensitive information and the network's integrity.

How to Set up a Secure Network Connection at a Remote Site
Set Up Firewall
Think of a firewall as your digital security guard. It sits on the border between your network and the vast internet, carefully watching all the data that flows in and out. This vigilant guard controls and blocks any data that could harm your network. It's your first line of defense, keeping your digital world safe and secure.
Install Antivirus Software
Just as you would protect your body from harmful germs, antivirus software serves as a protective shield for your devices against damaging software or malware. It tirelessly scans for and eliminates threats to keep your systems in top shape.
Apply Encryption to Data
Imagine encryption as a secret language that only you and some chosen people can understand. It deliberately tangles up your information so that no matter who intercepts it, they won't be able to make any sense of it.

Get a Virtual Private Network (VPN)
A VPN is like a safe passage for your internet connection. It's a guardian that protects your online actions, keeping them private and secure even when using public networks. Picture it as having your private lane on a super busy public street.
Set Up Two-Factor Authentication (2FA)
Two-factor authentication gives you added protection by needing two distinct forms of identity validation. Imagine it's like needing a key and a password to get into a locked room - it certainly makes it much harder for people who aren't supposed to be there to get in.
Enable MAC Address Filtering
MAC Address Filtering is similar to having a VIP entrance, where only specific devices are allowed to connect to your network. It's like a digital bouncer, making sure only recognized gadgets have access, keeping any unexpected and uninvited ones at bay.
Create Strong Passwords
Think of a strong password like a sturdy front door lock — the harder it is for someone to break in, the safer you'll be. It is your first line of defense. Try mixing up letters, numbers, and symbols — that'll give it some extra strength.

Timely Monitoring and Recording
Keeping an eye on your network activity regularly is like being alert and checking your surroundings for safety. It helps you quickly notice and respond to anything unusual, protecting you from potential dangers.
Implement Network Segmentation
Breaking down your network into smaller, manageable bits is like having separate rooms in a house. It helps you streamline the flow of data and puts a leash on any possible threats, keeping them confined within one area.
Regular Update of Software and Operating Systems
Regular updates frequently come loaded with essential security fixes. It is like mending a hole in a fence; the stronger and more secure it is, the less chance it is for unwanted guests to slip on in.
Cultivate Safety Awareness among Employees
Educating everyone on the importance of security practices shapes a more vigilant team. It's like having every member of a neighborhood looking out for each other, creating a safer community.

What Is Secure Network Connection Remote Site Protocol
In general remote access and connection, a certain remote protocol is selected and some customized services are configured to enhance the stability of the connection. Below, we describe several common secure network connection remote site protocols.
Communication Protocols
Communication protocols are like translators helping different devices talk to each other over a network. They're really crucial for ensuring data moves seamlessly between various devices and systems. We even use different kinds of these protocols to set up secure connections when working remotely.
HTTP (Hypertext Transfer Protocol): HTTP is an application layer protocol that specifies what kind of messages a client may send to a server and what kind of response it gets.

TCP (Transmission Control Protocol): TCP is a transport protocol specifically designed to provide reliable end-to-end byte streaming over unreliable interconnected networks.
IP (Internet Protocol): IP was designed to improve the scalability of networks. It provides information about various protocols to the transport layer and forms the basis of the Internet.
UDP (User Datagram Protocol): UDP provides a way for applications to send encapsulated IP packets without establishing a connection.
IRC (Internet Relay Chat): IRC is a network chat protocol. It is a multi-user, multi-channel discussion system in which many users can converse or talk privately about a topic within a channel, each with a different nickname.
SSH (Secure Shell): SSH is a protocol used for secure remote login and other secure network services on unsecured networks.
Management Protocols
Network devices are governed by management protocols that help supervise and solve network problems. These protocols are vital in monitoring and sorting out these network issues. As far as setting up secure connections go, two mainstream management protocols are:
SNMP (Simple Network Management Protocol): SNMP enables network administrators to manage network performance, identify and resolve network problems, and plan for network growth.

ICMP (Internet Control Message Protocol): ICMP belongs to the network layer protocol, which is mainly used to transfer control information between hosts and routers, including reporting errors, exchanging restricted control and status information.
Security Protocols
Security Protocols are particularly crucial for remote areas with a greater risk of the data being intercepted. We should consider the following security measures:
IPsec (Internet Protocol Security): IPSec uses cryptography to protect the security and confidentiality architecture of IP layer communications by encrypting and authenticating packets of the IP protocol to protect the IP protocol's collection of network transport protocols.
SSL (Secure Socket Layer): SSL encrypts all data transmitted after the application layer protocols have communicated, thus ensuring the privacy of the communication.

TLS (Transport Layer Security): TLS is a security protocol designed to provide security and data integrity for Internet communications.
SFTP (Secure File Transfer Protocol): SFTP is a network transfer protocol for data streaming over wired file access, transfer and management functions.
HTTPS (Hypertext Transfer Protocol Secure): HTTPS is a hybrid of HTTP and SSL. It provides authentication and encrypted communication methods, and is widely used for secure and sensitive communications on the World Wide Web, such as transactions and payments.
The Importance of Setting up a Secure Network Connection at a Remote Site
In our increasingly digital world, creating a secure network connection for remote locations is not merely about building safeguards - it's a necessity.
Reduce the Risk of Cyberattacks
A secure network connection acts like a robust shield, significantly reducing the odds of remote sites becoming victims of these attacks.

Protect Remote Devices
Securing your remote network is like making sure you've locked your front door. It keeps your gadgets safe from risky stuff, like damaging software, viruses, and folks trying to sneak in without permission.
Ensure the Security of Confidential Information
One should always keep personal information and delicate company data off-limits. A solid network safeguard guarantees this, working tirelessly to shield these specifics.
Increase Employee Productivity without Risk
With secure networks, employees can work efficiently with eased minds, assured that they're not compromising security. It gives them the mental peace to focus entirely on their tasks rather than stressing over potential cyber threats.

Avoid Data Loss
Experiencing a data loss can be truly devastating, whether you're a private individual or managing a business. Just imagine secure networks as a protective shield for your invaluable information. It reduces the risk of losing critical data due to unforeseen threats such as cyber-attacks or standard system failures. It's akin to keeping a backup of your treasured memories; a secure network safeguards your data, giving you peace of mind.
Best Practices - Choosing More Secure Remote Access Software
In the professional world we live in today, safe and secure remote access software isn't just a luxury; it's a necessity. It provides smooth, uninterrupted connectivity and also protects your precious data. Amidst numerous such tools, AirDroid Remote Support shines.
It comes loaded with top-notch security features and offers many benefits to meet all your remote access needs. At AirDroid Remote Support, your security is our topmost priority. We seamlessly grant access to your mobile devices while keeping your data safe. With fantastic features, including end-to-end encryption, we ensure all information shared between your devices stays private and protected.
AirDroid Remote Support provides security policies for Android and iOS devices, such as customizable remote control and file transfer service options, the ability to set up blockers to prevent unauthorized external access to an organization's devices, and the ability to enable a dynamic 9-bit connection code to protect customer privacy and avoid unwanted interruptions.

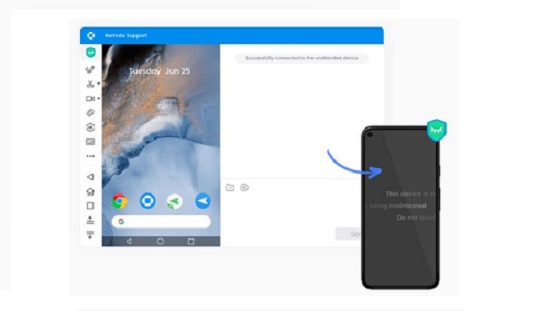
Moreover, it also has a black screen mode when remotely controlling an Android device. Black Screen Mode is a privacy-centric technology, which enables IT admins to hide the screen image of the remote device during the remote control session and a hint saying "This device is under maintenance" will be shown. This will ensure your sensitive data stay private as well as a smooth remote operation for your IT admins.
Conclusion
As our world becomes increasingly interconnected, it has never been more critical to establish a secure network connection at a remote site. It is vital for maintaining the safety of our personal and professional online spaces.
By shielding our devices from far and wide, we can fend off online threats, preserve our data privacy, prevent loss, and boost productivity. Essentially, all these key areas hinge on having a solid, secure network in place.
AirDroid Remote Support is an exceptional, highly secure remote access software. It perfectly strikes a balance between robust security features and ease of use, which makes it a favored choice for an array of remote access needs.






Leave a Reply.